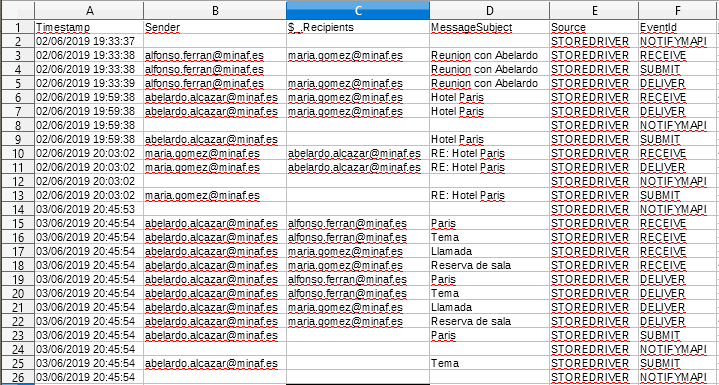
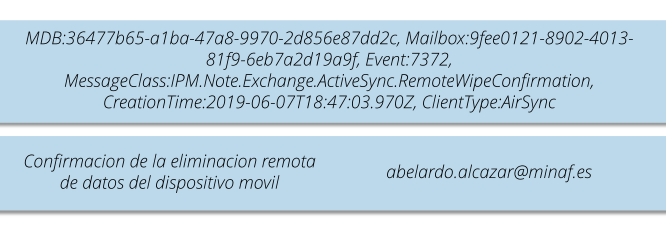
In the previous article, we saw how the attackers had been monitoring and manipulating the MINAF CEO’s email at will … and that they had done it through OWA (Outlook Web Access), the Exchange webmail.
To know how these logs work, we have to see how Exchange works. If we simplify it a lot, Exchange has two main components: CAS (Client Access Server) and DAG (Database Availability Group), which would be roughly equivalent to a web server and the database of a web application.
MORE