Two-step authentication is a protection approach widely known among cyber security people but it is not that known among regular users. This article aims to teach everybody about it, as domestic user accounts are more and more targeted by hackers.
We need a unique user ID on the domain in order to access any service on it, this could be a nickname, email address, identity card number, NI number, for example. This information identifies the user, but since it is not secret and anyone could know it, it does not confirm that the user is who they claim to be.
So the user needs to provide something else within the user ID to make the system trust him/her and get access. There are three kinds of authentication factors:
- Something the user knows: password, pin, passphrase, etc.
- Something the user has: pendrive, security key, smartcard, key generator, etc.
- Something unique to the user: fingerprint, retinal pattern, DNA sequence, signature, face, voice or other biometric identifier, etc.
Traditional authenticating methods, well known by everybody, involve the use of a unique user ID within a password that is only known by the user, but what happens if the password is intercepted or stolen by another user? You will not know this on your own.
Two-step authentication is also known as 2FA or TFA and involves the using of two factors of those already stated: the most typical scenario is the time-based one-time passwords. Users must provide his/her password within a one-time key, which is valid for a few seconds and is usually generated on a mobile phone. The mobile phone must be previously configured by introducing a seed for key generating. A hacker might intercept the user password and temporary key, but this would be useless since this is a time-based one-time key. A hacker would need the key generating seed instead, but it never leaves the computer, so a man-in-the-middle attack does not have any effect.
There are scenarios where the temporary key is generated on the server side and it is sent to the user with a text message or email.
You might think using temporary keys are not comfortable enough, if this is your case you can purchase one of the security keys available on the Internet. They are USB drives which contain a certificate and must be plugged into a USB socket anytime you authenticate by entering username and password.
This is a very good technique to harden security and make things tough for hackers but, however this is not 100% secure as security usually breaks by the weakest link: the user. Kevin Mitnick says in his biography: “Gosh in the wires”, that he managed to convince a network operator of a very important company to skip this protection by telling him he would be an employee who forgot his smartcard.
You are probably eager to use Two-step authentication at this point, and you are wondering: Where can I use it?
