As you can already guess from previous spoilers, in this third part of the series (see part one and part two), after having made clear the role that Threat Intelligence plays in the Purple Team methodology, we will go a bit more into details about the phases of preparation, execution and lessons learned in an exercise.
Disclaimer: As I mentioned in the first episode, I do not intend to set in stone anything in this article, but rather to give my point of view and provide an overview of a subject for which there is not much documentation, and what I found, is scattered in multiple sources.
After having developed an implementation plan based on the mapping of threats on the MITRE ATT&CK MATRIX, it is time to put all the use cases into practice. To do so, we will use Vectr.io, an open source web platform developed by Security Risk Advisors.
This tool is responsible for centralizing all the coordination tasks of the Red and Blue teams. But far from being a tool just for coordinating exercises, it is also prepared to be used as a sort of logbook of all operations executed in various exercises and their outcome over time, so that the evolution of the organization’s security posture can be tracked.
With an abstract description such as the above, it may be difficult to imagine how all of this is accomplished. Therefore, the aim of this post is to opt for a more practical approach.
For the sake of brevity, we will not detail all the functionalities of this tool but will show the possibilities it offers and how these can help us with our goal. It will then be up to you to explore the more advanced functions and evaluate whether they are useful for your particular use case.
First steps
The first thing to take advantage of this tool is to install it.
It can be installed in a relatively simple way through docker-compose, but if our goal is not to use it in production, it is convenient to use the SANS slingshot C2 VM that already has everything installed (plus many other things that are not the subject of this article). The only problem is that the installed version does not have the recently implemented functionalities.
One of the strong points of this platform is its wide compatibility being able to import among other things:
- TTPs designed with MITRE ATTACK Navigator
- APT Group TTPs from MITRE https://github.com/mitre/cti
- Atomic Test Cases from Atomic Red Team https://github.com/redcanaryco/atomic-red-team
- Collections from a CTI TAXII Server(such as MISP). More info here.
- Campaign templates from other instances of Vectr.io
- and other sources that will come
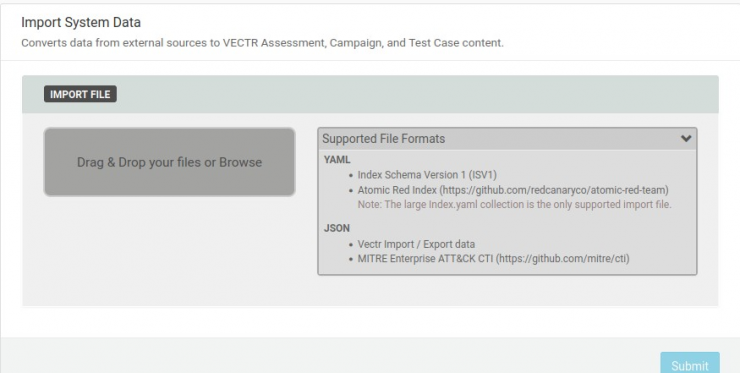
Of course, you can set up all Test Cases from scratch or take these campaigns/TTPs as a reference to make modifications to better suit your circumstances or organization, but these import modules make the first step towards a successful Purple Team exercise easy for those who do not have the knowledge to do so.
Campaign Management
Once the use cases are designed or imported, the next step would be to create an assessment. This is simply a way of aggregating a series of campaigns, usually pertaining to an exercise time frame.
Within these assessments the campaigns are created. In each campaign we will include all the Test Cases oriented to the same objective that will be executed within the same exercise. For example, we can create a TURLA campaign, a FIN7 campaign, and a phishing campaign that will be tested within the same assessment. We will see later how these divisions can be useful for reporting purposes.
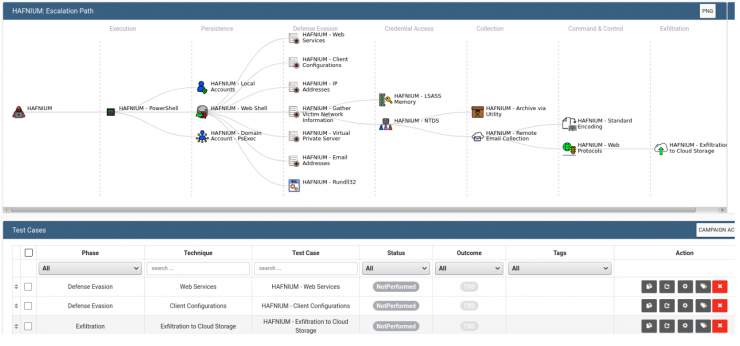
Below you can see what a campaign looks like in the interface. They are distributed in a graph divided according to the MITRE ATT&CK Tactics. Below is a list of all Test Cases. Here you can assign labels to each Test Case to expand the options and customize your workflow. In the Outcome column, the detection results of each Test Case are marked.
