ISC’ crew have a montly Traffic Analysis Quiz, and I want to practice some Network Forensic Kung-Fu, so allow me to introduce you Mr Natural.

What we have
- a packet capture (pcap) of infection traffic (let’s keep reading, don’t open it yet!)
- an image of the alerts shown in Squil (em ok)
- a text file listing the alerts with a few more details (now this is yummy)
- a PDF document with answers to the questions below. (SPOILERS!)
What do we know
- LAN segment range: 10.12.1.0/24 (10.12.1.0 thru 10.12.1.255)
- Domain: mrnatural.info
- Domain controller: 10.12.1.2 – MrNatural-DC
- LAN segment gateway: 10.12.1.1
- LAN segment broadcast address: 10.12.1.255
What our b0$$ want to know
- What is the IP address of the infected Windows host?
- What is the MAC address of the infected Windows host?
- What is the host name of the infected Windows host?
- What is the Windows user account name used on the infected Windows host?
- What is the date and time of this infection?
- What is the SHA256 hash of the EXE or DLL that was downloaded from 5.44.43.72?
- Which two IP addresses and associated domains have HTTPS traffic with “Internet Widgets Pty” as part of the certificate data?
- Based on the alert for CnC (command and control) traffic, what type of malware caused this infection?
Sharping the axe
Before starting, we must shape our tools.
In this post, Unit42 asks us how to configure Wireshark properly. Wireshark is not malware-oriented, but we can tune it customizing a few options. Do it now, thank me later.
Meeting Mr Natural
After taking a glance to the network data, it’s time to open our precious .PCAP file.

1. What is the IP address of the infected Windows host?
We start grepping by our first filter:
http.request or ssl.handshake.type == 1
The value http.request filters URLs for HTTP requests, while ssl.handshake.type == 1 filters domains names used in HTTPS or SSL/TLS traffic.
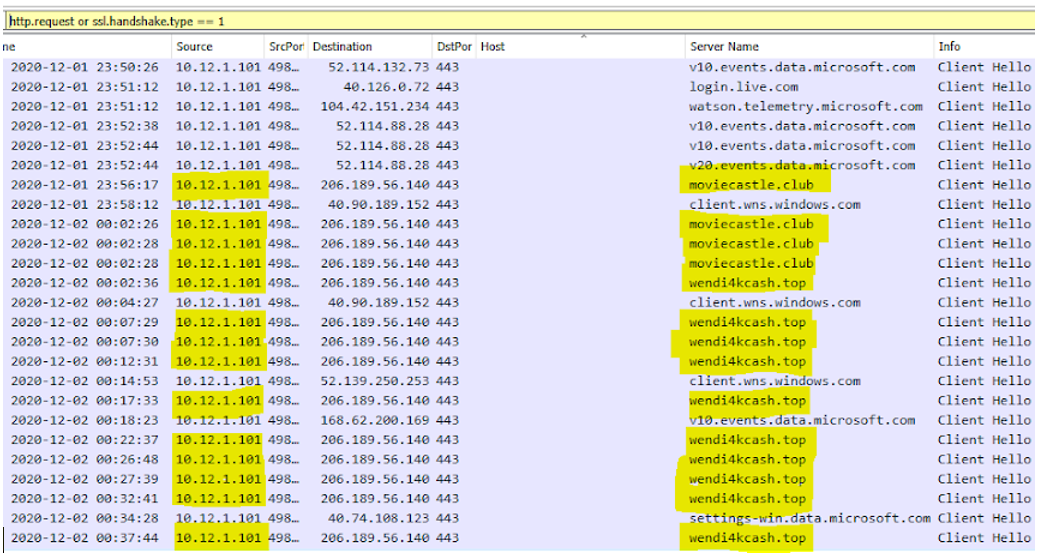
The host 10.12.1.101 has been in suspicious places and could be the root of the problem.
