Maritime transport is a fundamental pillar of the global economy and, like any system adopting new connectivity technologies, it is subject to cybersecurity risks. In the article “New cybersecurity requirements in shipbuilding: implications in the engineering process and designs of new ships“, we commented on the increasing connectivity of new ships, as well as the low maturity of cybersecurity in this area and the common problems encountered in their systems. These characteristics, together with the increase in cyber-attacks, are driving the creation of mandatory standards and certifications for new ships. However, the problems are not just procedural. Let us look at one of the most important technical aspects, maritime communication protocols.
To recap the previous post, the common issues in the maritime domain lie in factors such as reliance on network isolation and physical security, coupled with long system lifetimes and a focus on availability. These characteristics are reflected in the way ships are designed and operated, from general aspects such as architectures to specific aspects such as communication standards. In this article, we analyse the most commonly used maritime protocols today in terms of their security and the risk of being affected by some of the most common types of cyber-attack.
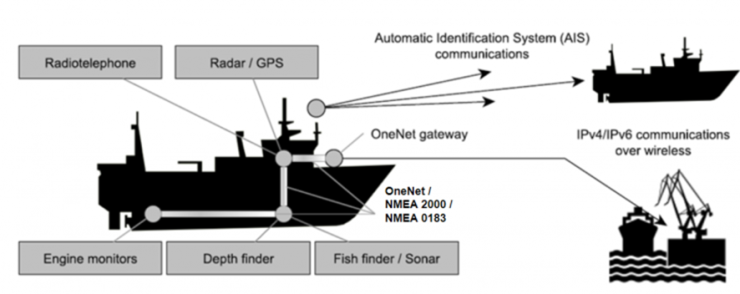
Maritime network protocols are the communication standards that define the rules, syntax and procedures for internal communication between ship systems and ship-to-ship communication. As in other fields, international associations such as NMEA (National Marine Electronic Association) have worked to establish standards that are used by all manufacturers.
These protocols are used to communicate between the various systems on board, such as the VHF radio, chartplotter, radar, sonar and echo sounder. Standard protocols such as NMEA 2000 define the communication mechanisms between devices to ensure compatibility between equipment from different manufacturers.
However, while there is a great deal of literature and research on conventional protocols, such as TCP/IP, little research has been done on maritime protocols, despite the fact that they are widely used “across the seven seas”. It cannot be overlooked that the maritime sector is a frequent victim of cyber attacks (attack on the port of Nagoya, Japan, attack on the port of Shahid Rajaee, Iran), it is essential to make further progress in ship security.
In this vein, the Department of Computer Science at Western Washington University has conducted theoretical research that opens the door to analysing these protocols and their vulnerabilities (see Marine Network Protocols and Security Risks, by Ky Tran, Sid Keene, Erik Fretheim and Michail Tsikerdekis). We have built on this research to show where maritime communication standards stand in terms of cybersecurity. We begin by analysing the most commonly used maritime protocols on commercial and civil vessels, and their vulnerability to some of the most common cyber-attacks. A comparison of these protocols with TCP/IP is then presented for the reader’s reference.
Source: https://mdpi-res.com/d_attachment/jcp/jcp-01-00013/article_deploy/jcp-01-00013.pdf?version=1618385190
NMEA 2000
This open source protocol is a standard that is widely used on all types of vessels and is based on the CAN bus protocol – J1939 (click here for more information on this protocol and its weaknesses). This protocol, like CAN, allows communication between devices connected to a single communication bus. All devices receive all messages and decide whether to do something with the information or ignore it.
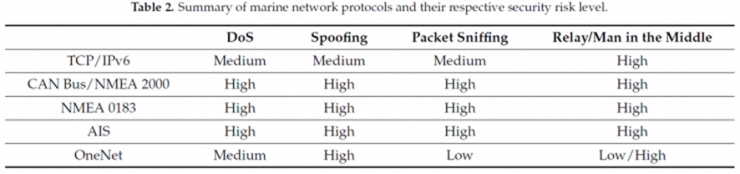
The NMEA 2000 protocol is designed for robustness in terms of transmission error detection, packet forwarding acknowledgement and reduced latency. However, it does not include any security mechanisms. For this reason, it is a protocol that is highly vulnerable to all the types of attacks analysed.
– DoS: Due to its limited bandwidth (250 Kbps), it is vulnerable to packet injection, which can easily flood the network with false high-priority messages, blocking all other communications.
– Spoofing: The only way to identify which node is sending the message is the PGN code inserted in each packet. An attacker could spoof the identity of a node by simply copying this parameter, which would allow any communication coming from that device to be spoofed.
– Packet sniffing: As this is a bus protocol, all messages are sent in broadcast to all nodes. This, combined with the fact that it is not an encrypted protocol, makes this attack trivial. Nowadays, tools such as Wireshark or SavvyCAN make it easy to analyse this type of communication.
