We left the previous article with many gaps in the mail coverage from both the CEO and CFO of the MINAF. A first (and above all) quick solution is to use the MessageTracking logs. As we have already mentioned, MessageTracking is a high-level Exchange log that provides us with some basic data about the message (origin, destination, date and subject) along with some low-level identifiers (of which we will tell something in due course since they will be fundamental in our investigation).
To give you an idea, this is what a MessageTracking log (that we have minimally adapted) looks like:
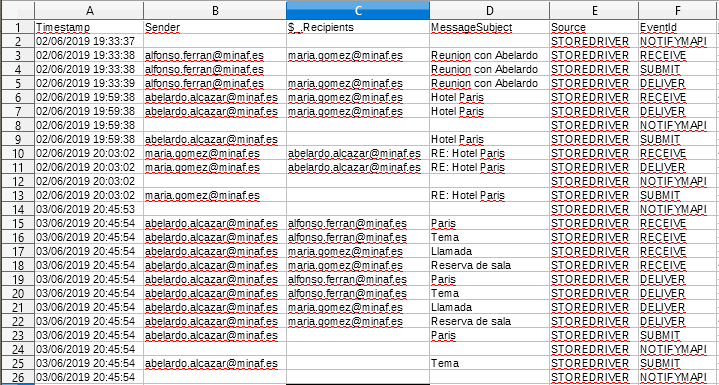
If we open the log and take a quick look at it, we find a wave of messages (about 1000) quite worrisome:
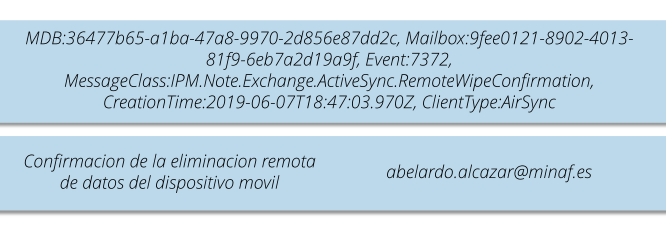
Apparently someone ordered the remote deletion of Abelardo Alcázar’s mobile device, something that can be done from Exchange if the terminal is configured correctly (very useful in case of theft or loss, since we do not require a remote management solution for mobile terminals or MDM).
This log agrees with Abelardo Alcazar’s statement, coinciding with the dates (remember that in Spain in summer we are at UTC + 2, so 18.47h UTC becomes 20.47h Spanish time).
We write down this detail and we are going to search in the log the emails sent supposedly on June 7. Indeed, it seems that they have gone through the Exchange:
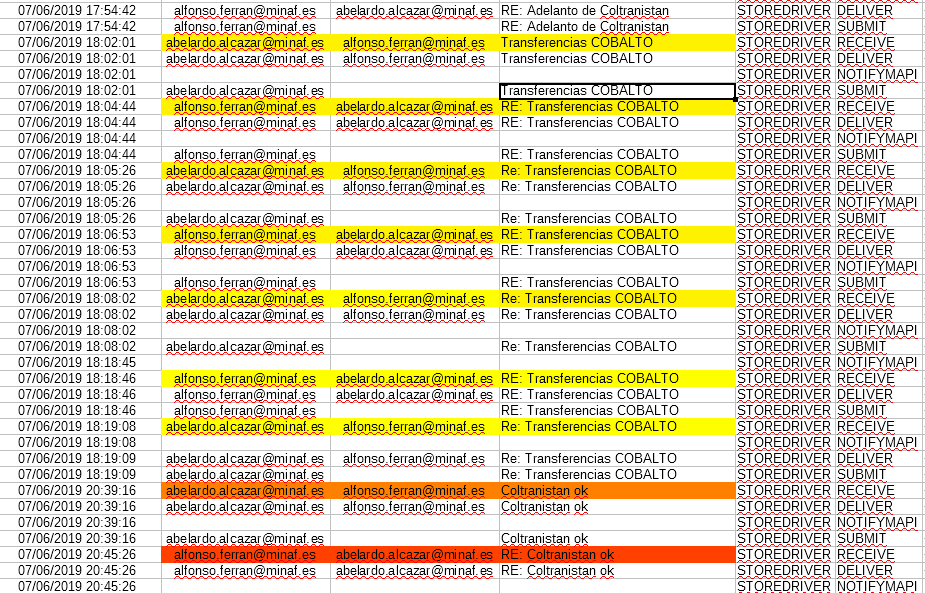
(Again, the dates are in Spanish time, that is, UTC + 2). If we look closely, we can see the chain of messages started by the CEO at 18:02:01 with the CFO, ending at 18:19:08 (messages in yellow). Abelardo Alcázar says that he did not send those messages.