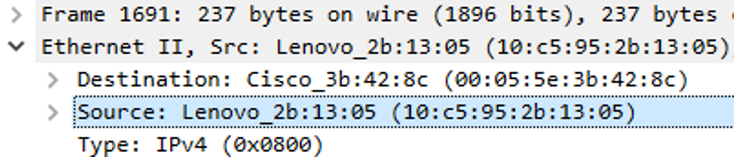
2. What is the MAC address of the infected Windows host?
3. What is the host name of the infected Windows host?
Let’s do some research:
DHCP or NBNS. DHCP traffic can help identify hosts for almost any type of computer connected to your network. NBNS traffic is generated primarily by computers running Microsoft Windows or Apple hosts running MacOS.
Trying with a bootp filter (DHCP) shows no matches. We are going to use a NBNS (NetBIOS Name Server) filter.
NBNS is a server responsible for maintaining a list of mappings between NetBIOS computer names and network addresses for a network that uses NetBIOS as its naming service.
A computer registers itself with the NetBIOS name server upon startup by providing the name server with its computer name and network address. When the computer needs to communicate with a remote machine, it queries the name server for the network address of the remote machine.
This filter shows just what we need.
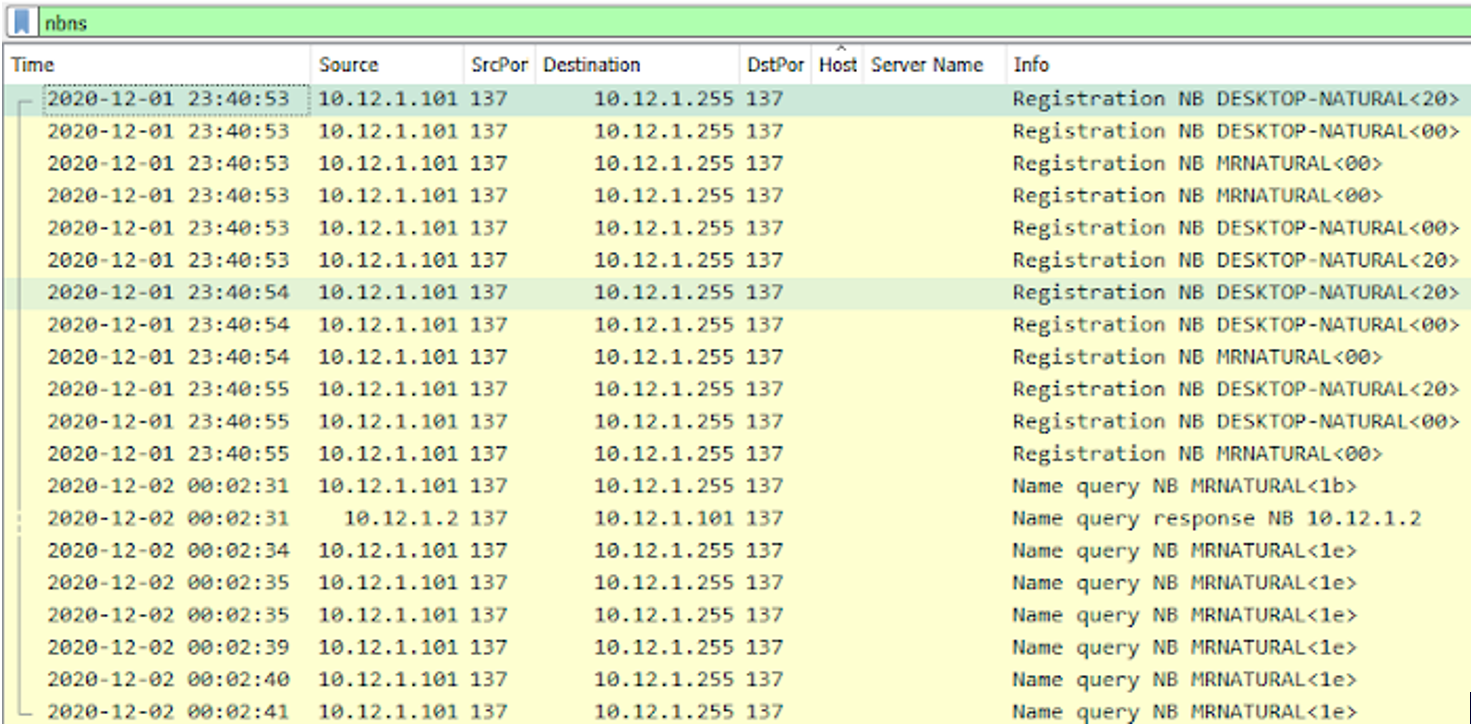
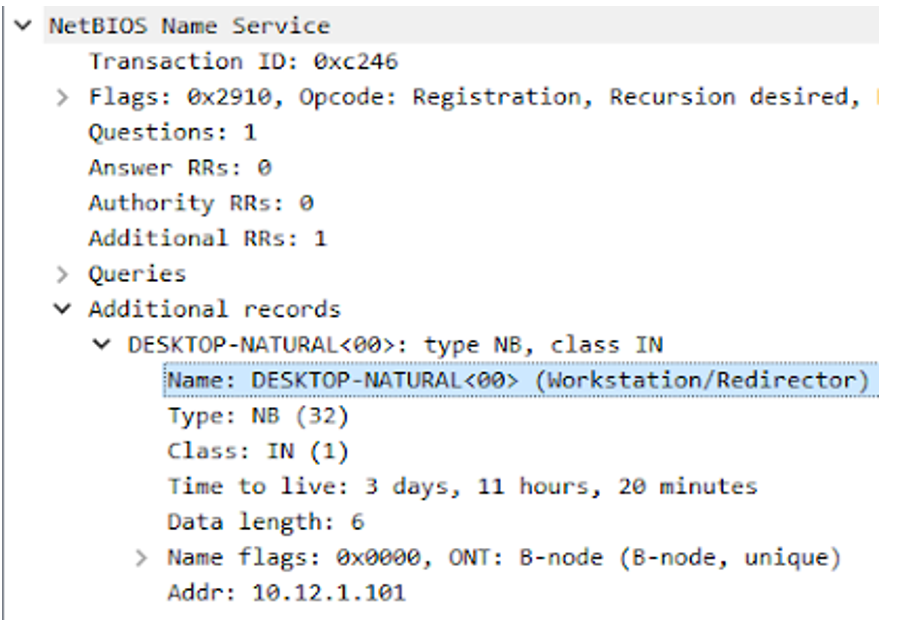
4. What is the Windows user account name used on the infected Windows host?
If we ask about Windows account, we are talking about Kerberos. Wireshark has a nice kerberos filter for this: kerberos.CNameString
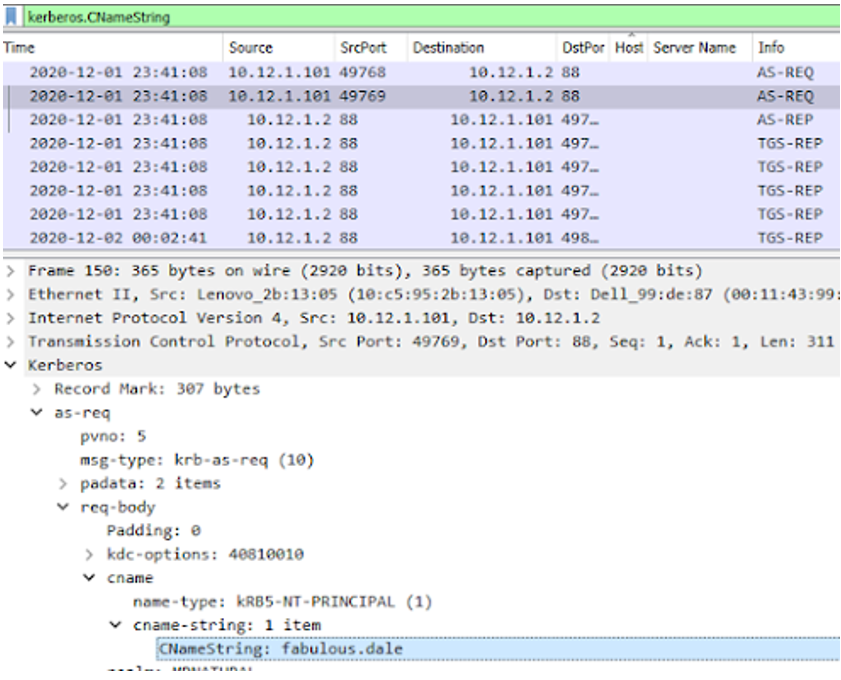
We can see that the account name is in the CNameString: fabulous.dale. Another option could be a filter of hosts contacting the Domain Controller (10.12.1.2 – MrNatural-DC).
