Within the Windows universe there are countless features and details that, given their magnitude and depth, could in turn make up multiple universes in which to wander, learn and, above all, get lost.
In today’s article we are going to take a break from Windows Security Identifiers, hoping to reveal (or remind) some of the possibilities it offers us. First, a bit of theory.
What is the SID? The SID (Security Identifier), briefly explained, is the equivalent of our National ID Card. That is, Windows generates a unique and unalterable SID for each of its entities. An entity is understood as everything that can be authenticated by the Operating System (users, groups, processes, etc.). Ultimately, thanks to this mechanism, the domain user Paco will forever have his own identifier, as will the group of Domain Administrators.
With regard to security groups, Windows decided to establish a set of SIDs (Well-known SIDs) to establish a common identification criteria for them. For example, in the case of the Domain Administrators group, the SID follows a pattern that begins with S-1-5-21 and ends with the sequence 512. Based on this information, an example SID of a group of Domain Admins could be the following:
S-1-5-21-3237368166-3349108251-301524939-512
In all SIDs, the intermediate numerical sequence follows the pattern xxxx-yyyy-zzzz, whose value identifies the domain of the organization.
Now that we know a little more about some basic aspects of SIDs, what good does it do us from a security point of view?
First of all, and thanks to the support of the wonderful Windows EventID 4728, we may be able to record when a user has been added to an interest group, such as the global group of Domain Administrators:
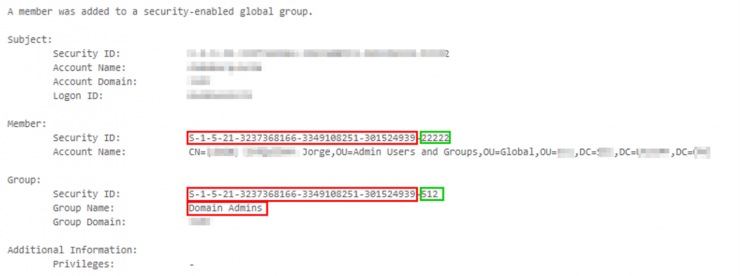
Although it is true that this fact could have been registered thanks to the name of the “Domain Admins” group, it could be that, at some point, someone internal to the organization or an attacker changed the name of said group. It’s a long shot, yes, but you never know these days :)
From the previous image, we can also identify the SID of the user that has been added to the Domain Administrators group:
S-1-5-21-3237368166-3349108251-301524939-22222
Therefore, and secondly, if we are able to register each of the SIDs that identify the most relevant user accounts of the organization to be protected, we will be able to carry out an exhaustive monitoring of their behavior much more precisely.
For example, we will be able to continue monitoring their activity even if an account name change occurs (although our faithful ally EventID 4781 should be useful for detecting such an event).
Third, for a forensic audit, it could be interesting to look for specific traces of a user by their SID instead of by name, since in the event of a change of name, in addition to a large amount of data to be analyzed, we could miss this fact, thus losing traces of potentially decisive actions for the investigation.
Fourth and last, in the face of an expert report, and in case of having to make any mention of any Windows entity (remember that they can be groups, user accounts, processes, etc.), we could reference its SID, given that we now have the assurance that it serves as a final identification.
In short, the SID feature can be useful to be sure that each action has an owner, no matter how much it may change its appearance.