He does claim to have sent the message in orange, which was (in his own words) to inform Alfonso Ferrán of the successful closing of the agreement. Alfonso’s reply (red, sent at 20:45:25) was never received by Abelardo Alcázar, possibly because at that time his terminal had been remotely deleted.
It is clear that we need access to these “ghost” emails, and that the mailboxes in the users’ laptops will be of little uses. Fortunately for us, we have recovered the mailboxes directly from the Exchange. And even better, when we exported them from Exchange, we got hold of the “Recoverable Items” folder.
Everyone knows that when a file is moved to the trash, it can be recovered. And when the trash can is emptied, the file has been “permanently” deleted (unless a secure deletion program has been used, forensics have tools to make it not so “permanent”).
Something similar happens in Exchange: a user can delete an email (move to the trash) and retrieve it without any problems, but when the trash is emptied the user no longer has access to it (with the added bonus that, since it is usual to have the mail synchronized with Exchange, this change is applied to the rest of the user’s devices).
What is not so common anymore is an Exchange folder called “Recoverable Items“, accessible only by the Exchange administrator, that saves EVERYTHING deleted by the user: emails, contacts, appointments, etc. for a maximum of 14 days or 30Gb (whatever comes first).
When we exported the mailbox from the Exchange, we got that folder, so we can open it with Kernel Outlook PST Viewer. First of all, we verify that the email exchanges between the CEO’s (let’s trust Abelardo Alcázar for now) and the CFO existed, were deliberately deleted and the trash emptied:
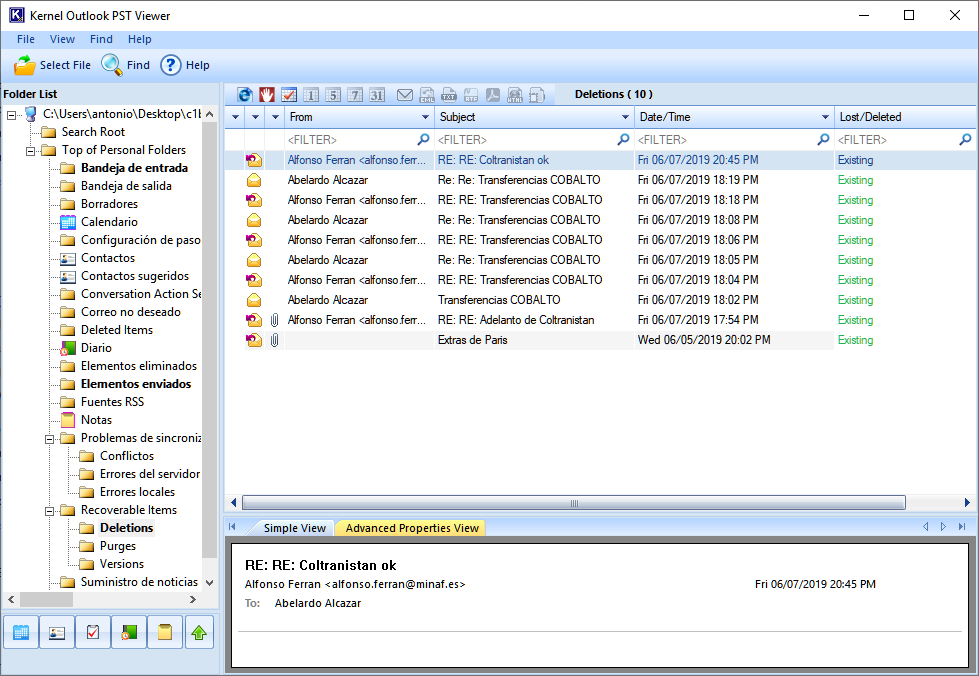
This email exchange is like watching a train wreck in slow motion: you know from the first moment what is going to happen, and there is nothing you can do to prevent it.
1. In the first email, the request for an international transfer (referring to an account called COBALTO, something apparently internal to the company).
