Articles in the series “Exchange forensics: The mysterious case of ghost mail”: [1] [2] [3] [4]
[Note: This is a fiction story, the characters and situations are not real, the only real thing is the technical part, which is based on a mixture of work done, experiences of other colleagues and research carried out. with the same technical dose but with less narrative, you can consult the video of the talk that the author gave at the 11th STIC Conference of the CCN-CERT here]
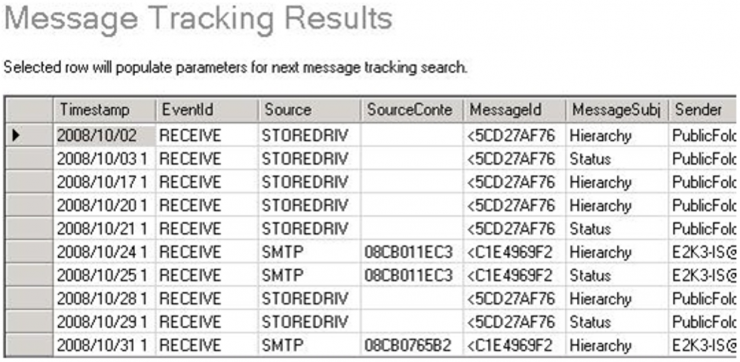
We return to the investigation of the incident by examining what our colleague had found in the OWA logs. If we gather all the information regarding the accesses made from the two IP addresses with the Firefox User-Agent, we find several patterns of interest:
[Read more…]