(Editor’s note: this post was originally published in the Spanish version of Security Art Work on 4th July 2019)
Today we publish the second of three articles courtesy of Jorge Garcia on the importance of server bastioning. You can find the first one here: The importance of server hardening – I
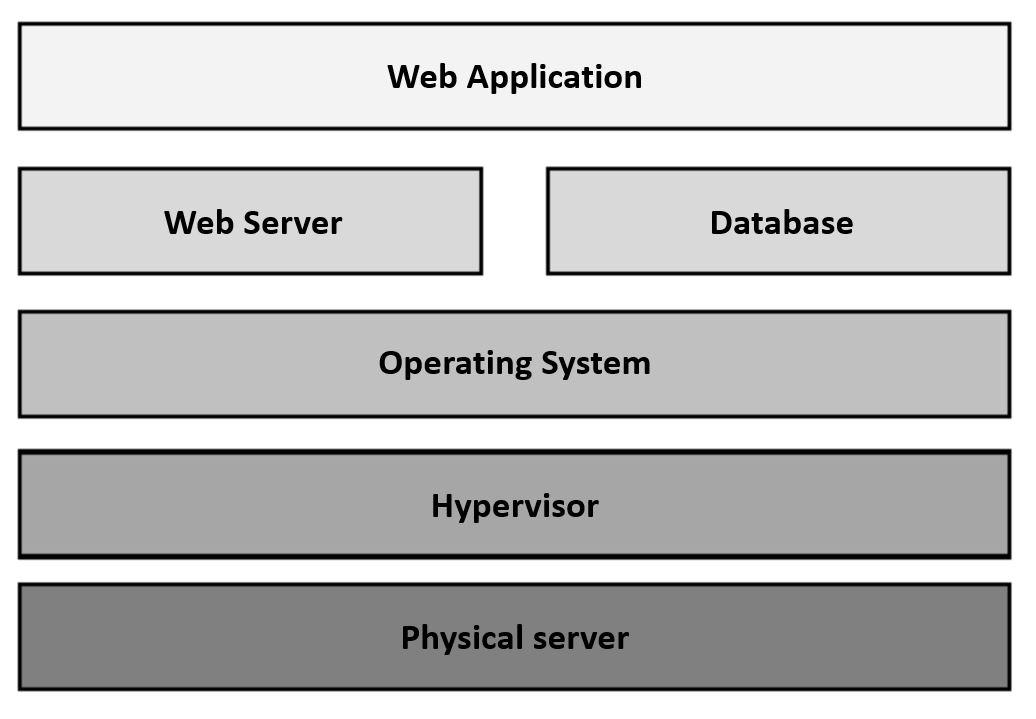
All right, we have the mission of hosting an online commerce web application and offering it to the world on a server that we own. Our goal is to make it as impregnable as possible at all levels. Since it is a web application, it is foreseeable that the main attack entry vector is through vulnerabilities of the application itself. Really, let’s not fool ourselves, all CMS are sure candidates for severe vulnerabilities. The scheme of how the platform will be organized is the usual one in a virtual server:
Therefore, the issue is to choose a CMS with these premises:
- That it is actively developed and supported by a large community of developers or by a large company. This ensures that when a vulnerability is published, it is quickly corrected.
- That the installed CMS is the last available version of a branch that has support, and that it is expected to continue having it for quite some time. Do not forget that, since we do not have a development environment at home, updates or migrations mean a loss of service which in turn means potential loss of money.
- That it is compatible with the operating system of the server that we have. A consideration that is obvious but important.
- May the history of critical vulnerabilities be as low as possible. A CMS that is actively developed and has good support but that on average finds a critical vulnerability every week is not viable to maintain or safe to use.