Test Cases
The options of each Test Case are divided into two zones: blue and red, where the fields to be filled in by the respective teams are located. These options can help us to document the actions being performed and their results. Depending on how meticulous we are, we can obtain a higher level of granularity and detail in the reports.
On the Red Team side, it is worth mentioning the possibility of taking notes of the times, the MITRE categories assigned to the Test Case, writing instructions for the operator or adding the targets to which the attack has been launched.
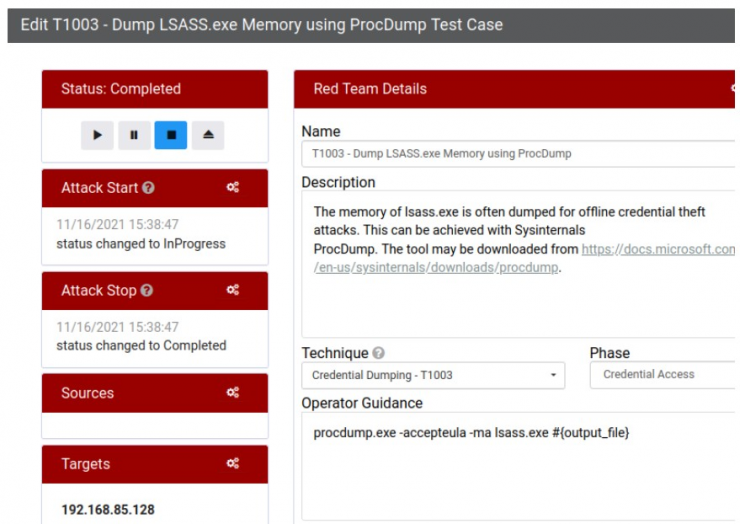
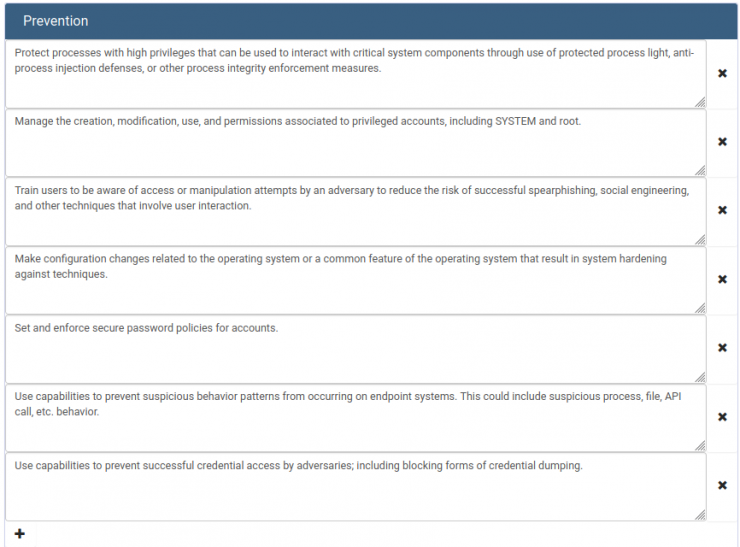
On the other hand, in the Blue Team part, you can describe prevention and detection tips as well as the result after the test (times, successful detections or forensic artifacts found). It is advisable, for example, to use this platform as a knowledge base for sigma/yara/suricata rules that have worked for each case.
