Have you ever thought that radiographs were just JPG images? Do you remember hearing the name DICOM? In this article we expect to resolve all your doubts about the protocol for sending medical images and show you its implications for cybersecurity.
Quick introduction to DICOM

Medical images that are transmitted within hospitals, such as X-rays or ultrasounds, are not in the common image formats, but are in DICOM (Digital Imaging and Communications in Medicine) format. However, they can be converted to JPG or PNG.
Although at first glance it looks like a simple image format, DICOM is much more: it is the standard for transmission, storage, retrieval, printing, processing and visualization of medical images and their information. Thanks to the implementation of this standard, technology in the health field was revolutionized, replacing physical radiographs with digital radiographs with all the implied data. Today, DICOM is recognized as the ISO 12052 standard.
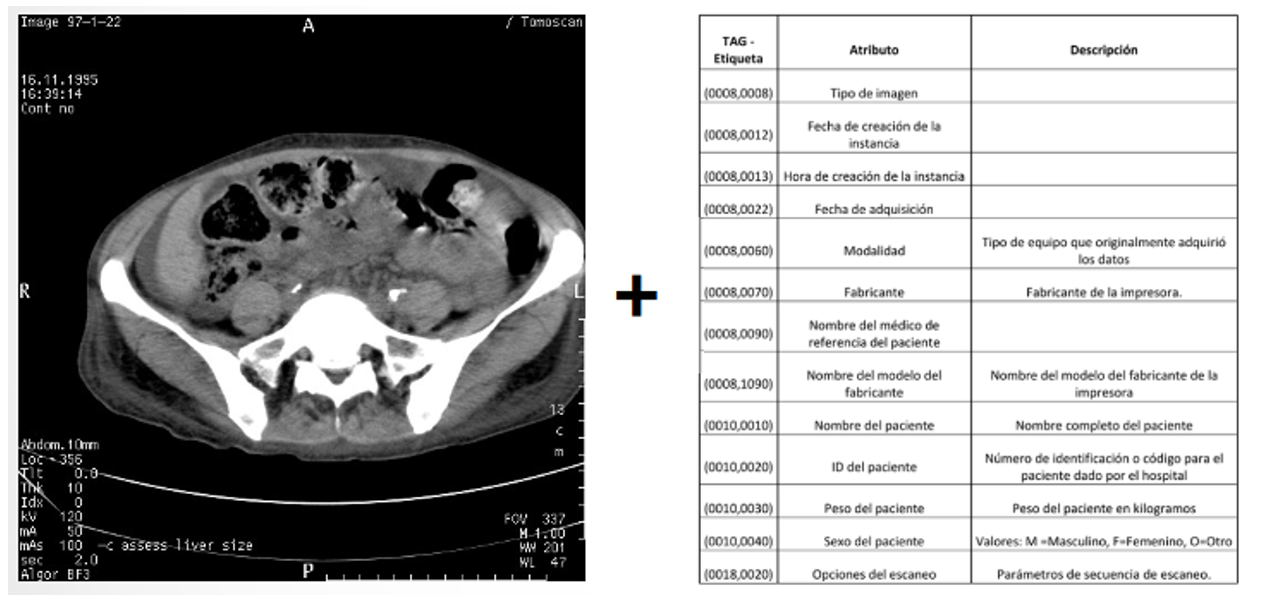
As we have previously mentioned, DICOM is a medical image storage format. The reason why DICOM is used and not other formats is that it not only stores the image taken, but also the patient data, as shown in Figure 2 below.
Some of the metadata found are the type of image, date of creation, modality (the equipment that acquired the data), doctor’s name, patient’s name, patient’s ID and patient’s weight, among others.
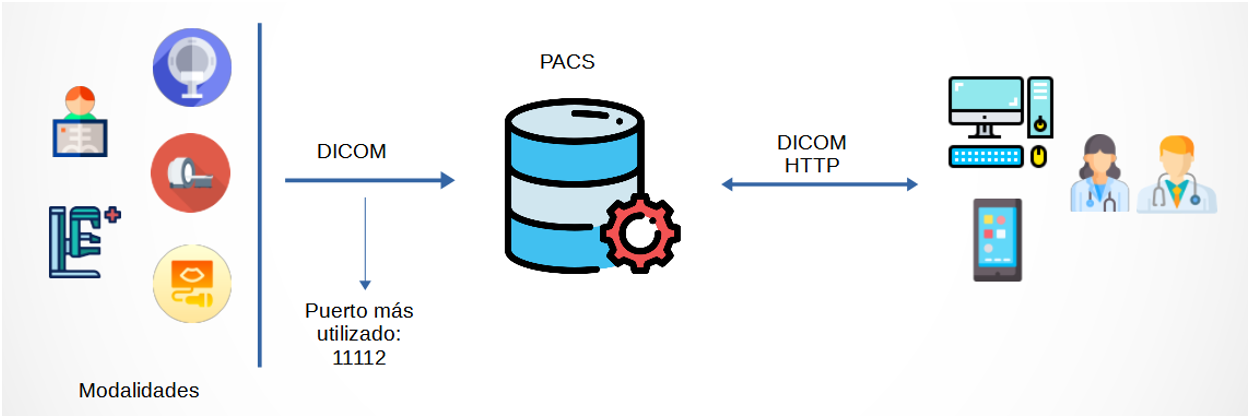
To understand the transmission of DICOM images within a hospital, specifically in a radiology or medical imaging unit, Figure 3 shows a diagram of DICOM communication and its component elements to better understand this entire ecosystem.
