Since smartphones installed in our lives, either for personal or professional use, one of the greatest fears is losing it. We store a great amount of sensitive information in this devices that can be potentially accessed by a malicious person. This problem is even bigger when it comes to professional smartphones, which have not only personal but also access to the corporate environment and information.
So what happens when you lose your mobile phone? If we have correctly hardened it, that will not be a major problem. The person who finds the device must know the code or the unlock pattern screen. In the best case, after N repeated attempts the device will wipe and no information will be compromised (full erase of user data). (Paranoid note: Do not leave footprints on the screen if we use a pattern to unlock the device).
And if we want to find it? Who knows, maybe no one found it and it still lays beneath the park bench. In this case we need third-party applications that allow us to locate the device. There are many of them, free and commercial, but we will describe briefly the most popular, although of course any reader contribution is obviously welcome.
Commercial applications
On one side we have the commercial applications, and every person must decide if the app is worth the price or not.
StealthGenie
This product comes from an American company that provides a product to perform a full trace of a mobile device with an application available for Android, iOS or Blackberry. However, you need to pay $99.99 per year. The basic version includes the following features:
- Call Log.
- SMS received / sent.
- Access the phonebook.
- Tasks and Calendar.
- History and Web bookmarks.
- GPS tracking.
- SIM change notification.
The ‘Platinum‘ version offers the possibility to listen to telephone calls among other options. This version ‘full-equipe‘ costs $199.99/yr. You can access a demo of the dashboard (or control panel) in the following link: http://demo.stealthgenie.com/dashboard
Cerberus
In the past we have already talked about Cerberus, as in the post regarding a case of “>malicious user that loses a mobile device on purpose (Spanish).
This application is available from € 2.99, with a lifetime license that allows you to control up to five different devices.
From the dashboard of Cerberus we have the following list of possible actions to control the device, among which is tracking through GPS.

This product is only available for Android smartphones.
Free applications
On the other hand, there are other free applications that allow you to track your mobile device. The features included are more limited than those offered by commercial solutions, but to some users they may be enough.
InstaMapper
This application only allows to track the device via GPS. Although free, next December 13th it will cease to provide this service, something that can be of interest for those users who are currently using it.
Prey
This is one of the solutions that most caught my attention, since from the begining it was a product to keep track of a computer (Windows or Mac OS X). Prey gradually expanded its range and now can be installed on Android, iOS and even Linux.
The advantages of this product is that there is a paid version ranging from $5 to $399 per month depending on the number of devices and functionality required. On the product page you can find more information on the plans.
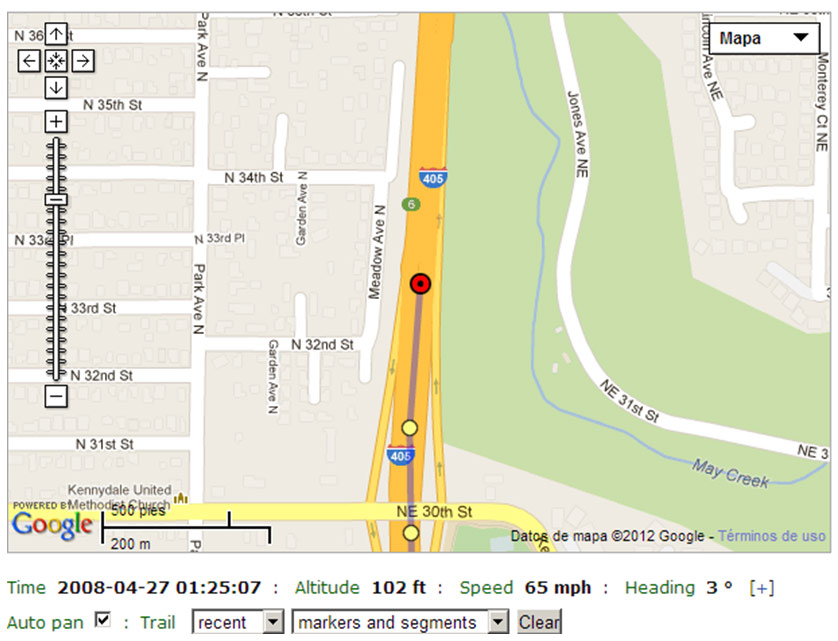
Below there is a screenshot of the dashboard on an Android device that has this product installed.