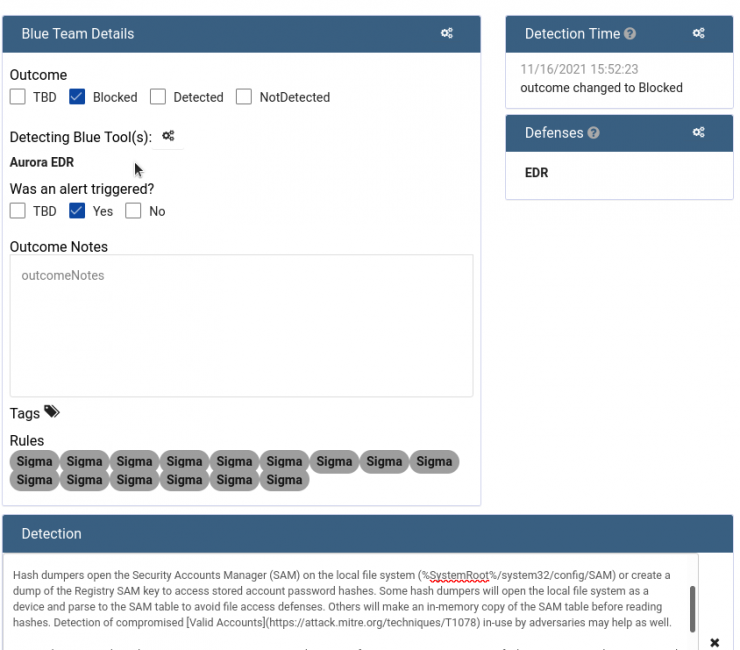
In the image we can see how the attack has been detected and blocked by EDR Aurora using sigma rules (by clicking on each rule, you can see the content).
And in the following image you can see the prevention measures to deal with an LSASS dump attack.
Lessons learned and reporting module
After having executed all the use cases for the number of iterations considered appropriate, it is of vital importance to keep a record of everything for two purposes:
To have a knowledge base for future exercises and thus, not to waste time and effort in replicating previously contemplated cases.
To have a way of reporting the results to the organization’s high management, who often do not have the knowledge nor the time to read long lists of logs and events. The lack of capacity of the technical staff to make executive reports can result in management fatigue or apathy, relegating security to a second place, while a good reporting capacity provides actionable information that contributes to the security areas being seen more as an investment than an expense.
Vectr.io‘s reporting module plays an important role in all this, by means of which different diagrams can be generated with the results of the exercises, being able to apply advanced filters that allow a good degree of granularity.
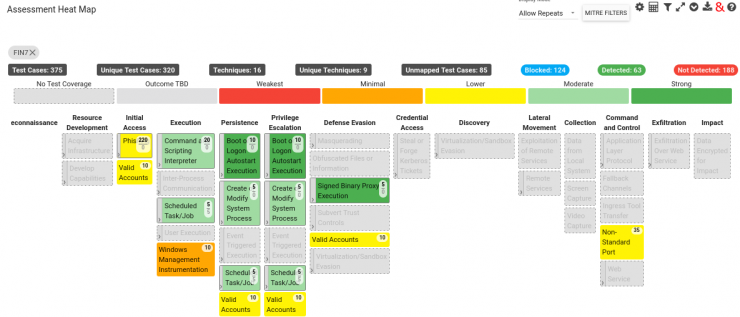
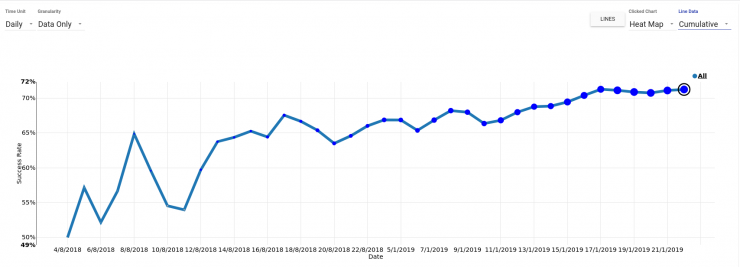
We see below how you can see, for example, the degree of coverage (in terms of MITRE ATT&CK) in our assesment of the TTPs associated with FIN7 (first image) or the percentage of detections for all the Test Cases tested over time (second image).
Bonus Track
I would not like to end this article without mentioning one of the most interesting features of this application, the Vectr Execution Framework.