To begin with, we have the modalities. The modalities are the equipment used for the acquisition of medical images such as ultrasound, mammography, magnetic resonance imaging, CAT scans, and X-rays, among others. When acquiring the image through these modalities, they are sent through the DICOM protocol (usually port 11112) to the PACS (Picture Archiving and Communication System), which is the database where all the images that are sent in the system are stored. This server can be accessed through DICOM requests from other servers or through web-enabled interfaces for physicians or radiologists.
Main vulnerabilities in DICOM
Once we have learned the basic concepts about DICOM and its operation, it is essential to know what implications this standard has today in the cybersecurity of health systems.
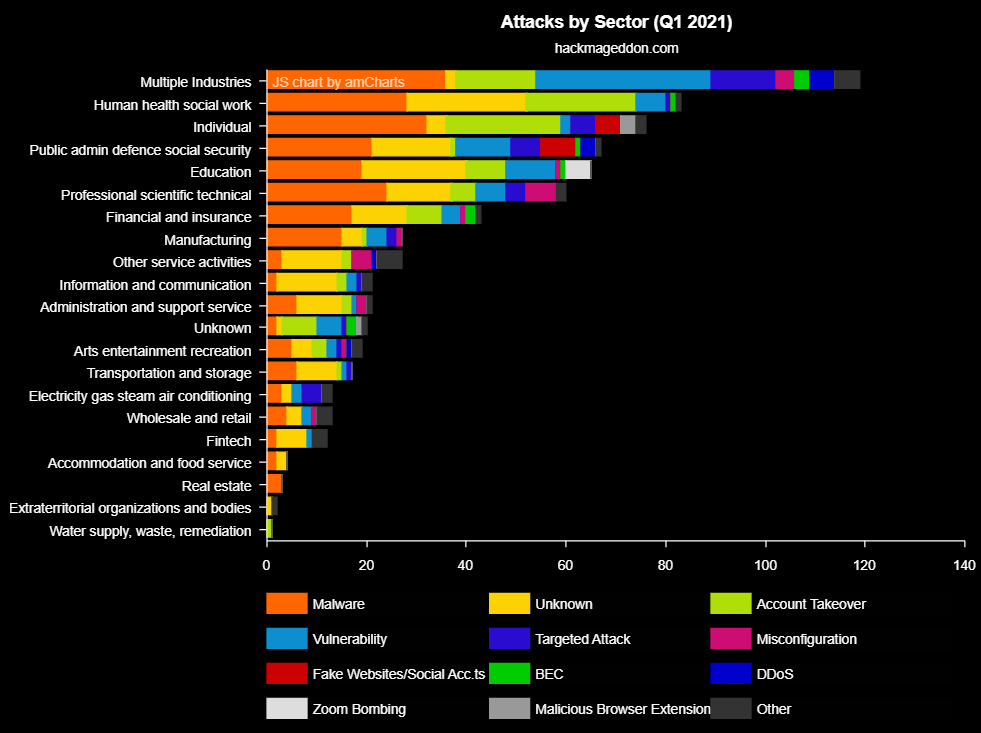
The number of cyberattacks on hospitals is growing, with the health sector being the second most attacked , as shown in Figure 4. As a consequence, data breaches in hospitals are becoming more common, affecting thousands of patients. To avoid these attacks received, we will have to look for the main vulnerabilities of hospitals to solve them.
So how can DICOM configurations affect hospital data breaches? In this case, we are going to focus on two specific situations and how an attacker, taking advantage of these vulnerabilities, could have quick access to hospital or health center data.
