After his last dispute (https://www.securityartwork.es/2018/02/26/evadiendo-av-shellter-tambien-sysmon-wazuh-i/), Pepote decided to rehire Pepito, who at heart was a good worker. But before that, Pepote took a couple of precautions, such as blocking web pages with “hacking” content that could make it easier for Pepito to perform improper actions.
Pepito accepted, but still holds a grudge from the time he was in prison, so on his first day on the job he is already trying to find ways to carry out malicious actions against his boss. (Already from here it smells like a promising and cordial working relationship, but that’s for another day).
For this reason, he has been searching, and a hacking forum has recommended the website “comohackearamijefe.saw”.
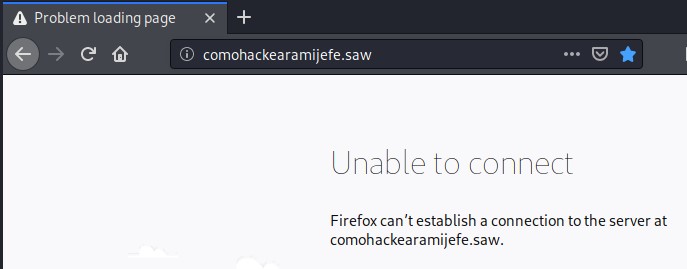
“Well… it seems that they have blocked this type of website…” thinks Pepito. However, Pepito has just remembered that he has a web server made in GO where his biography is:
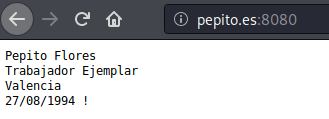
Whose code is as follows:
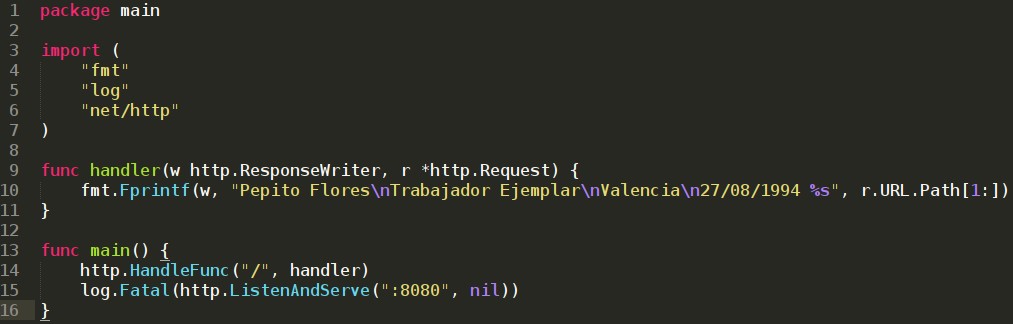
This domain is not blocked and you could take advantage of it to perform a port-forwarding to the blocked domain, without anyone knowing, so you decide to make the following modifications to your server:
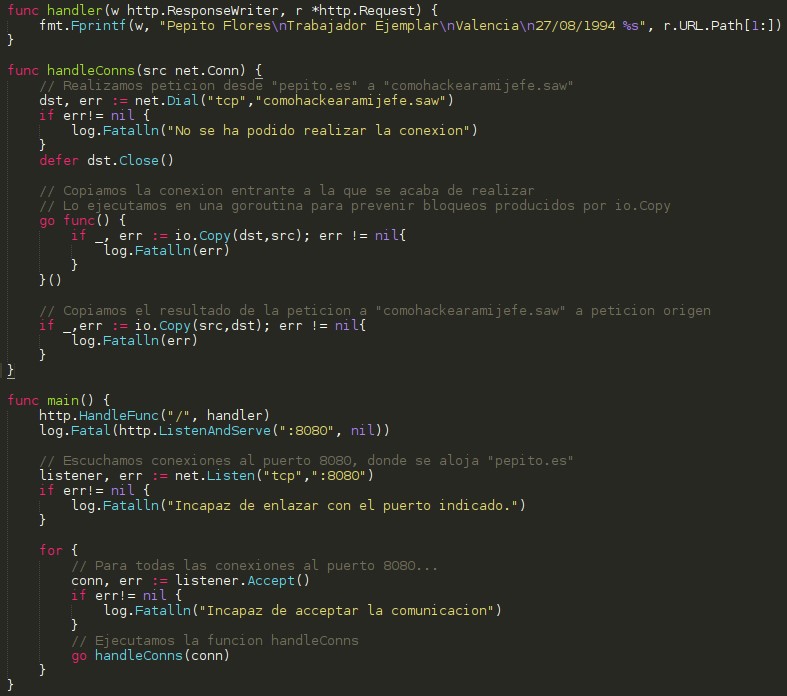
Once these changes have been applied, when you access “pepito.es”, this web server will make the request to “comohackearamijefe.saw”, and will return the result to the originator of the request.
The following screenshot shows Pepito successfully testing his access to “comohackearamijefe.saw” through “pepito.es”:
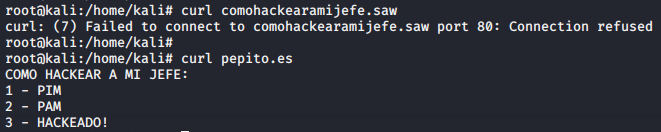
In this way, Pepito has managed to evade his boss’s block and can thus access websites/IPs without leaving a trace on the computer. (To the question “Will Pepito end up in jail again?” There is no answer yet).
Code available at: https://github.com/ppll0p1s/Proxying-a-TCP-conn