5. What is the date and time of this infection?
We can see the first GET request on Tuesday 2020-12-01 at 23:41:42 UTC:
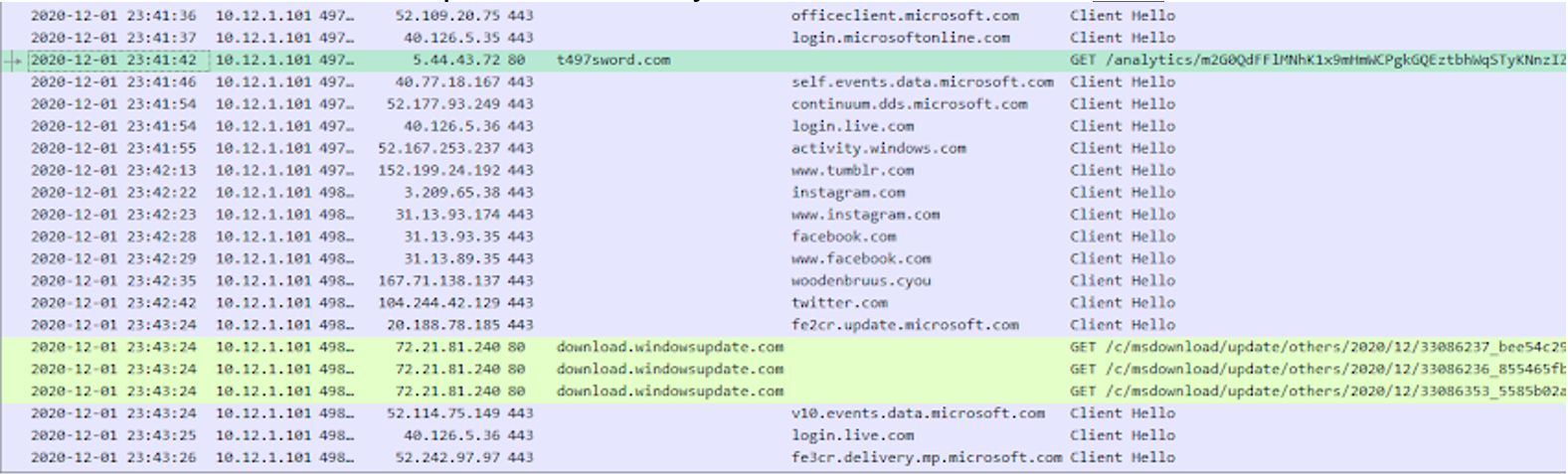
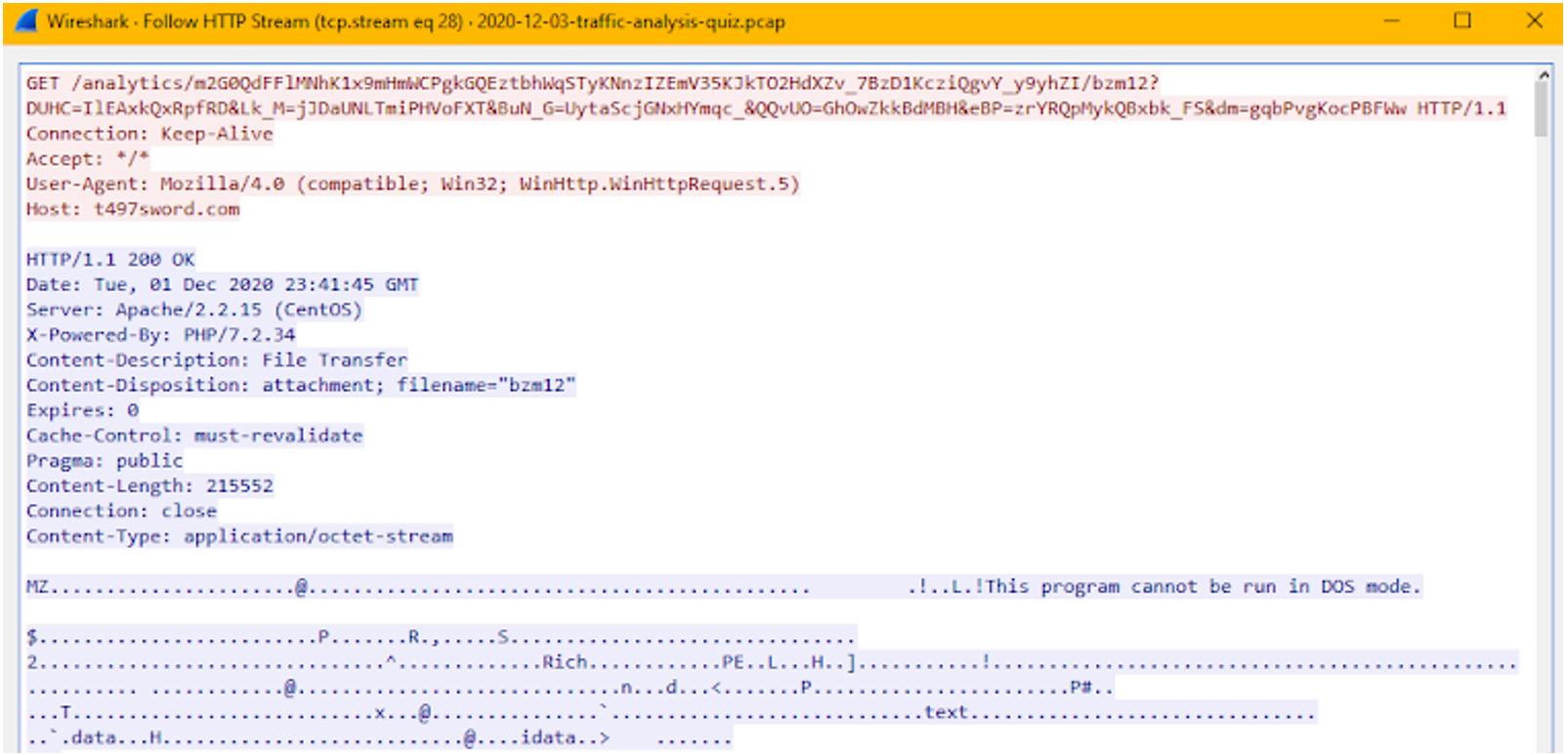
That packet asks for a resource, and the response contains a PE file (as we can observe the MZ and PE signatures). An easier way (as we have an alert system) is to check the logs:
Count:10 Event#3.3623 2020-12-01 23:41 UTC
ET POLICY Binary Download Smaller than 1 MB Likely Hostile
5.44.43.72 -> 10.12.1.101
IPVer=4 hlen=5 tos=0 dlen=1500 ID=0 flags=0 offset=0 ttl=0 chksum=31033
Protocol: 6 sport=80 -> dport=49790
Seq=0 Ack=0 Off=5 Res=0 Flags=******** Win=0 urp=22698 chksum=0
So we can establish 2020-12-01 23:41 UTC as the time of infection.