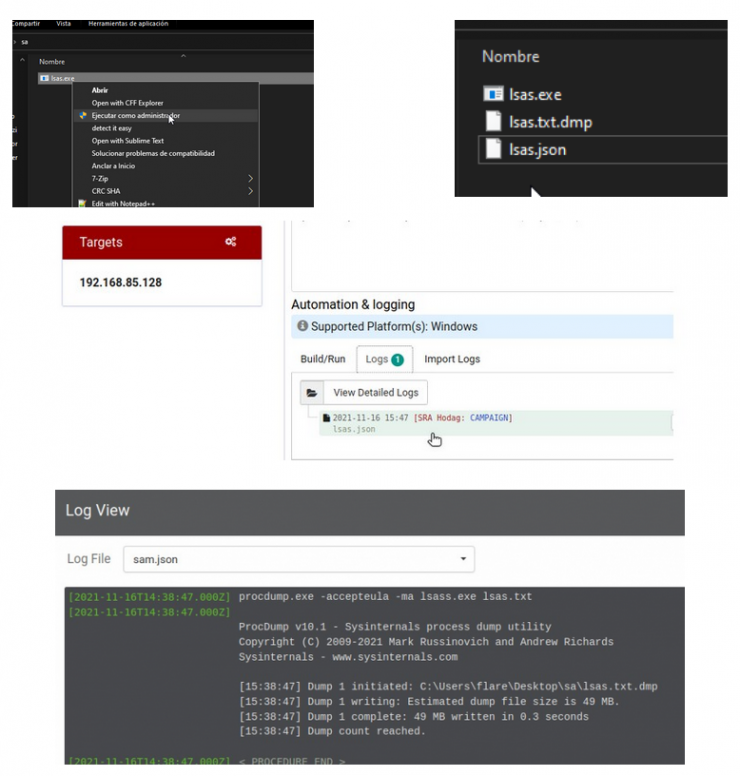
Through this module, Vectr.io allows the creation of executable files that can be launched on victim machines. These executables can be modified ad-hoc for each specific case through the use of arguments and also allows the addition of files that function as artifacts to be found by the Blue Team.
Once the executable is launched, it generates a log that can be imported into the Vectr console so that you can keep track of already tested computers and date/time of the tasks.
Unfortunately, it is not yet possible to launch these executables remotely from Vectr itself, so you will have to use another alternatives such as manual local execution, GPOs, SCCM, WinRM, etc. for the execution of the executable and the collection of logs.
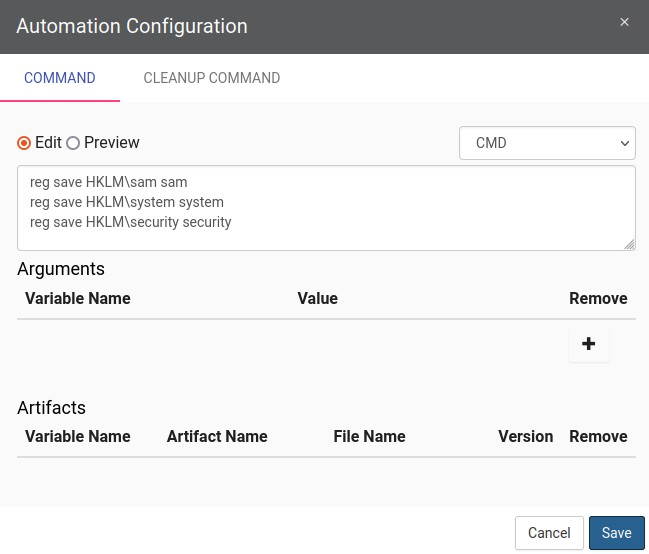
It is shown below how in each Test Case, there is an Automation & Logging menu. This is where we will configure the commands to be executed and the arguments. Once configured you can download the compiled exe.
Being a feature under development, it might fail in some cases. After talking with the developers (who answered very kindly my doubts in their Discord channel) they advised that if this fails, the files are in /var/lib/docker/volumes/sandbox1-builder-runtimes/_data/out/build-*.
Now all that remains is to run the exe on the victim machine, and collect the generated json to load it into Vectr.io and populate our log.
Conclusion
With this post we end this series of articles that I hope you have enjoyed and that have given you something.
Obviously, this tool has many other utilities (and more to come) so I encourage you to explore it in depth to extract all the juice, and maybe it can bring you a differential value in your organization.
If any of you detect any major error or inconsistency, do not hesitate to let me know. We are all constantly learning, so see you next time!