The inheritance of object handles between processes in a Microsoft Windows system can be a good source to identify local privilege elevation (LPE) vulnerabilities. After introducing the basic concepts around this type of security weaknesses, a tool capable of identifying and exploiting them will be presented, providing Pentesters and Researchers with a new point to focus their intrusion and research actions respectively, read on!
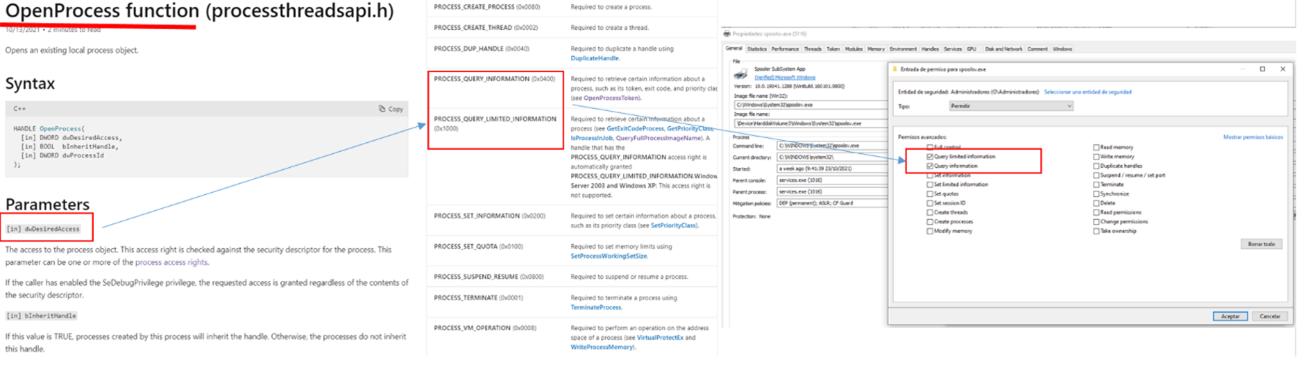
Within a Microsoft Windows operating system, processes are able to interact with securable system objects such as files, PIPES, registry keys, threads or even other processes. To do this and through the use of the WINAPI the source process requires the O.S. of a handle to perform a certain action on the object in question.
If the appropriate permissions and/or privileges are available, the O.S. authorizes this access by delivering the aforementioned object handle to the process that requires it. From that moment on it is possible to interact with it within the limits of the requested permissions. Let’s see the following example where a source process would make use of the WinApi OpenProcess function to try to open a target process (spoolsv.exe) in order to obtain information remotely from it (PROCESS_QUERY_INFORMATION).
[Read more…]
 In the world of advanced persistent threats or APTs, techniques used by malware artifacts play an important role in communication and exfiltering information via C2s (Command & Control). In this sense, there are as many as there are protocols and services and an attacker can draw from his/her imagination. As just small examples of “tricks” for disguising illegitimate traffic as apparently normal information are:
In the world of advanced persistent threats or APTs, techniques used by malware artifacts play an important role in communication and exfiltering information via C2s (Command & Control). In this sense, there are as many as there are protocols and services and an attacker can draw from his/her imagination. As just small examples of “tricks” for disguising illegitimate traffic as apparently normal information are: