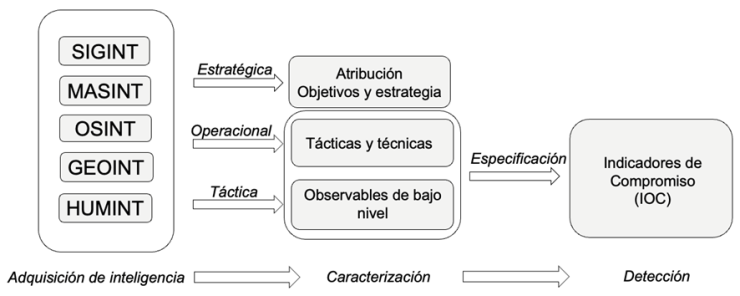
In today’s cybersecurity landscape, the concept of Threat Hunting or the proactive pursuit of cyber threats begins merely as soon as an actor establishes their foothold in an organization, limiting the detection capabilities and overall understanding of a campaign that a hunter may have regarding the offensive capabilities of their adversary. In this context, I propose and intend to tackle these challenges with two main tactics that hunters can employ to disrupt the offensive operations of state actors and non-state actors more effectively: Horizontal Hunting and Vertical Hunting, while integrating elements of persistent engagement to enhance visibility.
Initially, as is usual in hypothesis-driven Threat Hunting, we formulate hypotheses based on intelligence feeds to conduct proactive searches within our environment. However, this approach often lacks precision in both operational capabilities and strategic insight into the adversary’s intentions. This can be attributed to various factors, including:
- Limited intelligence collection capabilities
- Technical expertise of both hunters and Threat Intelligence teams
- Uncertainty about the proactivity of the hunting team
- Urgency to deploy detection capabilities (which may not always be effective) or publish articles by the Threat Intelligence team.