In this article we are going to learn about threat clustering carried out by Threat Hunting teams. But, first of all, let’s define some terms.
First of all, Threat Hunting refers to the art of proactively searching for and detecting cybersecurity threats hidden in an environment. It is a dynamic and strategic approach that allows defenders to discover and neutralize potential dangers before they escalate, making it an essential skill in today’s cybersecurity landscape.
Second, Threat Hunting analysts, also called Threat Hunters, need techniques to identify and track APTs and their activities. APT refers to an advanced, persistent threat that operates covertly and with malicious intent over an extended period of time. To accomplish their goals, APTs use sophisticated techniques, tactics and procedures (TTPs) to gain access to high-value networks and information systems, such as government, financial, military and other systems.
The identification of APT groups and their monitoring is essential for cybersecurity, as it allows the Threat Hunter to anticipate the actions of cybercriminals and take measures before it is too late, both detection and preventive, to protect systems and critical information. One of the mechanisms that Threat Hunters use to identify APT groups is precisely through threat clustering.
What does this strange term mean? Well, basically it is the pattern or series of actions that a particular APT carries out. For example, let’s say every time our friend comes to your house, he always rings the doorbell three times before entering. That single, consistent action of ringing the doorbell three times becomes a pattern of actions that allows us to immediately identify that it is our friend who is arriving, even before we see him, and not someone else.
Therefore, threat clustering allows Threat Hunters to identify patterns in the behavior of these groups, which in turn helps them to predict and prevent future attacks. On the other hand, they are very useful in achieving group-specific attribution, i.e. which group has been the perpetrator of a given attack, thanks to the fact that many APTs have their own pattern of behavior, as well as unique techniques, tactics and procedures (TTPs).
The next step is to identify what is needed to achieve APT threat clustering. First, we recommend reviewing, identifying and classifying all available forensic elements on the activities performed by each APT. For this, the Diamond Intrusion Model can be used, which could centralize the assessment on the following aspects:
- What are the results of the malware analysis and the attack methods used?
- What infrastructure has the malware used, and is there any pattern in the communications behavior?
- What targets did it select?
- What is the motivation for the attack?
But don’t panic, @Lector, there is already a lot of work in this field and we don’t have to start from scratch. For example, one of the most well-known APT clusters is the APT10 / Stone Panda group. This group is responsible for a number of attacks or activities against organizations around the world, ranging from government entities, technology companies and defense organizations. APT10 elements include the use of custom malware, the exploitation of zero-day vulnerabilities and the theft of intellectual property information.
Another example of a cluster is the APT32 / OceanLotus group, which targets government and business organizations in Asia, especially in Vietnam. Its elements include the use of spear-phishing techniques, remote access through compromised servers and the use of custom malware.
Still, there remains research work to be done by people who dare to enter this exciting world. Unfortunately, however, APT clustering takes a very long time. Why? Because the process to follow is long:
First, the promotion of these clusters starts from an incident in an organization, and this activity needs to be repeated until all or several elements of the Diamond Model match. Then, once the activities are identified, a UNC, i.e. Uncategorized Cluster (Mandiant) would be formed and then proceed to review which elements of these clusters overlap with known APT groups. This, in turn, has a major drawback that makes the matter a little more complicated, since it must be taken into account that each intelligence provider has its own telemetry, so that each element, within the attribution diamond model, will have different characteristics and names, and consequently, the attribution will also be different.
For example, in the following image you can see what would be the clustering of a single group from the perspective of different intelligence providers such as Microsoft, Mandiant, Proofpoint, etc. Each vendor has its telemetry, which varies depending on the size of the circle, and its own attribution. In addition, the further one circle is inside another, the more overlap there is in the elements of the attribution diamond model.
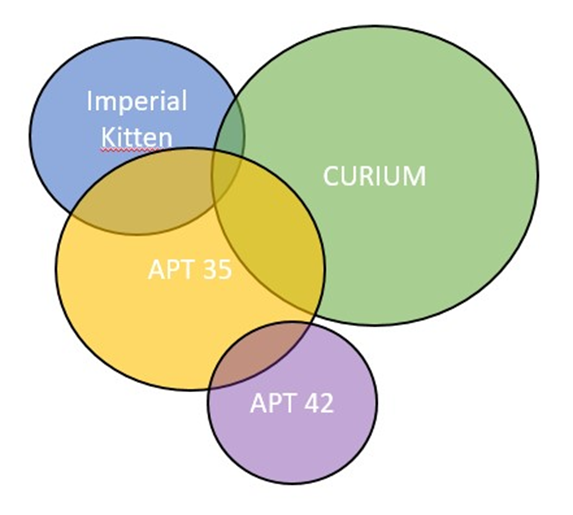
In this particular case, it can be seen that the green circle -attributed to CURIUM- has some overlaps with the blue and yellow circles -attributed to Imperial Kitten and APT 35- However, the former is related to Iranian groups, while the latter are related to Chinese groups. This, theoretically, is impossible because they overlap in aspects of the Diamond Model but not in group attribution. However, it does not mean that one supplier is right and the other is wrong, but rather that each uses different telemetry, analyzed differently and has therefore obtained different results.
In addition, clustering also takes advantage of possible OPSEC errors of some APTs or incidents of information exfiltration that have affected the groups – for example by a “Whistle Blower”.
Therefore, by grouping all this information together, in addition to our own telemetry, we can, firstly, attribute with a high level of reliability and, secondly, start to cluster the analyzed activity. The more information the Threat Hunter has on these clusters, the more it will be able to analyze their TTPs and their evolution. This will, in turn, allow him to improve the organization’s detection capabilities and, therefore, result in fewer threats and a higher level of overall security, which, after all, is what we are all trying to achieve.

Speak Your Mind