The logistics sector has evolved in recent years to more complex deployments where there is a greater flow of communication between its elements. This evolution is noticeable in critical sectors such as maritime, for example, in port environments there are a large number of interconnections for the exchange of information between a wide range of systems.
Real examples show how there are more and more cyber-attacks targeting companies in the maritime sector. It is therefore essential to develop cybersecurity strategies based on system protection, attack detection and incident response capabilities. Cybersecurity must be considered from the design stage, thinking beyond functionality and considering it as a process that must be incorporated into the day-to-day operations of all companies.
Given the variety of industry best practice standards or mandatory regulations that have emerged on cybersecurity in the maritime sector, IACS, a non-governmental, technical-based organization of eleven major marine classification societies, has established new unified requirements (UR E26 and E27) on the cyber resilience of ships that will apply to ships contracted for construction on or after January 1, 2024. Cybersecurity will move from being an added value to a market requirement.
Humanity is facing new challenges that require, more than ever, a new comprehensive vision. As a result, all organizations, and society in general, are to a greater or lesser extent immersed in a process of digital transformation. This transformation is based on the incorporation of technology in all the organization’s business processes and hyperconnectivity. There has been a convergence between Information Systems (IT), Operation Systems (OT) and Consumer Technologies (CT), giving rise to an interconnected ecosystem in which the impact of one node can have direct implications for the entire chain.
From a cybersecurity standpoint, this systemic world leads to a high-risk scenario. As our business processes become more dependent on technology, the impact of a potential cyber-attack increases.
The hyperconnectivity of the systems that form the technological base on which we develop our business processes greatly expands the attack surface and, consequently, the probability of a cyber incident occurring.
According to the Allianz Global Corporate & Specialty Risk Barometer for the year 2023 (Allianz Risk Barometer: Identifying the major business risks for 2023), cyber incidents are the greatest danger for companies worldwide. This threat has been considered by 34% of the 2,712 risk management experts consulted in more than 94 countries and territories. It is worth noting that, a decade ago, cyber risk ranked fifteenth, with only 6% of responses. Awareness of the cyber threat has grown rapidly in recent years, driven by the increasing dependence of companies on their data and IT systems, as well as a number of incidents that have occurred.
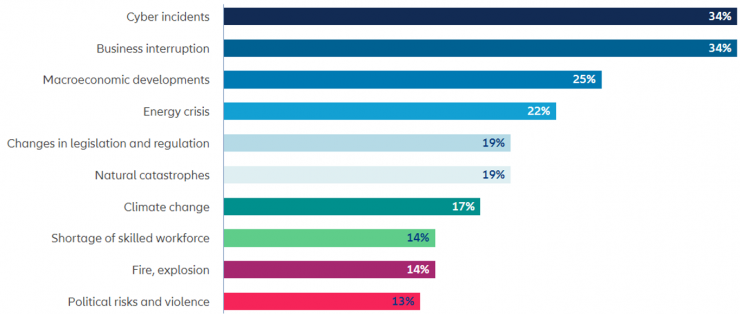
It is noteworthy that the second greatest danger is business interruption, also with 34% consideration. It is worth noting that the same report includes a survey of 917 experts, which indicates that cyber incidents are considered by 45% of respondents as the most feared cause of business interruption.
So it can be concluded that directly and indirectly, 50% of respondents consider cyber incidents as the greatest danger to their company.
Evolution in the logistics sector
The logistics sector has evolved by introducing new technologies, which have made it possible to move from traditional logistics based on the lack of coordination between the different parties, with low-complexity cargo flows. That is to say, concrete and defined communication flows, and a rigid system where constant or periodic supplies predominate.
In today’s logistics industry, there is an increasing demand to optimize the supply chain. Physical transport time is invariant, so delivery schedules and routes, storage or transport methods must be optimized. In addition, there is an increasing and increasingly distributed demand. This has resulted in an evolution of the logistics sector towards more complex deployments with new environments and techniques, based on an increase in the number and frequency of communications, the introduction of centralized control systems and the introduction of new technologies that blur the border between IT and OT. With these advances comes a new concept, fleet management. It is about the administration of a group of elements of the same organization.
The shipbuilding sector: a strategic field in a global economy
As the pandemic has shown, there is a strong interdependence between producers and consumers, who can now be found anywhere in the world. They are connected, to a large extent, by maritime transport. Today, maritime transport is a fundamental pillar of the global economy.
The number of tons transported by ship globally has increased by a factor of 2.5 in the last 25 years (UNCTAD Handbook of Statistics 2022 – Maritime transport). The maritime transport sector involves a wide range of players, including shipbuilders or shipyards, shipping companies, shipping agents, ports themselves and the national and international bodies in charge of its regulation. In addition, it is deeply interconnected with other elements of logistics chains, such as rail and road transport of goods.
The case of ships: a large-scale intelligent system
Linked to the maritime sector, the shipping sector has traditionally worked with isolated elements, and with specific communications from control centers to monitor the position and route of transports. Nowadays, the interconnectivity of the elements has increased, so there are constant communications with the outside world, including communications between transports. Vehicles are now capable of receiving and interpreting information about other transports at the same time.
A vessel is a complex system where multiple systems interact: customer services, personnel from different departments, maintenance, cargo management, bridge control, etc. But it also requires continuous monitoring of the status of the systems and needs regular wireless communications with control centers at considerable distances (there is a wide range of technologies for remote communications).
