Good hunters, how’s the hunt going?
I hope you have had time to play with your lab and feel more and more comfortable consulting and analyzing the data.
As I said in the previous article, now it’s time to get down into the mud and start understanding what is happening in our laboratory. In this case we are going to talk about the creation of processes, what happens when a process is created, what ways there are to create them and the traces that creation leaves behind.
Understanding the environment
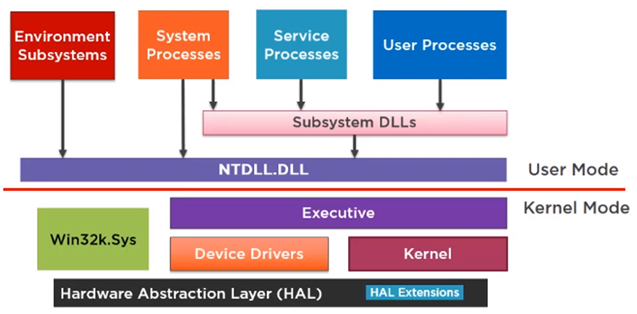
Windows is organized in layers as far as interaction with the system is concerned.
The upper layers are those with which the user or the programs that he launches interacts, the lower layers those used by the operating system itself to function.
For security reasons, the upper layers are well documented and Windows offers facilities to interact with them, but with the lower layers things change, they are not documented and due to the complexity of their operation, it is very difficult or directly not possible for security reasons.