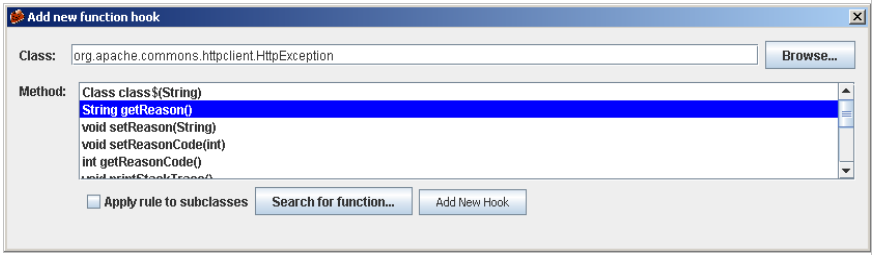
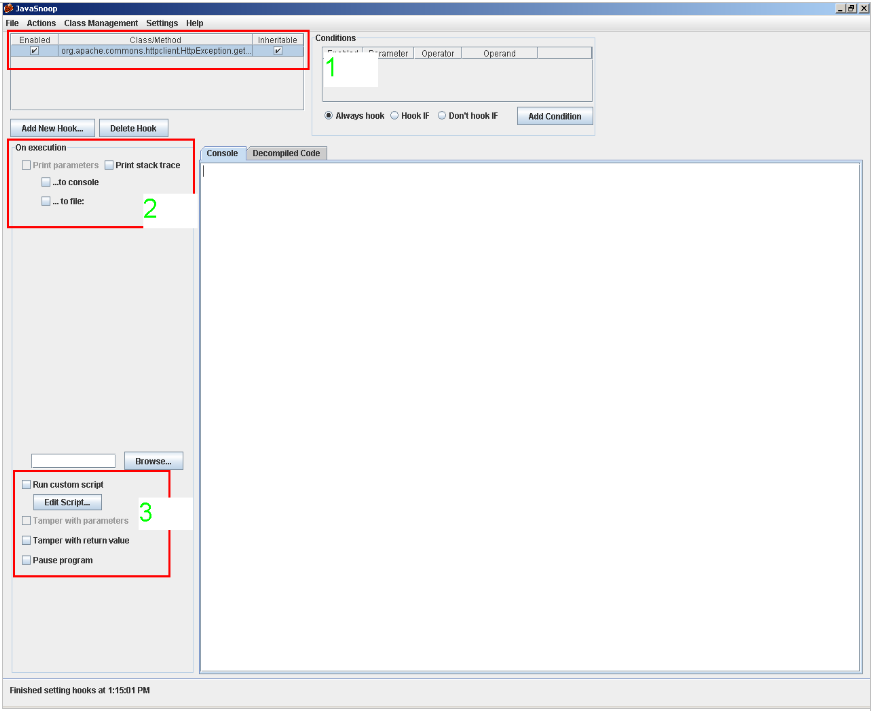
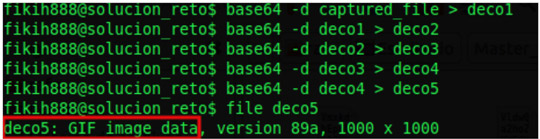
I’m sure we all have sketched a smile when seeing photographs or videos of strange artifacts powered by steam or internal combustion engines. Most of these inventions failed because the technology used didn’t fit the purpose they were meant for. Seen with modern eyes it’s just so naïve to try to fly a plane fitted with a steam engine. However, those inventors were not as dumb as their failure suggests. They were intelligent people (or, let’s say, not less intelligent than average) trying to solve the problems of their time with the technology available.
Steam powered the beginning of industrialization, granting people access to energy at a scale never seen before. This brand new technology lead to an engineering and cultural revolution that paved the way to our modern society. The Industrial Revolution beginnings were times of faith in progress, of unleashed collective optimism. Steam-powered machines were regarded as the key to all kind of engineering problems that remained unsolved so far.