The world of cybersecurity is becoming increasingly complex and challenging. With each new threat, from harmful capabilities such as malware or 0 days, to changes in infrastructure, having moved from on-premise to hybrid or full-cloud environments, there is an urgent need for schemes and methodologies to help address these adversities. We not only seek to minimize the impact of any threat, but also to achieve a level of detection and neutralization with which we feel confident, although this can often give a false sense of security.
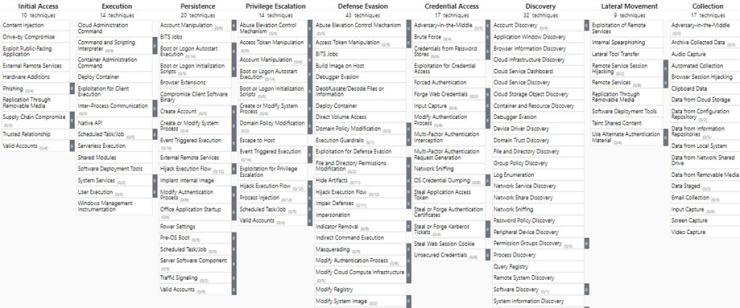
Today we find various schemes that help us understand and contextualize the modus operandi of hostile actors. From the widely recognized MITRE to the Malware Behavior Catalogue (MBC), through Microsoft Attack Kill Chain and Lockheed Cyber Kill Chain, these tools offer us a guide to understand and confront the tactics, techniques and procedures (TTPs) used by adversaries. Within this scenario MITRE ATT&CK is the most recognized scheme. Its matrix breaks down the different techniques, tactics and procedures (TTPs) used by hostile actors.