After discussing in the first post of the series some details about the new version of OWASP Top 10, and in the second one the new category A08, software and data integrity flaws, in this third and last post we are going to analyze the category A10: Server-Side Request Forgery (SSRF), as well as the possibilities of mitigating these types of vulnerabilities.
A10: (Server-Side Request Forgery, SSRF)
SSRF attacks are possible when an application allows a remote resource to be obtained without validating the URL provided by the user. This type of attack can bypass the protection provided by the firewall, VPN or access controls.
For example, when an application allows you to specify a URL to which the initial request will be redirected, if we do not filter the URL to which it will be redirected, the attacker could take advantage of this to enter a random address.
Attacks could consist of requests such as:
Host: example.com
or
Host: example.com
So if the redirection URLs are not filtered and the resources are not protected, they would allow the attacker to access them.
One of the causes of these attacks is the application code that allows access from the application to addresses that should not be accessed, so that the attacker can send requests from the application to both internal and external resources and receive the responses.
SSRF attacks are increasing due to cloud services and the progressive increase in architecture complexity.
Mitigation of these attacks can be carried out on several fronts:
- From the network layer.
- From the application layer.
- At the general level.
2.1 Mitigation from the network layer
The following are some ways to mitigate these attacks from the network layer.
- Segmenting networks. Using for example VLANs, to avoid spreading the attack in one part of the network to other parts of it. It would be the same principle used in a ship with compartments; this allows that if a waterway occurs and cannot be bailed out, the water does not invade the other compartments.
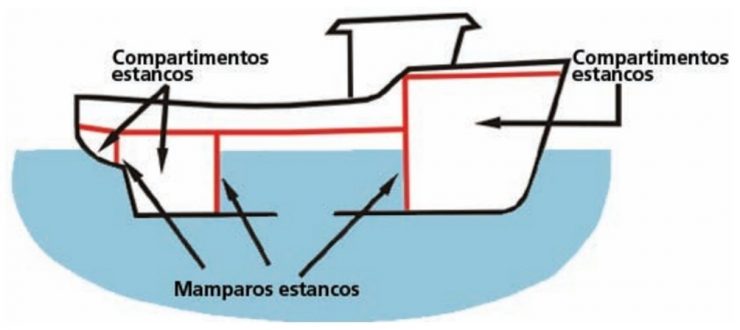
Watertight compartments and bulkheads. Source: https://www.fao.org/3/i0625s/i0625s02c.pdf
- Always deny by default. The firewall should block all intranet traffic, letting only explicitly allowed traffic through.
- Log network traffic when a request is accepted or denied. This way we could go to the logs to see what is happening, in an ideal situation, we should also be able to create alerts to warn us of suspicious behavior.
2.2 Mitigation from the application layer
Listed below are some forms of mitigation that can be carried out from the application layer.
- Sanitize and validate user input data, which is mandatory in this and other situations, as it is one of the reasons for injection attacks.
- Use whitelists to allow only the URL, port and destination schemes that we decide will be accessible. Whitelisting allows only what is specified in the whitelist and denies everything else.
- Deshabilitar las redirecciones HTTP si no son estrictamente necesarias, ya que se debe incluir la funcionalidad que realmente se necesite, y el resto de funcionalidad deshabilitarse. Disable HTTP redirects if they are not strictly necessary, since only the functionality that is really needed should be included, and the rest of the functionality should be disabled.
- Avoid using deny lists or regular expressions as they can be avoided and would not be of much use.
2.3 Mitigation at a general level
The following are some of the ways to mitigate these attacks, although now, at a general level.
- Controlling localhost traffic, since its security is usually somewhat neglected, as it is not directly accessible from the LAN or Internet. With this attack we have seen that this must also be taken into account.
- Provide VPN access as far as possible to the users of our organization. This limits the exposure of our services to external networks or the Internet, by granting access only to our users from the local network. In addition, we can more accurately log access to services, and detect suspicious patterns of behavior.
- Verify the response when performing the redirection. We must verify that the response is as expected. For example, if we redirect to a page on the source code repository server, we should check that the page to which we will redirect the request belongs to the server and is not another page.
- Disable unused URI schemes, as in other risks where the recommendation is to disable elements that are not being used or needed. In this risk we should recommend that unused services and ports be restricted, allowing access only to those that are needed or must be accessed, specifying them explicitly with whitelists. For a list of URI schemes, see RFC 3986. Uniform Resource Identifier (URI): Generic Syntax: https://datatracker.ietf.org/doc/html/rfc3986.
A list of examples compiled from the referenced RFC of URIs that we may not need would be:
http://www.ietf.org/rfc/rfc2396.txt
ldap://[2001:db8::7]/c=GB?objectClass?one
mailto:John.Doe@example.com
news:comp.infosystems.www.servers.unix
tel:+1-816-555-1212
telnet://192.0.2.16:80/
urn:oasis:names:specification:docbook:dtd:xml:4.1.2
Note that in addition to the domain, you should also check that the scheme is allowed. For example: https://example.com and ftp://example.com share the example.com domain, but they differ in their scheme, https or ftp respectively.
- Enable authentication for all network services, especially for those that by default do not require authentication, such as: Memcached, Redis, Elasticsearch or MongoDB. We also recommend that secure protocols such as HTTPS or TLS be configured and enabled for access to them.
Following this point we should refer to the concept of “Zero Trust in corporate networks”, which could be interpreted as “Zero Trust in corporate networks”. This information can be found on the “Angels” website of the National Cryptologic Center, in the “Cyberadvice” section, in the “Threats” section, where there is a summary document and an explanatory video in Spanish.
In the referenced document there is a significant sentence to understand the magnitude of Zero Trust: “The traditional model based on the concept of perimeter, where access is protected from the outside and the internal user is trusted, is no longer valid“, so we are facing the change of a classic paradigm where a perimeter was defined to protect us from the outside and we could trust the internal elements.
The reader is encouraged to visit the additional links in the referenced content to expand on the concepts. Documents and videos on various related topics in infographic format, useful to understand in a visual way the concept, can be found on the mentioned website. They are accompanied by videos and in some cases by reports where the information is expanded, as well as tips and solutions.
With this article we close the series related to the OWASP Top 10 2021 news. We hope you have enjoyed it and, above all, that you find it useful.
Thank you very much to all of you.
