In the wake of all the uproar that there are these days around the metadata in Spain, I have been reviewing various tools of PDF metadata deletion. In principle, the tools analyzed work on GNU/Linux systems, but that does not mean that some may not work on other systems.
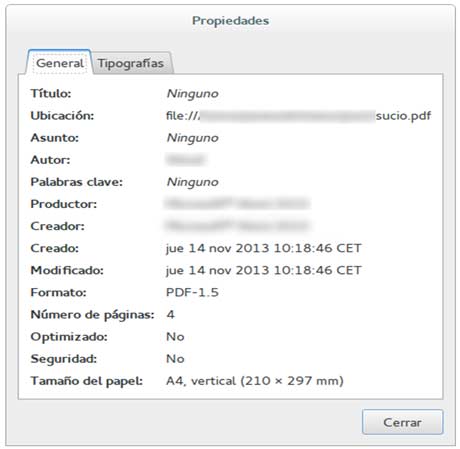
I started from a PDF created by myself. As you can see in the following image, it contains metadata (screenshot in Spanish, but I guess you get the idea):