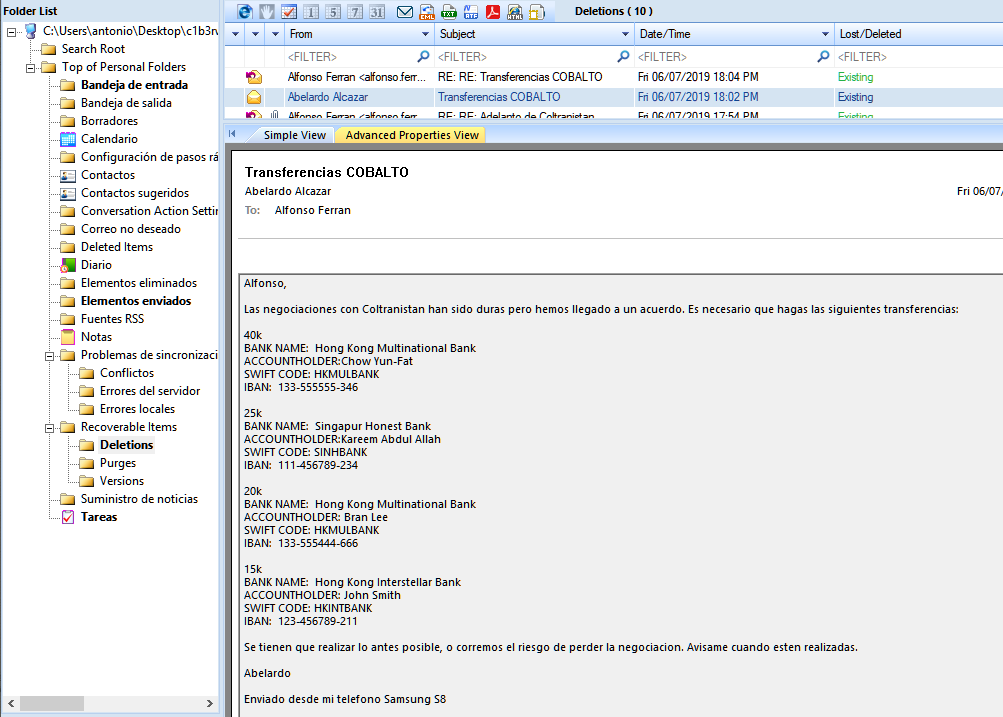
2. The CFO responds anxiously to the magnitude of the transfers:
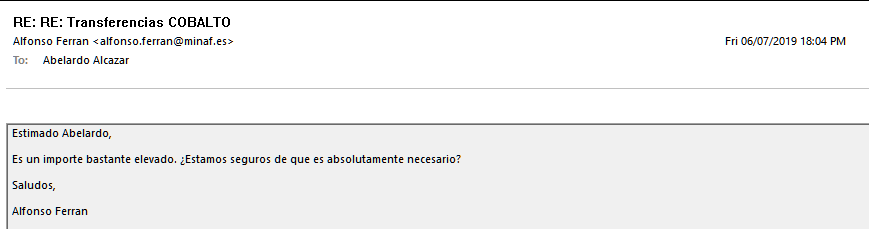
3. The answer is almost immediate and categorical:
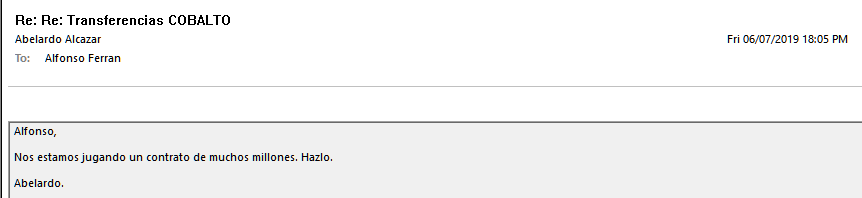
4. El CFO continues complaining about the transfers:
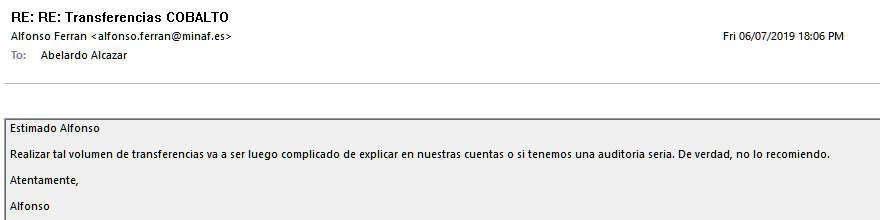
5. “COBALTO” looks like a “special” account used in MINAF for “special” matters. As we are not financial auditors, nor is there any flagrant proof of a crime, it is not our business. What we are interested in is the clear and decisive answer.

