What is YARA?
When speaking about malware detection, there are mainly three ways of determining if a file is malicious: signatures, heuristics and string signatures.
The most widespread in the antivirus detection systems is the signature based detection, i.e. based in the HASH of a file, check it against a signature database and see if this file has previously been detected as malware. This kind of signature is useless for the detection of unknown malware, and to evade this system you just need to recompile the code in a different system or change a single bit.
In order to try to stop these evasion methods, the heuristic method is usually the chosen one. This method relies on the behaviour of the executable file and, according to the actions that it performs inside the system, it decides if it’s dealing with a malicious file. The main issue of this method is that, as many legit programs perform suspicious actions, it can generate a big amount of false positives.
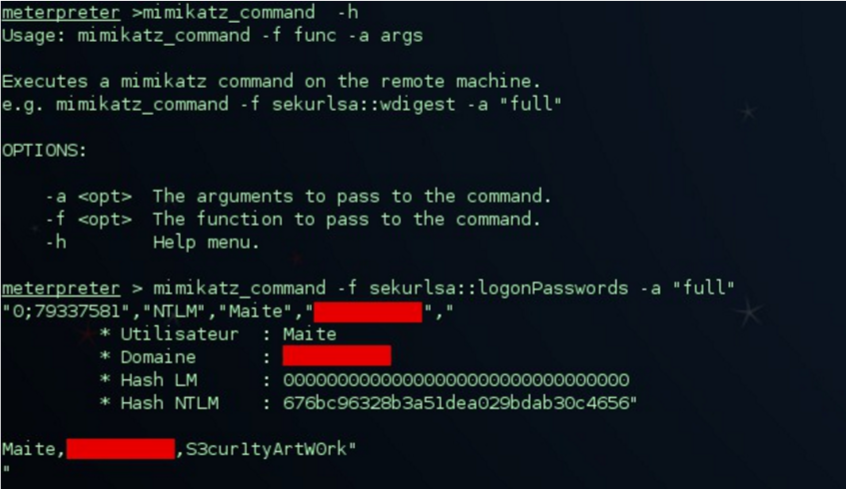
Last but not least, there is the method which this article refers to: string signatures. This method is based in another kind of signatures, different from the aforementioned kind. Instead of using HASH signatures, it uses text or binary strings that uniquely identify a malware sample. That way, even if the file has been tampered with, if it still contains those string signatures, the analysts will be able to detect and classify the malware sample.