Cybersecurity in the naval sector
The most common cybersecurity-related problems encountered in the naval sector are related to the long life cycle of systems, the lack of reference standards, reliance on network isolation and physical security, as well as a lack of awareness of aspects such as the convergence of IT and OT technologies, the weakness of current protection systems, the motivation of potential attackers or the existing risks.
It is increasingly common to see cyber-attacks in critical sectors, such as the maritime sector. Everyone remembers the cyberattack suffered in 2017 by the shipping company A.P. Moller Maersk, which forced the company to paralyze its operations for weeks and had an economic cost of between $250 million and $300 million.[1]
But this incident is not an isolated case. In 2018, the shipping company COSCO suffered an attack that affected its operations in the United States; in April 2020, the shipping company MSC saw its Geneva headquarters compromised; in September 2020 CMA CGM announced that a cyberattack had affected its peripheral servers; in 2021 the IT infrastructure of OMI was subject to a cyberattack and even in 2023, DNV, a ship certification company, suffered an attack that has affected 1,000 ships that depend on its technology[2].
What all these attacks had in common was that they were malware cyberattacks, and in all cases through ransomware. The shipping industry is one of the sectors most affected by cyberattacks, either as a direct target or as a possible collateral damage.
Cybersecurity strategy
At a global level, common strategies should be defined that outline guidelines to identify vulnerabilities, weaknesses and opportunities for improvement in all areas. The purpose of these standards would be to ensure that cyber assets are adequately protected, in such a way as to guarantee their reliability in the face of possible attacks or simply security incidents in the field of cybersecurity.
For the development of a standard, it must be taken into account that the industrial sector is very heterogeneous, so there are no general solutions. In addition, the pace at which changes in the industrial sector are assimilated must be taken into account in order to avoid setting unrealistic horizons.
The growing concern for cybersecurity in the shipping sector is causing international public and private organizations to promote the creation of standards in this area. Thus, the IMO (International Maritime Organization), the United Nations specialized agency responsible for setting standards for safety, security and environmental performance in international shipping, creates the circular MSC FAL 1-Cir.3 and recommendation MSC.428.
The MSC Circular MSC FAL1-Cir.3 provides high-level guidance on cybersecurity risk management recommendations. This circular describes an initial list of systems to be reviewed, sets out a method for analyzing them and provides a list of best practice guides and standards relating to information security, such as ISO/IEC 27001 or the NIST framework 1.0.
IMO recommendation MSC.438 ratifies that ships must include in their ISM (International Safety Management) manual a cyber-attack resilience plan, and encourages the authorities of each country to review its implementation in the next revision as of January 1, 2021.
Following this, new standards are emerging, such as the Code of Practice Cyber Security for Ships[3] developed by the UK Department for Transport or the cybersecurity certifications developed by companies such as DNV (Cyber Secure class notation – DNV-GL)[4] or Lloyd’s (ShipRight procedures) [5] . The latter certifications are based on international reference frameworks of recognized prestige, such as the IEC-62443 standard, which addresses cybersecurity in industrial automation and control systems.
Given the variety of cybersecurity standards that have emerged, the International Association of Classification Societies (IACS), a non-governmental, technical-based organization comprised of eleven marine classification societies covering more than 90% of the world’s cargo ships, has adopted two new unified requirements (URs) on cyber resilience of ships:
- UR E26 aims to ensure the secure integration of operational technology (OT) and information technology (IT) equipment into the ship’s network during the design, construction, commissioning and operational life of the ship. This UR addresses the ship as a collective entity for cyber resilience and covers five key aspects: equipment identification, protection, attack detection, response and recovery. [6]
- UR E27 aims to ensure that the integrity of the system is assured and reinforced by third party equipment providers. This UR establishes requirements for the cyber resilience of shipboard systems and equipment, and provides additional requirements relating to the interface between users and shipboard computer systems, as well as design and product development requirements for new devices prior to their deployment on board ships. It should be noted that the requirements established by this UR are based on the requirements of Part 3-3 of the IEC 62443-3-3 standard (System security requirements and security levels). [7]
Entry into force
These URs will apply to new ships contracted for construction as of January 1, 2024.
The entry into force of these new requirements will imply a greater effort for operators, shipowners, shipyards and suppliers, since cybersecurity will have to be incorporated into the design, construction and operation of ships.
Incorporating cybersecurity in the early design phases of a ship will be critical, as it will allow for better ship protection results, and will significantly reduce costs as it will be easier to implement cybersecurity-related measures.
Cybersecurity in the naval sector has gone from being an added value to a market requirement.
References
[1] https://www.diariodelpuerto.com/es/15404881030567640
[2] https://www.dnv.com/news/cyber-attack-on-shipmanager-servers-update-237931
[3] Code of Practice Cyber Security for Ships – Department of Transport of United Kingdom https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/642598/cyber-security-code-of-practice-for-ships.pdf
[4] Cyber Secure class notation – DNV-GL https://www.dnvgl.com/services/cyber-secure-class-notation-124600
[5] ShipRight procedures – https://www.lr.org/en/shipright-procedures/#accordion-digitalships
[6] UR E26 – https://iacs.org.uk/download/14104
[7] UR E27 – https://iacs.org.uk/download/14105