6. What is the SHA256 hash of the EXE or DLL that was downloaded from 5.44.43.72?
For that question we have to recover the PE file from the traffic dump.
When we filter for ip.addr == 5.44.43.72 and http we find out the domain: t497sword[.]com
We can recover the file from File -> Export Objects -> HTTP:
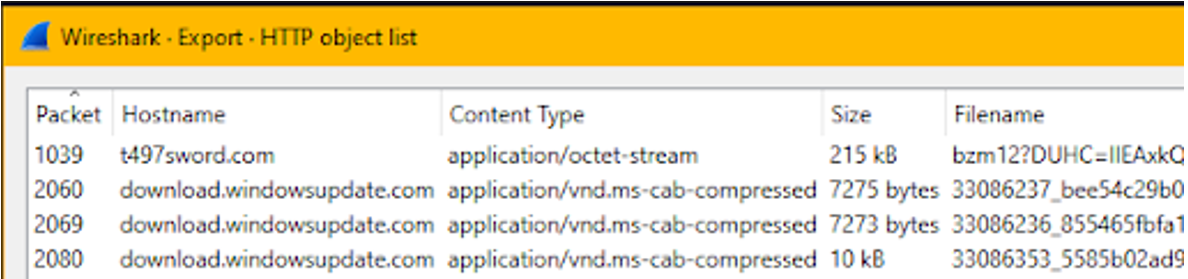
On Linux, we can type sha256sum <malware>, and Get-FileHash <malware> in Powershell. We could also analyze the malware manually with or throw it to a sandbox, but we should never upload a non-public sample to a public sandbox.
The hash of the downloaded file is:
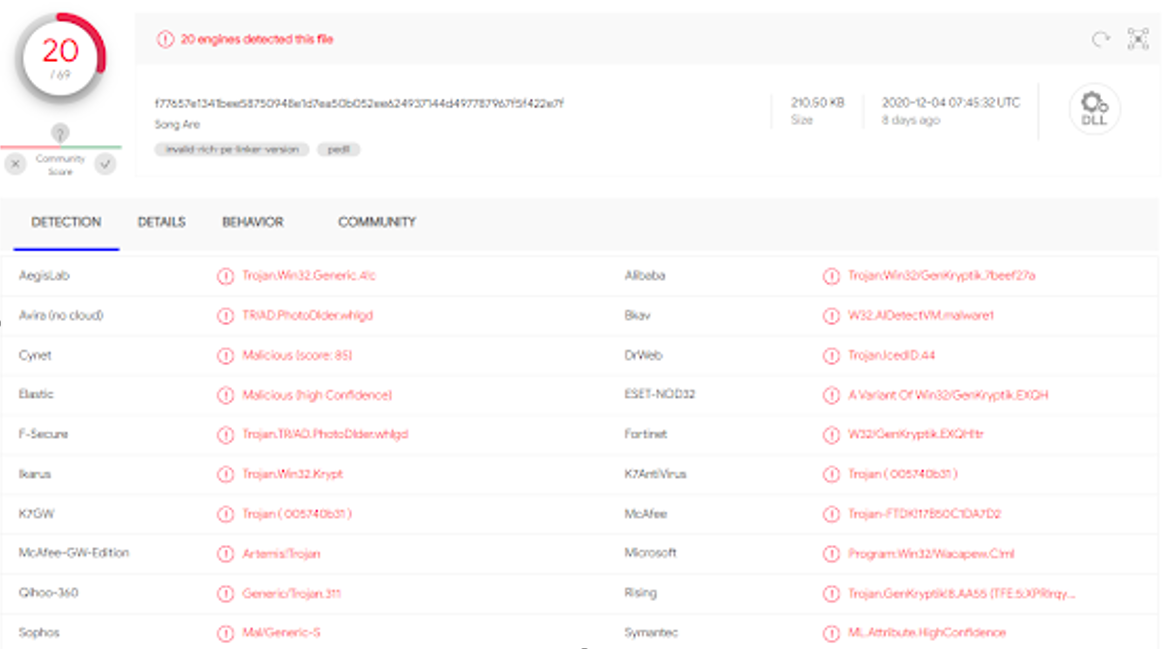
F77657E1341BEE58750948E1D7EA50B052EE624937144D497787967F5F422E7F
And it’s a known threat in VirusTotal.
