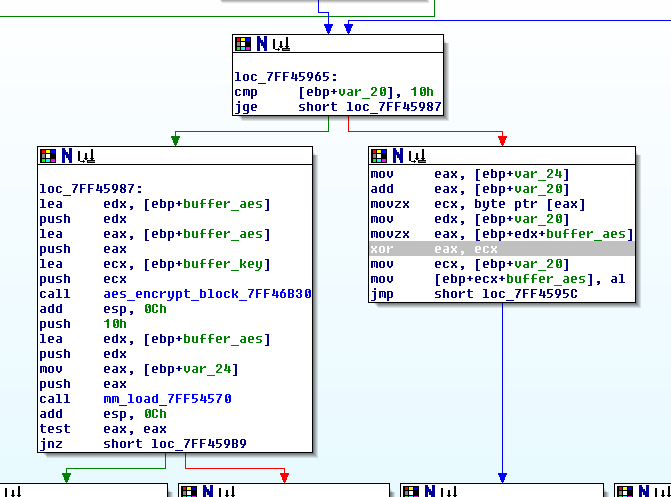
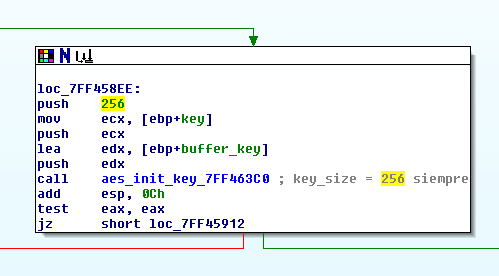
A few days ago we got the source code of the Haikai malware, which corresponds to one of the many implementations carried out by the continuous recycling of source code belonging to different IoT botnets. Although we have not identified any new developments compared to previous IoT malware versions, it has allowed us to obtain a lot of information on techniques, improvements and authors.
It should also be noted that, according to different records obtained, this botnet has been in operation for most of the last month of June.
In the following lines the code will be analyzed, as well as the possible attributions and the implementations not referenced in the execution thread, which allow us to guess that the code is mutating in different lines in parallel for the same function.
So let’s start by analyzing the structure of the files. [Read more…]

 The widespread use of devices connected to the network, such as cars, medical equipment, industrial controllers (PLCs), appliances, etc., has brought with it a new and extremely vulnerable landscape.
The widespread use of devices connected to the network, such as cars, medical equipment, industrial controllers (PLCs), appliances, etc., has brought with it a new and extremely vulnerable landscape.