In today’s cybersecurity landscape, the concept of Threat Hunting or the proactive pursuit of cyber threats begins merely as soon as an actor establishes their foothold in an organization, limiting the detection capabilities and overall understanding of a campaign that a hunter may have regarding the offensive capabilities of their adversary. In this context, I propose and intend to tackle these challenges with two main tactics that hunters can employ to disrupt the offensive operations of state actors and non-state actors more effectively: Horizontal Hunting and Vertical Hunting, while integrating elements of persistent engagement to enhance visibility.
Initially, as is usual in hypothesis-driven Threat Hunting, we formulate hypotheses based on intelligence feeds to conduct proactive searches within our environment. However, this approach often lacks precision in both operational capabilities and strategic insight into the adversary’s intentions. This can be attributed to various factors, including:
- Limited intelligence collection capabilities
- Technical expertise of both hunters and Threat Intelligence teams
- Uncertainty about the proactivity of the hunting team
- Urgency to deploy detection capabilities (which may not always be effective) or publish articles by the Threat Intelligence team.
Horizontal and Vertical Hunting aims to address these shortcomings by comprehensively understanding the adversary’s offensive capabilities and enhancing detection capabilities for both hunters and Threat Intelligence analysts.
Next, let’s define Horizontal/Vertical Hunting to elucidate the concepts discussed in this article.
Horizontal Hunting involves proactively searching for offensive capabilities employed by an actor’s campaign in open sources (OSINT), enabling the identification of artifacts or architectures used by the adversary. This facilitates the identification of additional artifacts, victims, industries, and adjustments to our detection capabilities. Generally, Hunters predominantly focus on known Techniques, Tactics, and Procedures (TTPs) as those outlined in frameworks like ATT&CK, such as “Execution – Command & Scripting interpreter.” However, additional elements including malware “pdb” or TLS negotiations by a server may not be explicitly covered in ATT&CK but provide more precision and aid in identifying unique characteristics of certain artifacts, thereby detecting other artifacts used in the same campaign and understanding its victimology.
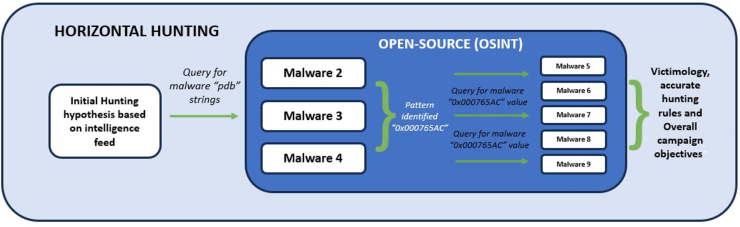
Horizontal Hunting provides an advantage in identifying the adversary’s capabilities while enhancing the detection capabilities of the Threat Hunting team. Moreover, it offers an additional avenue to proactively intervene and preemptively disrupt a campaign before it unfolds.
On the other hand, Vertical Hunting involves direct interaction with the adversary’s Command & Control (C2) architecture. Successful Vertical Hunting requires the incorporation of a Persistent Engagement framework. Persistent Engagement is referred to as the efforts aimed at intercepting and halting cyber threats, diminishing the capabilities and networks of adversaries, and continuously reinforcing our infrastructure.
Vertical Hunting aims to identify offensive capabilities from their source, including adversary architecture, proxy entities, victimology, and objectives. It employs two elements: Active Engagement and Sustained Interaction. Active Engagement involves disruptive actions to targets, preventing future attacks, while Sustained Interaction includes mechanisms such as Exploitation and Active Collection to escalate offensive capabilities and gather information from ongoing operations.
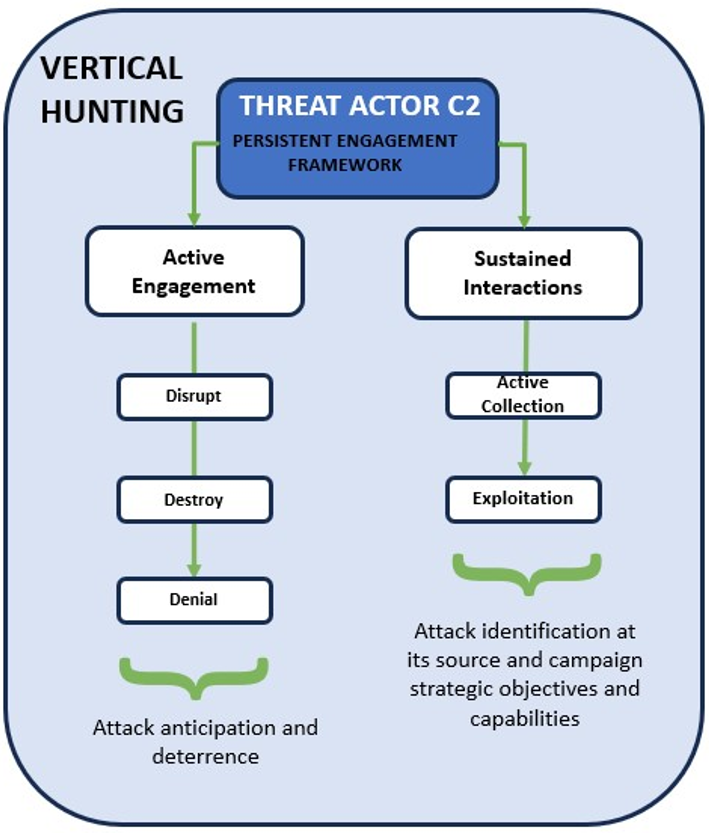
Therefore, Vertical Hunting enables both Cyber Threat Intelligence and Threat Hunting teams to adopt a proactive stance, surpassing mere detection to disrupt and identify adversaries’ campaigns and objectives.
In summary, Horizontal and Vertical Hunting, coupled with Persistent Engagement, empower proactive measures beyond conventional boundaries to anticipate, detect, and disrupt state and non-state actor campaigns. This approach allows Threat Hunting teams to proactively deter threats before they materialize, enhancing overall cybersecurity resilience.

Speak Your Mind