7. Which two IP addresses and associated domains have HTTPS traffic with “Internet Widgits Pty” as part of the certificate data?
Checking the traffic alerts we can see two matches:
Count:1 Event#3.3771 2020-12-01 23:42 UTC
ET POLICY OpenSSL Demo CA - Internet Widgits Pty (O)
167.71.138.137 -> 10.12.1.101
IPVer=4 hlen=5 tos=0 dlen=1342 ID=0 flags=0 offset=0 ttl=0 chksum=30842
Protocol: 6 sport=443 -> dport=49804
Seq=0 Ack=0 Off=5 Res=0 Flags=******** Win=0 urp=25828 chksum=0
Count:16 Event#3.3779 2020-12-01 23:44 UTC
ET POLICY OpenSSL Demo CA - Internet Widgits Pty (O)
206.189.56.140 -> 10.12.1.101
IPVer=4 hlen=5 tos=0 dlen=1342 ID=0 flags=0 offset=0 ttl=0 chksum=41729
Protocol: 6 sport=443 -> dport=49813
Seq=0 Ack=0 Off=5 Res=0 Flags=******** Win=0 urp=49248 chksum=0
Now we can filter like this:
ip.dst_host == 167.71.138.137
ip.dst_host == 206.189.56.140
Let’s take ALL the domains that match. So the two IP’s (and associated domains) that we want are:
167.71.138.137 woodenbruus.cyou
206.189.56.140 rockercastle.bestm
206.189.56.140 moviecastle.club
206.189.56.140 wendi4kcash.top
8. Based on the alert for CnC (command and control) traffic, what type of malware caused this infection?
The alerts found a match, but we can also analyze the malware manually or in some sandbox (as the sample is already public).
The alert says:
Count:6 Event#3.3778 2020-12-01 23:44 UTC
ETPRO TROJAN Observed IcedID CnC Domain in TLS SNI
10.12.1.101 -> 206.189.56.140
IPVer=4 hlen=5 tos=0 dlen=224 ID=0 flags=0 offset=0 ttl=0 chksum=42847
Protocol: 6 sport=49813 -> dport=443
Seq=0 Ack=0 Off=5 Res=0 Flags=******** Win=0 urp=51002 chksum=0
We can determine that the malware could be IcedID.
Conclusions
The computer DESKTOP-NATURAL (10.12.1.101) contacted with the domain t497sword[.]com from the Windows account fabulous.dale, downloading a sample of IcedID, a banking trojan on Tuesday 2020-12-01 at 23:41:42 UTC.
We can now burn the infected host and give the IOC to our BlueTeam to contain this incident:
5.44.43[.]72
167.71.138[.]137
206.189.56[.]140
t497sword[.]com
woodenbruus[.]cyou
rockercastle[.]best
moviecastle[.]club
wendi4kcash[.]top
17b50c1da7d23d686fccfa8de3d27a3a
802c099a8a8f21f6e5cecc5c946f2cd52672c15e
F77657E1341BEE58750948E1D7EA50B052EE624937144D497787967F5F422E7F
