This post has been elaborated together with Alex Alhambra Delgado.
Since 2020, many changes have been made in the way we interact with each other, as well as with computer systems. In the wake of the pandemic, all companies had to upgrade their network infrastructures to provide better performance, speed and availability, given the large amount of work that suddenly had to be done remotely.
In the same way, companies needed a way to monitor all their processes remotely, in order to reduce travel and the potential exposure to viruses. In this situation, all types of industries took advantage of the benefits of the IoT (Internet of Things), which provided a new way to control the processes of a company remotely.
Likewise, a large number of sectors benefited from IoT in its industrial component (Industrial Internet of Things or IIoT) to access and collect data, or take control of a wide variety of devices. Some of the best-known cases of IIoT are, for example, surveillance cameras. We can monitor the status of a plant through sensors, gather GPS location of mechanical parts or employee brigades, remotely open or close doors, or control the status of a patient in a hospital through the use of wearables.
This last case, with all the COVID-19 tsunami that came in 2020 and everything we are still living since then, is extremely alarming considering the number of devices that can be connected to the internet in a hospital: blood pressure, heart rate, blood glucose levels, drug delivery and other hospital management and supplies.
A few days ago the news came out that the Hospital Universitario Torrecárdenas, in Almería, had implemented a system to control the stock of medical gas in the hospital using IoT technologies (in Spanish), in order to monitor the status of the oxygen cylinders and their locations. The cylinders communicate with the system, reporting their location and capacity level. This way you can have a real-time picture of the status of all the oxygen cylinders and their location to know where there are more than enough, and where there are none.
However, what if a malicious actor were to break into that system and modify the values to, for example, show that the cylinders are fuller than they really are? It could cause a serious problem for patients and clinicians.

Not only that, but in a hospital we can find other types of IoT devices less “trendy”: IV (intravenous) pumps are the most widely used IoT device in hospitals, accounting for 38% of the equipment in a hospital. Being such an important healthcare tool, an attack against these pumps could cause serious harm to a patient, including death.
Of course, with the increased use of such devices, the risks are also increasing. In the cybersecurity industry we always hope that, as time goes by and the use of new technologies increases, greater security measures will be taken. But this is not always the case, and IoT is no exception.

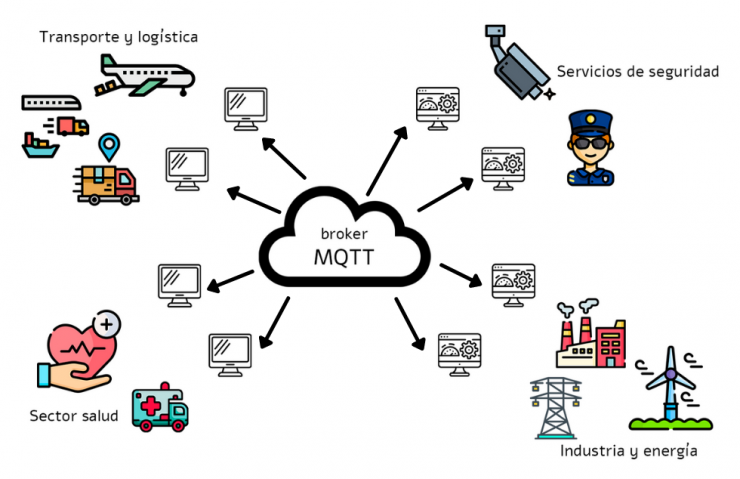
In the world of the Internet of Things there are many protocols, such as Zigbee, LoRa, even Bluetooth, but the one that probably takes the lion’s share of the market is MQTT, which we already mentioned in a previous post. This protocol is tremendously useful, given its ease of implementation and its low power and resource consumption. However, it also has serious security flaws.
We must not forget that MQTT is a protocol created at the end of the last century, and that today there are means and threats that were not so widespread then. It is a protocol that lacks security, so we need to rely on other systems to support it.
The protocol requires at least two devices to be functional: on the one hand, the device that publishes or subscribes on the network to the messages published by others, and on the other hand a centralized node or broker, used to guide which messages should reach which devices. Indeed, the broker is the heart of the protocol; if it is breached by an attacker, he could even execute arbitrary code on any device connected to it, since he has complete visibility over all other computers. Moreover, it is not only the protocol itself that is vulnerable, but also the applications used to implement it.
A few days ago Kaspersky published in its report that, over the course of 2021, 33 vulnerabilities related to the MQTT protocol or its applications had been discovered, of which 18 are of critical or high severity. This is an increase compared to the 10 that were detected in 2020. Of course, to this must be added all the vulnerabilities that exist in the devices themselves, as could be those mentioned by Kaspersky: Qualcomm Snapdragon, of which 147 vulnerabilities were discovered in 2021 alone.
Going back to MQTT vulnerabilities, those reported by Kaspersky as critical or high could allow an attacker to obtain sensitive information, as well as modify such records or perform denials of service, without requiring too high a level of expertise, nor too high a level of privilege. Worst of all, none of the reported vulnerabilities have been patched yet.
It is extremely important to try to bastion all infrastructures that are critical for an institution, even when there are no fixes for the vulnerabilities. In cases such as MQTT, other measures should be applied to strengthen its security, as well as that of the rest of the systems. A door can be opened if an attacker puts time and effort into it, but if we put in a few more doors, the chances of someone opening them all are greatly reduced.
References:
- https://acoustic-iot.webs.upv.es/2019/06/27/industrial-internet-of-things-iiot/
- https://securelist.com/telehealth-report-2020-2021/105642/
- https://threatpost.com/unpatched-security-bugs-medical-wearables-patient-tracking-data-theft/178150/
- https://hitconsultant.net/2022/01/25/critical-medical-device-risks-threaten-hospital-security/#.YgPnM_iCGUk
- https://www.trendmicro.com/vinfo/es/security/news/internet-of-things/mqtt-and-coap-security-and-privacy-issues-in-iot-and-iiot-communication-protocols