6. The CFO eventually gives up and makes the transfers:
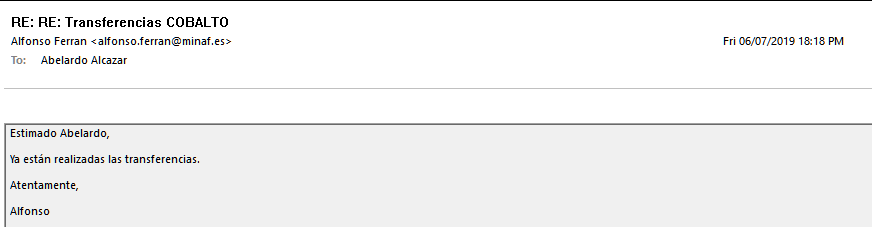
7. And receives a succinct message of thanks from the CEO:
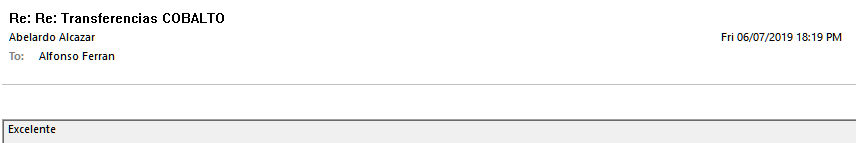
8. It is totally clear to us what has happened, but all that remains to be seen is the outcome of the tragedy, when the CEO Abelardo Alcázar sends a new message of “everything OK”:
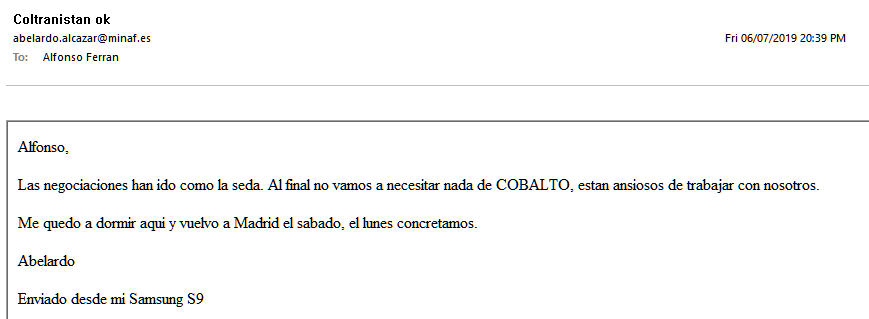
9. And the CFO’s panic response, which CEO Abelardo Alcázar claims he never read:
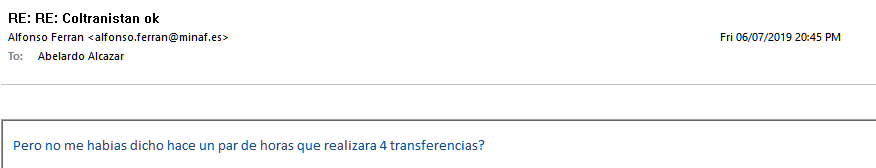
With these emails we have a reasonable working hypothesis: the attackers have managed to access the MINAF CEO’s email, and it is more than likely that they have studied his email and agenda, looking for the right opportunity to strike.
The analysis of the rest of the emails in the CEO’s mailbox allows us to draw these additional conclusions:
- There are previous emails that refer to a bank account called COBALTO. This account seems to have been used to make transfers potentially “questionable”.
- There are emails about the negotiations with Coltanistan and the trip to Istanbul.
- The attackers have modeled their emails in the style of Abelardo Alcázar, copying his signature and writing in a concise and direct language.
The Exchange mailboxes have revealed a part of what happened.
But if we want to learn more about the incident, we will have to delve into the mysteries of the EventHistoryDB… in the following article.

“In the following article…” OMG this is worse than the tv series.
I could barely see through the haze.
Kind regards,
JS.
Sorry, when it comes to publishing we are more HBO-like, rather than Netflix-like…