In this article we are going to analyze, gut and customize a little screen-locker (a member of ransomware family that locks the machine without encrypt the data). This is a clumsy but effective sample that we will alter to create our own ScreenLocker.
SSHBOT, the cr*ppy ScreenLocker
SSHBOT, also known as P4YME, is an old and unsophisticated malware from ransomware family.
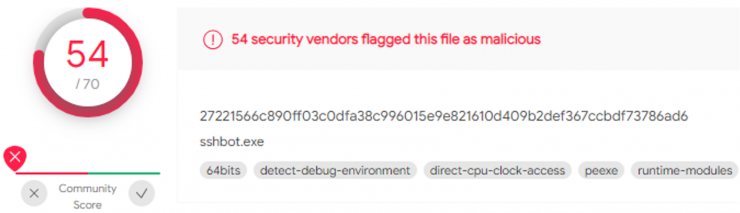
We will use a public sample submited to VirusTotal, where is detected by 54 Anti-virus:
When executed, it restarts the machine and shows this message:
[Read more…]