– Replay/MiTM: Again, as a bus protocol without security protection, if a device is connected between a node and the rest, it is easy to modify the communication to/from the node, spoofing the information injected into the network.
NMEA 0183
This is another open source protocol commonly used on boats, in this case for unidirectional data transmission. This means that the networks consist of a transmitting device and one or more receiving devices. Data is transmitted as ASCII strings over a serial cable (RS-232 or RS-422), although it can also be used via UDP in an Ethernet network. Although this protocol is the predecessor to NMEA 2000, it is still widely used on commercial vessels.
Again, this protocol does not incorporate any security measures and is therefore highly vulnerable:
– DoS: Due to its low bandwidth (9.6 Kbps), it is vulnerable to this type of attack. An attacker could easily saturate the network and block communication.
– Spoofing/packet sniffing: By transmitting data in ASCII format without any encryption, both attacks are trivial. An attacker connected to the network could, for example, inject false GPS readings.
– Replay/MiTM: Again, without security protection, it is relatively easy to intercept and modify communications, especially when using the protocol over UDP.
AIS
AIS (Automatic Identification System) is a tracking system used by ships’ transceivers for vessel traffic management. This protocol is used to communicate and broadcast metadata to other vessels via VHF. This metadata includes information such as name, coordinates and other navigational parameters. In general, these messages are transmitted via UDP port 5321.
This protocol does not include any security measures, although there is a less widely used version that encrypts the traffic (EAIS). In terms of vulnerability to various attacks:
– DoS: The limited bandwidth (9.6 Kbps) combined with specific characteristics of the protocol make it extremely vulnerable to this type of attack. For example, an attacker could deny the transmission of messages by repeatedly and synchronously sending a command to the victim to delay the retransmission of messages for a specified time.
– Spoofing: In the absence of security measures, vessels using this protocol can be easily “spoofed”. For example, by creating a “dummy ship” that appears on the receiver’s radar.
– Packet sniffing: As it has no encryption and is usually used in broadcast mode, it is trivial to intercept and read the transmitted data.
– Replay/MiTM: It is relatively easy to intercept and modify the communication between two ships due to the lack of protection mechanisms. Such an attack could, for example, alter the real position of one ship in the eyes of the other, causing confusion and danger.
OneNet
It is a new communication standard based on NMEA 2000. It is designed for communication over maritime networks via IPv6, while maintaining backward compatibility with its predecessor protocols via gateways. Each device must run a OneNet application to communicate with the network.
This protocol allows a “secure mode” where an encrypted tunnel is used to transmit information. In this case, this tunnel must be established using the Anonymus Diffie-Hellman method, with the device “in charge” of security and access to the network, known as HID. When this secure option is enabled, each device must obtain a certificate (issued by specific software) in order to access the network. In terms of vulnerability to various attacks:
– DoS: The bandwidth supported by OneNet (Ethernet) networks is much higher than that of the previously mentioned protocols, making them less susceptible to this type of attack.
– Spoofing: When security measures are enabled, communication is through an encrypted tunnel, which reduces the vulnerability to these attacks. However, an attacker could spoof an HID, causing the device to join a “fake network” and obtain the information.
– Packet sniffing: If the communication is through the encrypted tunnel, the content cannot be intercepted and read by an attacker. Again, as in the previous case, this protection can be bypassed.
– Replay/MiTM: As the Anonymous Diffie-Hellman method does not authenticate the shared key, an attacker could spoof the connection at the beginning of the process, making it vulnerable to MiTM attacks. However, the protocol has protection against replay attacks because messages are numbered with a code that cannot be reused.
Finally, a comparison is made between these maritime protocols and the TCP/Ipv6 protocol. The latter has been chosen as a reference to contrast the similarities and differences between the two protocols.
Source: https://mdpi-res.com/d_attachment/jcp/jcp-01-00013/article_deploy/jcp-01-00013.pdf?version=1618385190
In conclusion, ‘traditional’ maritime protocols start from a similar problem to other industrial protocols: they focus on the availability and integrity of communications, not on confidentiality. They are designed for use cases, not misuse. There is a strong reliance on network isolation, physical security and security by obscurity to protect against cyber-attacks. However, connectivity solutions for all types of systems are becoming more common. For example, for remote maintenance. In this sense, it is only a matter of time before a network is no longer “isolated”.
Although progress is being made in the area of cyber security, with new standards such as OneNet being proposed, there is still a long way to go. On the one hand, industry constraints limit the security measures that can be implemented, making even new protocols vulnerable to certain attacks by design. On the other hand, replacing legacy communication protocols is an arduous, long-term task that must involve manufacturers, integrators and owners.
