(Please note this post was originally published past 10th January in the Spanish version of SAW but we find it relevant —and couldn’t find time to translate until now— ;)
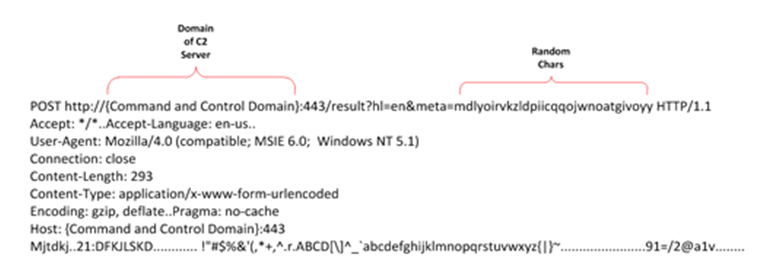
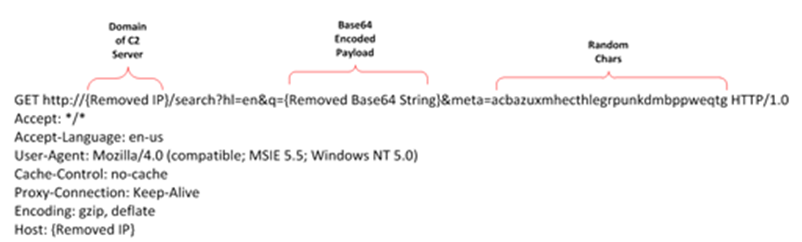
Lately, we are detecting a significant increase of Remote File Inclusion [1] attacks in which the same pattern is repeated in the payload of the attack. In these, the URL of injection used is always the same: http://www.google.es/humans.txt. Although the content of this file is not malicious, the amount and frequency of alerts that are detected show that there is a reconnaissance attacks campaign underway.
The attacking IP addresses are located worldwide (up to 10 countries have been detected, including Spain), which may indicate that one or more botnets are behind this attack. On average, over a period of 10 days, each one of these IP has attacked about 12 targets, generating between 2000 and 5000 alerts each one.