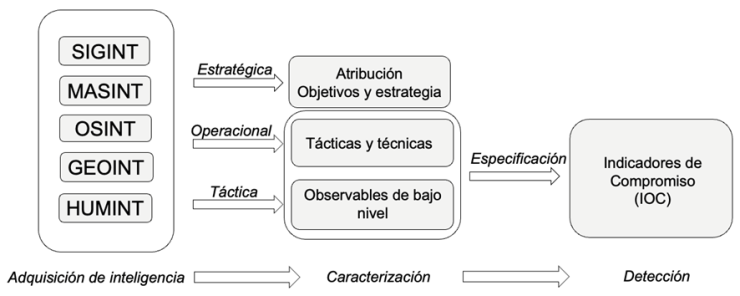
The main units of the Russian GRU engaged in cyberspace operations have been discussed in this blog: from our old posts (from 2018) about unit 26165 and 74455, to the recent rise of unit 29155. All these units have something in common, in addition to their cyberspace capabilities: they have been assigned an APT group name. Military unit 26165 is commonly referred as APT28, while unit 74455 is known as Sandworm Team and unit 29155 is named Ember Bear (please note the mess about APT groups nomenclature, referred in this blog). However, not all GRU units operating on cyberspace have the honor of being assigned an APT group. In this post, unit 54777 is presented, a GRU military unit engaged in PSYOP -also through cyberspace- but, until now, without a particular common name.
Soviet Union, and now Russia, has a long history on disinformation and psychological warfare. In fact, Information Confrontation’s aim is to influence the perception and behavior of the enemy, population, and international community. Psychological warfare has been used since the roots of Soviet intelligence by spymaster and Cheka founder Felix DZERZHINSKI, to the current Ukrainian conflict. Just a fact to highlight the relevance of psychological warfare in modern Russia: Aleksandr Gennadyevich STARUNSKY, a former commander of military unit 54777, was appointed by Vladimir PUTIN to the Scientific Council, under the Security Council of the Russian Federation.
Soviet GRU, and whole Soviet Red Army, considered special propaganda as part of their active measures. Although propaganda was supposed to influence on enemy troops, the Soviet regime used it to strengthen the spirit of its own troops. When Soviet Union collapsed, the Special Propaganda Directorate, responsible for military psychological operations, were transferred into the GRU, and few years later, in 1994, it was established as military unit 54777. This transference was not only a bureaucratic question: it made Russian PSYOP more aggressive than they were during Soviet times. While in Soviet times special propaganda units operated only during military operations, with this transference operations began to be carried out “in peace time and war time”.
Military unit 54777 (VCh 54777, 72nd Special Service Center, 72nd Main Intelligence Information Center -GRITs- or Foreign Information and Communications Service), is still responsible for the GRU’s PSYOP. A detailed description of this unit, together with historical Soviet propaganda efforts and current Russian psychological warfare, can be found on Agentura website and on Aquarium Leaks (Inside the GRU’s Psychological Warfare Program).
Among its most notable operations, unit 54777 has been involved in disinformation campaigns related to the 2014 annexation of Crimea, to the Syrian civil war and to the Ukraine conflict. In peace time, this unit has been involved in propaganda campaigns during elections in Europe and in the United States, as well as in disinformation campaigns related to COVID-19 pandemic.
In addition to conventional PSYOP, unit 54777 includes both SIGINT and cyberspace capabilities. Related to SIGINT, unit 54777 gathers and analyzes communications to produce intelligence that can be used in further disinformation and influence campaigns. In the cyber arena, this unit works complementing Cyberspace Operations not only with digital PSYOP: its activities include operating in support of other GRU cyber units, creating and disseminating fake versions of their cyberspace operations, as well as operating on the tactical level by conducting electronic warfare and psychological operations.
Unit 54777 conducts most of its online operations through social media, an activity which began with the Maidan revolution. In addition to social media, this unit engages in spreading disinformation and manipulating public opinion through online digital platforms and public forums. It works through several front organizations, including InfoRos and the Institute of the Russian Diaspora, founded by Aleksandr Gennadyevich STARUNSKY. These are “information agencies” focused on political, economic and social life in the Russian Federation and other ex Soviet Republics, posting both in Russian and in English.
Probably, unit 54777 is located within the GRU 12th Directorate, which focuses on information operations. It is believed that unit 54777 is overseen by unit 55111. In fact, Aleksandr Gennadyevich STARUNSKY, former commander of unit 54777, was the deputy commander of unit 55111 when he was appointed to the Scientific Council. According to open sources, military unit 54777 has, or has had, different subordinate units performing PSYOP in every Russian military district in addition to the Moscow one:
- PSYOP Leningrad Military District, military unit 03126, located in Leningrad region.
- PSYOP Central Military District, military unit 03138, located in Yekaterinburg.
- PSYOP Southern Military District, military unit 03128, located in Rostov-on-Don.
- PSYOP Eastern Military District, military unit 03134, located in Khabarovsk.
A characteristic feature of all these units is their emblem: a combination of the international symbol for psychology, Y (“Psi”), and a red carnation, the heraldic symbol of Russian military intelligence, as shown in image (from Agentura website):