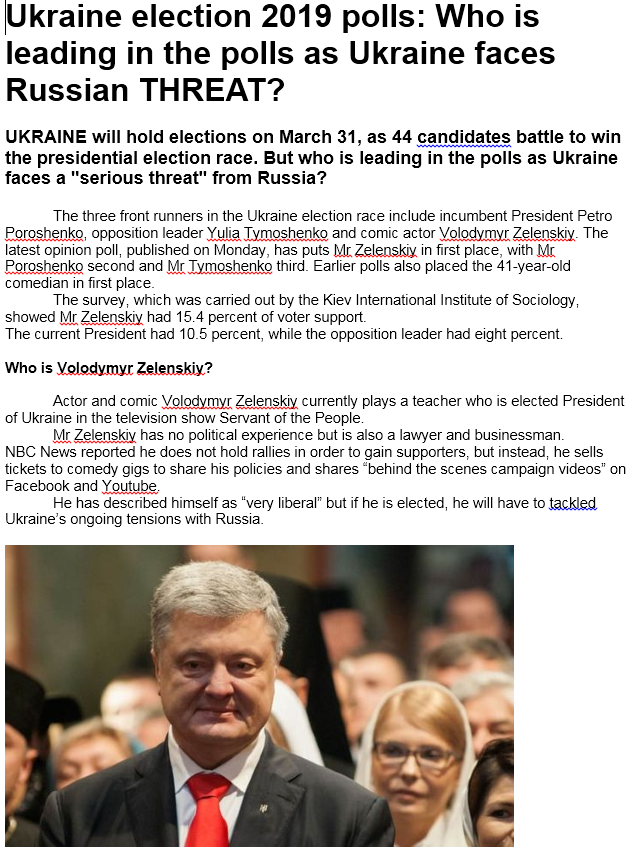
In this work, we have analyzed mainly the structure, targets and TTP of the GRU in the cyber field, based on the information brought to light during 2018 and which allowed to obtain a detailed knowledge of the Service and its activities, not only to intelligence services, but also to poor analysts like us who do not have all the capabilities that a state can have. With what we know, even analyzing public sources, we have access to information that in some cases should be considered sensitive and that, without a doubt, is being -or has been- analyzed by services from all over the world, starting with Russia itself.
The fact that we know the GRU better than a year ago does not mean that now it is a worse service than before; it will remain part of the elite, fulfilling its missions and acting “in any part of the world where it is required“, said one of its former directors. The GRU, or APT28, or whatever you want to name it, will continue to be a very important player in the cyber field and, of course, in the non-cyber realm. We all make mistakes, and the GRU made them on that occasion – and they were published. However, it is more of a concern in certain circles that the GRU failed in its operations than to have leaked the identities or modus operandi of some of its members.

 Apparently, Unit 74455 is linked to operations of disinformation, influence, propaganda … which would reconfirm the broad concept of information warfare of the Russian military doctrine. We have already referred to it repeatedly, and to the mixture of the purely technical field with the psychological field (dezinformatsiya, spetspropaganda, kompromat, etc.).
Apparently, Unit 74455 is linked to operations of disinformation, influence, propaganda … which would reconfirm the broad concept of information warfare of the Russian military doctrine. We have already referred to it repeatedly, and to the mixture of the purely technical field with the psychological field (dezinformatsiya, spetspropaganda, kompromat, etc.).