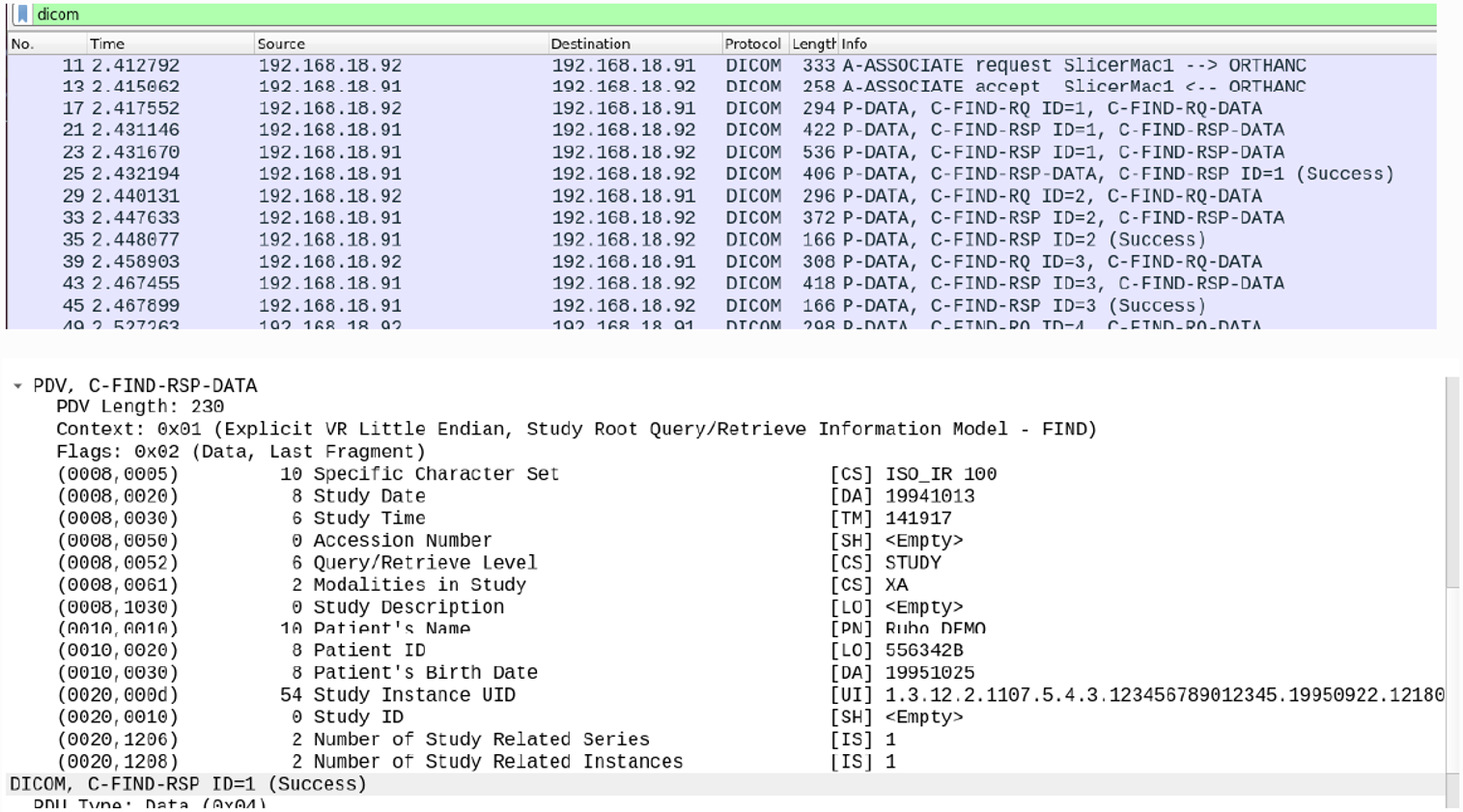
In the first situation we analyzed the hospital network and found images transmitted using the DICOM protocol. This protocol is usually not encrypted and when analyzing the packets, we find the patient data in plain text. Figure 5 shows a Wireshark capture where the metadata of the sent image is displayed.
In the second case, we ran a search on Shodan.io finding open ports and medical imaging web servers. When trying to access the web servers, we realize that they do not ask for credentials and that we can view private images of patients and acquire their data without any type of restriction.
These small examples show us the lack of security that we find today in the health sector when using the DICOM protocol and in the transmission of medical images. Some examples that are easy to implement and without the need to write a single line of code.
Countermeasures
Cybersecurity in hospitals is of vital importance, as is dealing with patient data responsibly. What can we do to protect a healthcare environment? Once we know these dangers, the important thing is to implement countermeasures to protect ourselves:
- Use strong passwords on medical equipment and web servers.
- Encrypt DICOM communications.
- Perform periodic audits on the medical network.
- Monitor DICOM requests and accesses through the web interface.
With the implementation of these measures, we are one step closer to turning hospitals into cybersecure places.
References
- [1]“DICOM.” https://www.dicomstandard.org/ (accessed Feb. 28, 2022).
- [2]“HIPAA Breach News,” HIPAA Journal. https://www.hipaajournal.com/category/hipaa-breach-news/ (accessed Feb. 28, 2022).
- [3]14:00-17:00, “ISO 12052:2017,” ISO. https://www.iso.org/cms/render/live/en/sites/isoorg/contents/data/standard/07/29/72941.html (accessed Feb. 28, 2022).
- [4]“January 2022 Healthcare Data Breach Report,” HIPAA Journal, Feb. 22, 2022. https://www.hipaajournal.com/january-2022-healthcare-data-breach-report/ (accessed Feb. 28, 2022).
- [5]“Yearly Archives: 2021,” HACKMAGEDDON. https://www.hackmageddon.com/2021/12/23/november-2021-cyber-attack-statistics/ (accessed Feb. 28, 2022).
