The RHME2 is an embedded CTF running on the Arduino Nano board. The participants have to prove their skills both on software and hardware exploitation. Buffer overflows, ROP, C++ exploitation, cryptoanalysis, side channel analysis, fault injection… and all these in an AVR architecture!
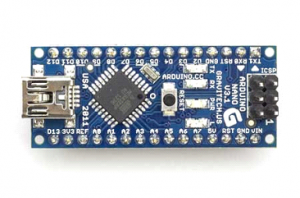
The pre-registration for the 2nd edition of the RHME challenge is open now. Pre-register now and get your Arduino Nano with the challenges. The boards will be sent for free at the end of October and the CTF will officially start on November 1st. There is a limit of 500 boards and the first to come, the first to ship!
More information at http://rhme.riscure.com
Search Results for: CTF
Registration for the RHME2 embedded CTF is open
So you want to go into cybersecurity…

This post has been prepared with the invaluable (and necessary) help of Maite Moreno (@mmorenog) and the cybersecurity team of S2 Grupo.
One of the good things that Information Security shares with other IT disciplines is the wide variety of training resources available, both free and for tight budgets.
Without a large financial investment, anyone with time and desire (and a minimum knowledge of technical knowledge, for which there is another large number of resources that we will not cover here) can be trained from practically zero to expert levels in practically any area of cybersecurity.
Below are some of the resources available on the Internet for free or for a reduced cost, bearing in mind that:
- This list is not intended to be exhaustive. Feel free to comment on any content you think is missing and we will add it as soon as we can.
- Some platforms have a freemium approach, combining free content and functionalities with paid ones.
- Although the less technical areas of Information Security such as GRC are less (very little) represented in the list, the more generalist training sites include courses on data protection, control frameworks, risk management, etc.
- Most of the courses are in English, so a minimum level is required to understand instructions and texts. This level is essential nowadays in the field of information technology.
- Blogs, vblogs and podcasts on Information Security are left out, but there are plenty of extremely useful resources. This includes the thousands of webinars on every conceivable topic.
- Nor have we included more general platforms such as edX or Coursera, which nonetheless contain many courses from prestigious universities and organizations.
- Finally, we have not included courses from the device manufacturers, software or cloud providers, which in some cases are free, and which sometimes also provide free versions (with limitations) of their products. AWS, Tenable or Splunk come to mind, but there are many others.
Ransomware ate my network (I)
Series entries: First part, Second part, Third part, Fourth part, Fifth part
Note 1: This series of posts is a narration of a forensic analysis of a totally fictional incident response case study (but told, we hope, in a didactic and humorous way). If you want a version with the same technical dose but with less narrative, you can check the video of the talk that the author gave at the XIV CCN-CERT STIC Conference, or take a look at the slides of the presentation.
Note 2: These posts reveal a forensic analysis workshop encompassed within the incident response. There will be some things that could be done more efficiently and elegantly, but the idea was to make them simple so that they are easy to understand. And like any practical workshop, you can take advantage of it in several ways: you can download from LORETO the evidence already worked to follow the case step by step, you can download the raw evidence to do your own investigation… or you can play the CTF DFIR that we have prepared and that will be unfolding the case as you respond to the various challenges.
There are few good months for cybersecurity in a Public Administration, and November is not one of them: projects must be closed, status reports must be made, and it is necessary to make sure that the entire budget is executed (and justified with the corresponding invoices).
Angela de la Guarda, CISO of the MINAF (Ministerio of Alegría y Felicidad, Joy and Happiness in English) has not had a particularly happy year: the pandemic forced the deployment of teleworking for a large part of the personnel, which caused a significant overload on all ICT personnel… and even more so on her and her team, responsible for ensuring the security of all systems.
To make things worse, in the usual restructuring with each change of government, the MINAF has been entrusted with the mission of “unifying all state agencies with skills on joy and happiness.” This has led to the absorption of several entities of different sizes, among which the FFP (Federation of Patron Festivities, in charge of managing all town festivals in Spain) stands out. The FFP has, so to speak… a rather relaxed view of cybersecurity, which made assimilation highly conflictive. In the end, the upper echelons have ruled, and the MINAF finally absorbed the FFP.
It’s 5:00 p.m., and Angela is checking emails to finish the first of a week full of reports and go home, when Salvador Bendito (MINAF security analyst) calls her on her mobile: “Boss, we have a very serious problem. One of the canaries has jumped: we are losing the goalkeepers. All of them”.
[Read more…]How they swindle $100K without blinking an eye – Forensic Analysis of a BEC (Business Email Compromise) (I)
Note 0: This series of articles is a description (hopefully entertaining) of the case study (fictional, beware) that Maite Moreno and myself presented at the c1b3rwall digital security and cyber-intelligence conference, organized by the Spanish National Police. If you want more information on CEO scams you can check the (in Spanish) slides of our talk,full of data as well as a real case that we researched.
Note 1: We emphasize that this case is fictitious. However, the techniques and procedures used are identical to those used by the attackers, with the difference that we offer evidence to study them in detail. Note that he investigation could have been done more efficiently, but we wanted to show some interesting elements and techniques to deep into Exchange, hence the steps taken.
Note 2: Before starting the case study… you can play it! We have set up an open-access forensic CTF you can use to practice your technical skills. Try it before reading these articles (recommended), or later to reinforce concepts. If you only want the raw evidence, you can get them here. You can also download the step-by-step guide with all the tools and evidence needed for each step of the articles, perfecto to continue with the slides.
Those of us who work in incident response and forensics would love want attackers to warn us before doing their wrongdoing. We want it together with the Lamborghini, the yacht and the unicorn with a rainbow in the background, but we get the same response in almost all cases: no f****** way.
“What a pain in the ass it is to have an incident at 14:55 on a Friday,” you would think. There are worse things: a call from your boss at 15h on a Saturday while you are taking a nap: “Grab your incident suitcase, ‘we’re going to party’».
The party consists of about 4 hours of travel from Madrid to Ponferrada, where the headquarters of the MINAF (Minerías Alcázar y Ferrán) is located. MINAF is a mining company that will not ring a bell, but which has a turnover of more than 40 million euros and operates in 12 countries.
[Read more…]Solving ‘heap’ from defcon 2014 qualifier with r2
This article will introduce r2 to resolve a simple CTF from Defcon ’14 using Linux. For those who do not know radare2 is a unix-like reverse engineering framework and commandline tools and the most important thing about it is that it is open source thus we can play with it.
Radare2 gives us the possibility to do reverse engineering and more by free as we will look on this post though we are not going too deeply into the commands. I leave it as an exercise for the reader.
Most people complain about the lack of doc that r2 has but that is far from the truth. Radare has:
