Today, I do not think it necessary to mention what the SSH (Secure Socket Shell) protocol is, since it would be really difficult to live without it today. Therefore, SSH is considered globally as the “mega” indispensable tool for any administration work. Among the advantages of its use we can find: secure access to remote machines, access to services on other machines by creating direct or reverse tunnels, creation of proxy socks, creation of secure channels for the encapsulation of traffic from unsecured applications … etc.
I do not think it necessary to mention what the SSH (Secure Socket Shell) protocol is, since it would be really difficult to live without it today. Therefore, SSH is considered globally as the “mega” indispensable tool for any administration work. Among the advantages of its use we can find: secure access to remote machines, access to services on other machines by creating direct or reverse tunnels, creation of proxy socks, creation of secure channels for the encapsulation of traffic from unsecured applications … etc.
Among the innumerable advantages of this protocol, there is a point that can sometimes be a great inconvenience, the performance of the connection.
To try to solve this problem and add improvements, Mosh (mobile shell) emerged, an application that offers several advantages over the traditional SSH connection. It was presented at the USENIX Annual Technical Conference 2012 by Keith Winstein & Hari Balakrishnan, M.I.T. Computer Science and Artificial Intelligence Laboratory.
- Operation under the UDP protocol, which greatly increases the speed of response.
- Allows roaming between networks even if there are IP address changes in the connection.
- Supports intermittent connectivity and automatic session recovery.
- Interaction of writing totally agile with the server because it does not wait for a response from every keystroke, preventing lag of writing and enabling the editing and correction of orders.
- Client and server under non-administrative privileges.
- Designed from scratch and supported only on UTF-8.
To establish the connection, Mosh does not raise any service, but it relies on SSH to initialize it so that the credentials and type of authentication (password, public key or certificates) will be the same as using SSH. Once the authentication has been con-validated, the connection becomes UDP and exchanges all communication over encrypted UDP datagrams making the connection more resilient.
There are packages compiled for the main distributions of Linux, so it will be enough to use the appropriate package manager depending on the distribution. In debian and derivatives it will suffice with a simple apt-get install mosh.
For the correct configuration, only a change in the firewall must be made to allow incoming UDP connections between ports 60000-61000 on the machine where Mosh is located.
The basic configuration for a system with Iptables on the same machine as Mosh is as follows:
iptables -I INPUT 1 -p udp --dport 60000:61000 -j ACCEPT
 The usage syntax is similar to SSH, so the change does not involve any effort.
The usage syntax is similar to SSH, so the change does not involve any effort.
ssh user@example.com ? mosh user@example.com
In case of needing to pass specific SSH arguments it will be done in the following manner:
mosh --ssh="ssh -p 2470" user@example.com
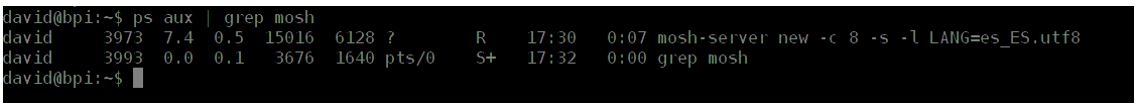
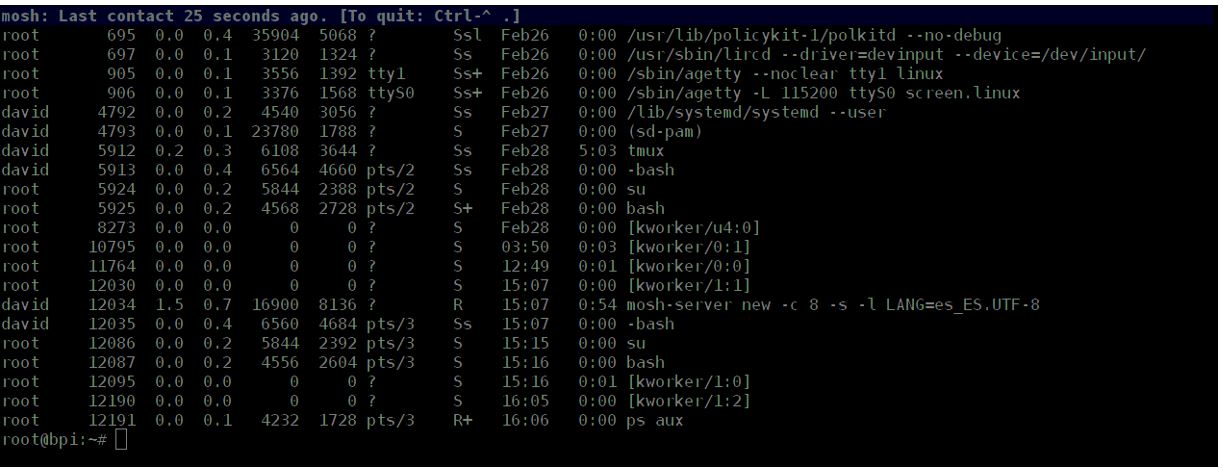
Once the connection is made we will see a Mosh process in the system
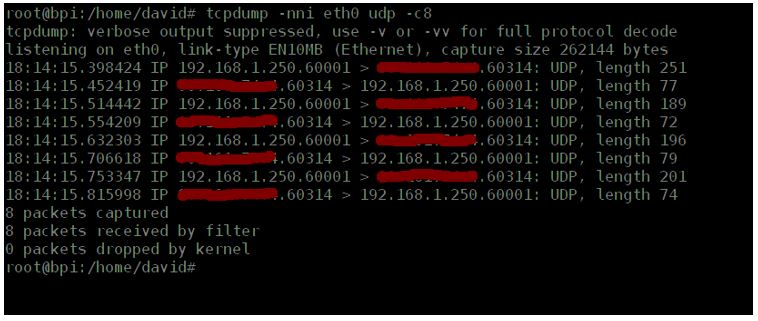
to verify it, we will see that it is actually generating UDP traffic
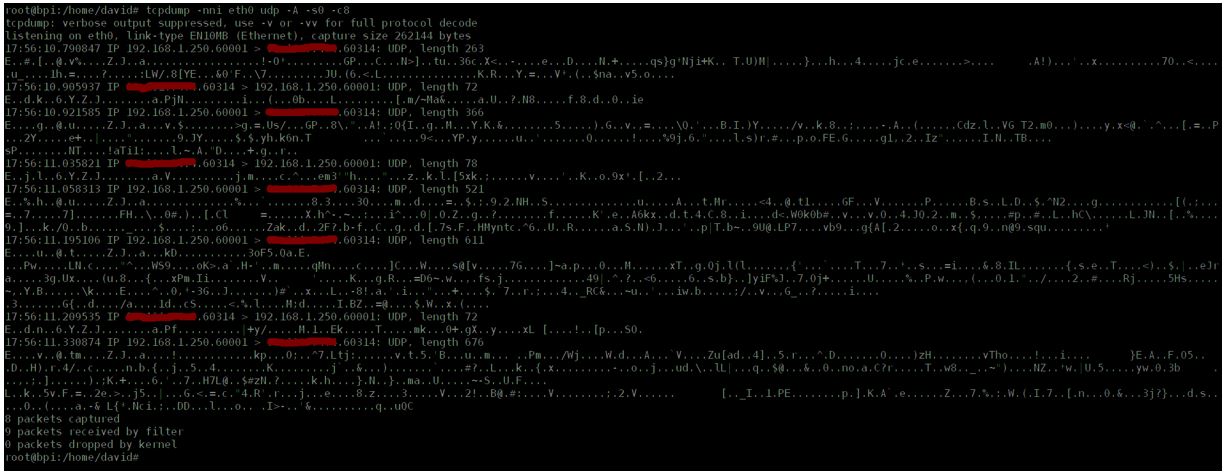
And besides, said traffic is not legible.
In the event of an interruption of the connection, a bar will notify us of the disconnection. In this case we will force the interruption by disconnecting the network interface.
Once we recover the connection, the terminal will remain intact.
Mosh is a free software and is available under the following platforms: GNU / Linux, BSD, MacOS, Solaris, Android, Chrome, and iOS. Finally, it is recommended to use Mosh in conjunction with screen or tmux because it does not save scroll on the screen since it only synchronizes the changes in the screen.
Here are a few links for further information as well as the video presentation of the tool.
For more information access the official website of the project https://mosh.org/
ACT Presentration 2012 https://www.usenix.org/conference/atc12/technical-sessions/presentation/winstein

ssh + tmux = WIN
Hi Martin.
I’m totally agree with you. Tmux is one of my preferred applications on linux, and is one of the first that I install on a new system.
Regards
David