The GRU, Military Unit 44388, obtains and processes intelligence from multiple disciplines, including IMINT, SATINT and, of course OSINT, with information needs linked to the military, political, technological, economic and ecological/energy fields ([1]). It was already indicated in the article dedicated to the GRU, within the series on the Russian Cyberintelligence Community, that the Sixth Directorate of the GRU has historically had the SIGINT (COMINT and ELINT) attributions of the Service. An excellent description of these attributions can be found in [2]; in the image, the historical structure of the GRU:
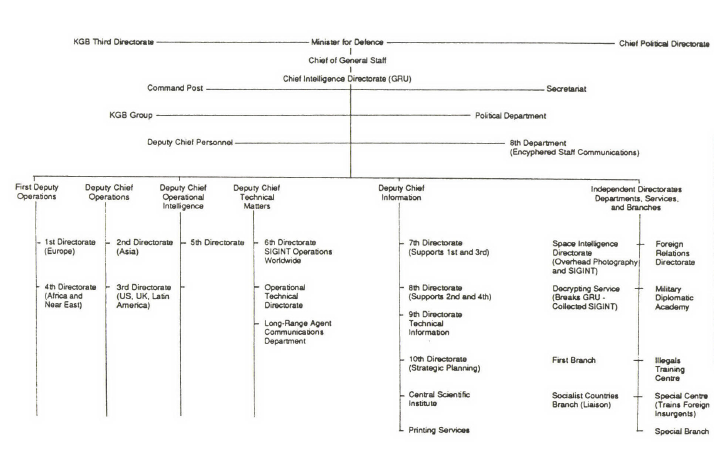
The Sixth Directorate, which reports directly to the Service’s Deputy Director for Technical Affairs, was divided into four divisions
- COMINT,coordinating all the COMINT activities of the GRU and its Transmission Regiments and also responsible for the interception network of the Service.
- ELINT, similar to the previous one but for non-COMINT signal intelligence (ELINT and perhaps TELINT).
- Technical Support, the branch responsible for the operation and maintenance of the GRU’s interception capabilities around the world, from those located in embassies or consulates to large stations such as Lourdes (Cuba).
- SIGINT monitoring, operating and reporting to the Service Command Post, in 24 × 7, to monitor the military situation worldwide, especially in the USA.
In addition to the structure of the Sixth Directorate, the GRU has other capabilities related to signal intelligence, from the Service Command Post to the Spacial Intelligence Department. We could even talk about the theft of cryptographic material via HUMINT, but of all these additional capabilities, the following are especially relevant – due their proximity to the cyber environment:
- Decryption Service, which receives and decrypts communications acquired by the GRU worldwide, especially from the Technical Support branch, and which is located in Komsomolskiy Prospekt (Moscow) ([3]). Contrary to what appears in some publications, this service does not depend on the Sixth Directorate, but is directly subordinated to the Director of the GRU.
- Special Processing Center of the GRU (Spetsialniy Tsentr), which, from its headquarters in the outskirts of Moscow, processes the enormous volume of communications provided by the Sixth Directorate through Soviet systems ([4]).
- Central Scientific Research Institute, in Moscow, responsible for the design of SIGINT equipment for the GRU ([5]).
- Operational Technical Directorate, of the General Directorate of Technical Affairs, independent from the Sixth Directorate since 1968 and which is responsible for research, development and procurement of the SIGINT hardware of the GRU.
Finally, and outside the GRU structure but coordinated and supported by it, each of the military land or naval areas of the former USSR had its own Intelligence Directorate (RU), and at the same time a department -the Fifth Department- was established within each of them, responsible for radioelectronic recognition. This Fifth Department was in charge of analysing the signal intelligence collected by the Transmission Regiments and their stations in each of these military zones. Operational intelligence was developed in these RU, so its coordination depended on both the Sixth Directorate of the GRU and the Fifth Directorate of the Service.
References
[1] Roland Heickerö. Emerging Cyber Threats and Russian Views on Information Warfare and Information Operations. FOI. Swedish Defence Research Agency. March, 2010.
[2] Desmond Ball. Soviet Signals Intelligence (SIGINT). Canberra papers on strategy and defence, no. 47. Strategic and Defense Studies Centre. Research School of Pacific Studies. The Australian National University. Canberra, 1989.
[3] Desmond Ball, Robert Windrem. Soviet signals intelligence (Sigint): Organization and management. Intelligence and National Security. Volumen 4, Issue 4. 1989.
[4] Karl Maria Michal de Leew, Jan Bergstra (Ed.). The History of Information Security: A Comprehensive Handbook. Elsevier. August, 2007.
[5] Jeffrey Carr. Inside Cyber Warfare: Mapping the Cyber Underworld. 2nd edition. Ed. O’Reilly, 2011).