As you can see in the picture above, the geolocation feature is not enabled unless the device has been lost, which is one of the main differences it has with Cerberus.
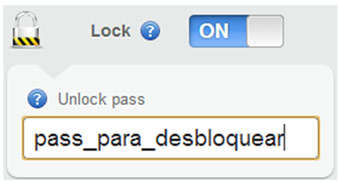
Another option to highlight is the locking of the mobile device with a password. In the moment that this feature is enabled (be the phone marked as lost or not) the device is blocked until the owner enters the password specified in the control panel, as shown in the image:
Plan B
What would happen if you lose your device without any of the above applications installed? As its name suggests, there is a plan B.
This application is available to download from Google Play and can be installed remotely on the device. We conducted a test setup and in minutes the application appeared correctly installed in the device.
Once installed, when the device gets GPS coverage it sends its coordinates to the Gmail account that’s associated with it.
This product is only available for Android smartphones.
Personal opinion
Getting into a more paranoid view, the application that best security and privacy offers (call it confidence if you want) is Prey, not only because it has a free version but because the trace options. Maybe it is not as complete as its competitors, but being an open source product has the advantage that the code is auditable and it can be verified that no unknown actions are performed without the user consent.
Of course, with this I want to re-emphasize the danger that we saw in the previous post about finding a mobile device on the street and using it in our daily tasks (or business, even more dangerous) without taking proper precautions.

 How much is our reputation worth? To respond to this issue we have to consider the relationship between reputation and success. And when I say “success” I mean achieving our objectives, both personal and professional. In certain groups, reputation is an essential element for its success or decline. We could include in that group people with public office as mayors, councilors, ministers, etc., but it also directly affects professionals from the private sector as actors, singers, designers and a long etcetera.
How much is our reputation worth? To respond to this issue we have to consider the relationship between reputation and success. And when I say “success” I mean achieving our objectives, both personal and professional. In certain groups, reputation is an essential element for its success or decline. We could include in that group people with public office as mayors, councilors, ministers, etc., but it also directly affects professionals from the private sector as actors, singers, designers and a long etcetera.
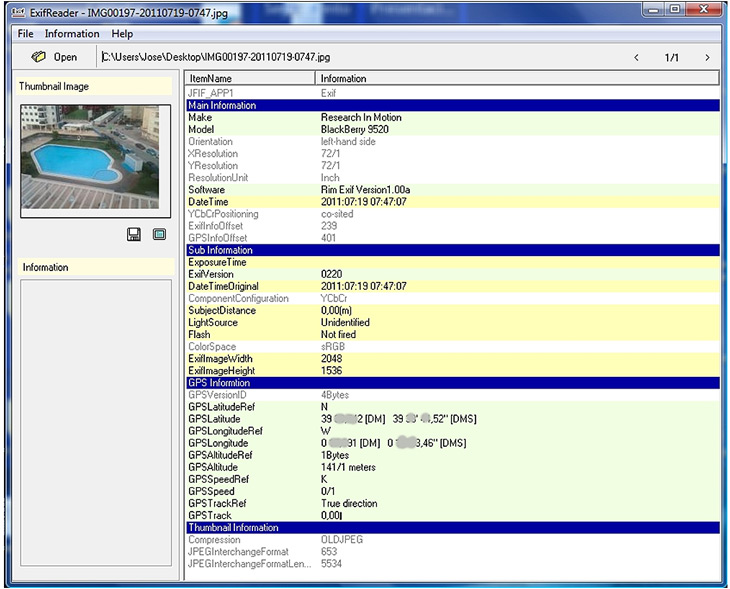
 A couple months ago, our partner Jose Vila talked about
A couple months ago, our partner Jose Vila talked about  A couple of weeks ago I saw
A couple of weeks ago I saw