It is available in more and more services, but unfortunately not yet in all of them. Some of these services are Google, Dropbox, Facebook, PayPal, eBay and Twitter. You can find a table of services that offer this kind of authentication and how they implement it in https://twofactorauth.org/.
Summarizing, Two-step authentication:
- Reduces or removes account stealing by phishing.
- Removes account stealing by man-in-the-middle attacks.
- It makes impersonalization tougher.
- It gives you something to talk to your friends about when they ask you: What is that weird, geeky pendrive on your keyring? And then you can entertain them by telling them about what you’ve just read, or even better, write your own article!
You can find some valuable information regarding MFA in this extenal resource: https://pixelprivacy.com/resources/two-factor-authentication/.


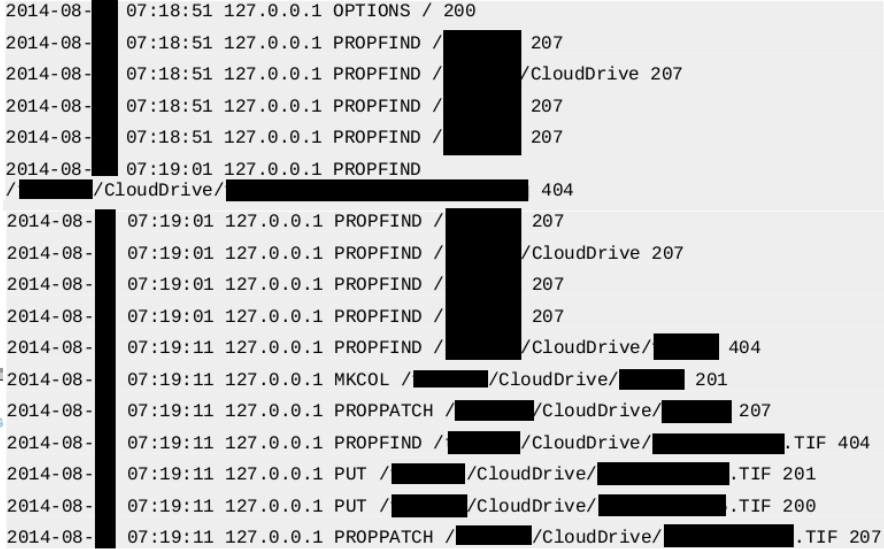
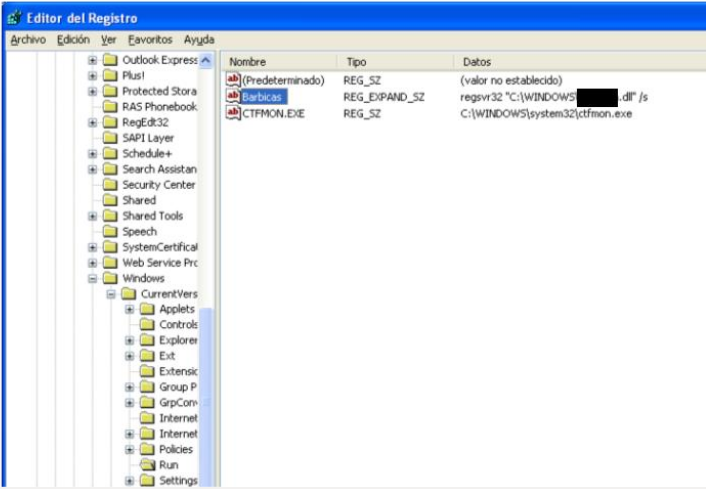
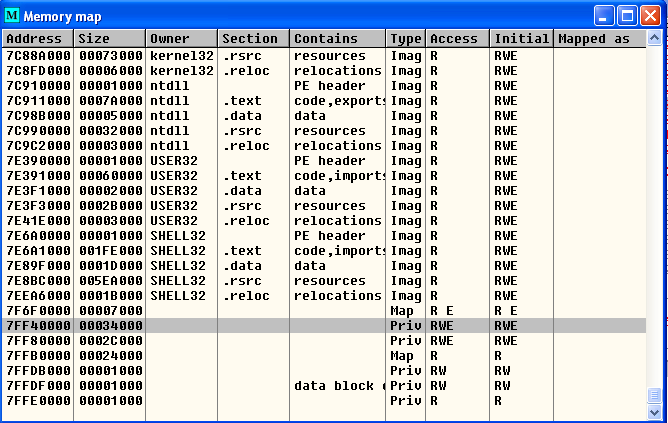
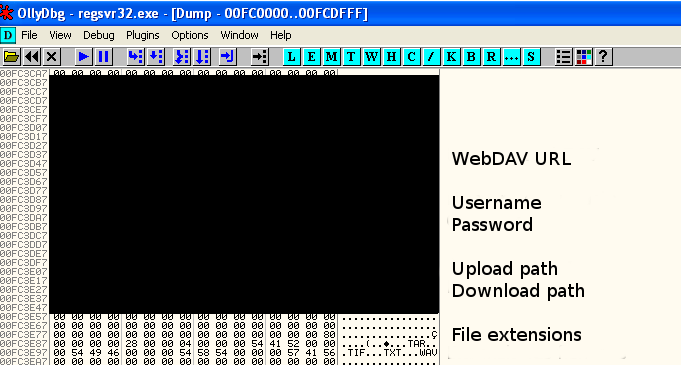
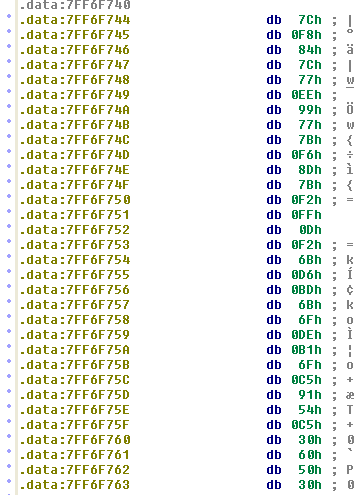
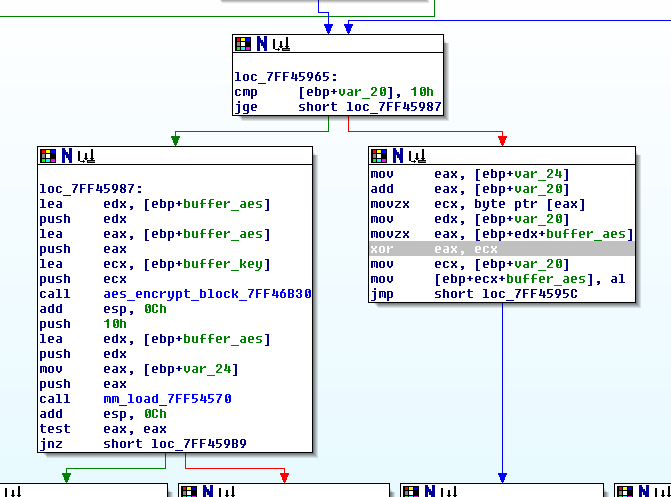
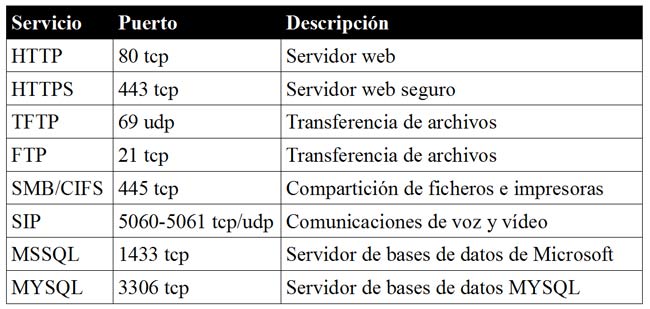
 In the world of advanced persistent threats or APTs, techniques used by malware artifacts play an important role in communication and exfiltering information via C2s (Command & Control). In this sense, there are as many as there are protocols and services and an attacker can draw from his/her imagination. As just small examples of “tricks” for disguising illegitimate traffic as apparently normal information are:
In the world of advanced persistent threats or APTs, techniques used by malware artifacts play an important role in communication and exfiltering information via C2s (Command & Control). In this sense, there are as many as there are protocols and services and an attacker can draw from his/her imagination. As just small examples of “tricks” for disguising illegitimate traffic as apparently normal information are: The other day, a friend told me that he was at work, having a coffee; one of those from the machine that are now standard in most companies, you know, a Nespresso. When he pushed the button something strange happened and the machine got stuck in a loop —they get more and more like computers— and the lights were flashing. He turned it off and then on again (my friend is a computer engineer) and everything worked out fine —just like a computer— and he could satisfy his need for caffeine.
The other day, a friend told me that he was at work, having a coffee; one of those from the machine that are now standard in most companies, you know, a Nespresso. When he pushed the button something strange happened and the machine got stuck in a loop —they get more and more like computers— and the lights were flashing. He turned it off and then on again (my friend is a computer engineer) and everything worked out fine —just like a computer— and he could satisfy his need for caffeine.