For several weeks we have been detecting a new variant of malware for Linux and IoT architectures from the malware laboratory of S2 Grupo, registered for the first time on the VirusTotal platform on October 18, which we have called Linux.Helios, due to the name of certain functions present in the sample.

We emphasize that the main antivirus signatures do not unanimously classify this sample: they range from ELF.DDoS to Tsunami, through Gafgyt or Mirai.
[Read more…]

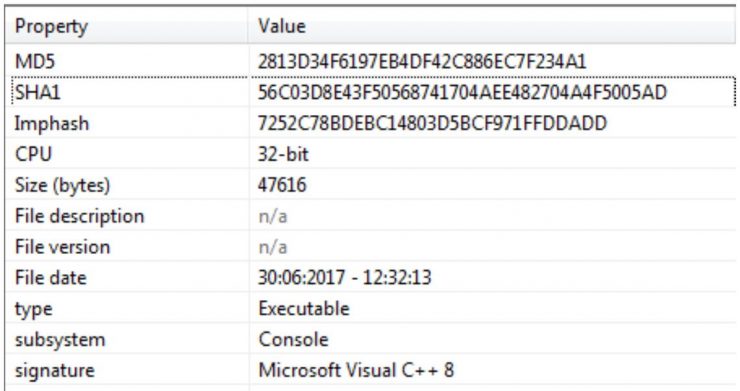
 From the malware lab of S2 Grupo we have been monitoring the movements of a Trojan known as Trickbot. Its relationship with Dyre, another older Trojan with which it shares many design features, and the speed at which it evolves, has captured our interest ever since we saw the first samples.
From the malware lab of S2 Grupo we have been monitoring the movements of a Trojan known as Trickbot. Its relationship with Dyre, another older Trojan with which it shares many design features, and the speed at which it evolves, has captured our interest ever since we saw the first samples. I do not think it necessary to mention what the SSH (Secure Socket Shell) protocol is, since it would be really difficult to live without it today. Therefore, SSH is considered globally as the “mega” indispensable tool for any administration work. Among the advantages of its use we can find: secure access to remote machines, access to services on other machines by creating direct or reverse tunnels, creation of proxy socks, creation of secure channels for the encapsulation of traffic from unsecured applications … etc.
I do not think it necessary to mention what the SSH (Secure Socket Shell) protocol is, since it would be really difficult to live without it today. Therefore, SSH is considered globally as the “mega” indispensable tool for any administration work. Among the advantages of its use we can find: secure access to remote machines, access to services on other machines by creating direct or reverse tunnels, creation of proxy socks, creation of secure channels for the encapsulation of traffic from unsecured applications … etc. The widespread use of devices connected to the network, such as cars, medical equipment, industrial controllers (PLCs), appliances, etc., has brought with it a new and extremely vulnerable landscape.
The widespread use of devices connected to the network, such as cars, medical equipment, industrial controllers (PLCs), appliances, etc., has brought with it a new and extremely vulnerable landscape.