A Darknet is a portion of network, a certain routed space of IP Addresses in which there are no active servers o services. I.e., externally no packet should be directed to that address space.
Therefore, any packet entering a Darknet should not be legitimate. It could reach it due to errors such as poor security policies or poor configuration (such as broadcast messages sent to a segment to which the issuer doesn’t belong). However, most of these packages would be associated to some action by a suspicious malware (see Responding to Zero Day Threats) or attacker who is in our network actively searching vulnerable devices.
If we install within our Darknet a server that collects, analyzes and processes the traffic entering it, it would help us to gather more information on the anomalous traffic / malware that may be circulating in the network infrastructure of our organization. This will allow us to reduce the number of false positives, detect attacks in real time and new attack trends making use of forensic analysis of the Darknet traffic.
We can monitor, among others, some strange behaviours, such as (see Aprendiendo del enemigo – Spanish) :
- Suspicious traffic grouped by ports (TCP, UDP, ICMP, etc.) or related to certain services (SSH, FTP, WEB, etc), brute force attacks against services, scanning, DoS attacks, etc..
- Specific attacks that use spoofing techniques.
- IP addresses and domains blacklisted.
- Certain patterns generated by malware (scans, increased traffic, unavailability of service, spread of worms, bots, etc.).
- Botnet identification patterns inside and outside of P2 networks.
- Possible malicious traffic to external networks
- New attack trends.
From the project “The Darknet Project” by Team Cymru, we have a couple of practical examples of anomaly detection thru monitoring traffic from a Darknet. For example, we know that there are bots that exploit open shares of Microsoft Windows 2000. A common feature of such bots is the scanning of systems listening on port 445/TCP, and looking at the monitoring tools integrated in the collector server of the Darknet we can detect whether there has been a scan to the 445/TCP. Be this confirmed, it would be a warning as packets detected within the Darknet are not legitimate.
Another practical example is about the Slammer, which performs a DoS attack to SQL servers by sending multiple files with the worm code to port 1434. One symptom of the presence of Slammer is the significant increase in network traffic through UDP port 1434 (SQL Server Resolution Service Port). Detecting this in our Darknet would be a warning about the possible presence of the worm in our network.
In short, collecting data on all traffic will allow us to analyze patterns of interest and subsequently automate the entire process through an IDS installed (e.g.) on our collector server.
Before creating a Darknet in our organization it is important to consider, among others, these two aspects:
- Define the characteristics of the network (topology, scope, visibility).
- Define hardware and software to install, taking into account what type of data we want to collect, how we want to process it (traffic capture tools, traffic analysis tools, possibility of implementing honeypots, etc.) and the financial budget we have.
Creating a Darknet
- The first step in the deployment of a Darknet is to place it in a right place, so you should choose a segment(s) of network IP addresses that will be routed to it. We recommend using an address space of at least /24 (the higher the reserved space the higher the visibility achieved).
- The next step is to reserve physical and logical space for the Darknet. As Team Cymru points, you should not put a Darknet in the same collision domain or VLAN than other subnets; the objective of the Darknet is to supply us with reliable data, so it is important to avoid “poisoning” the Darknet with legitimate traffic nor is recommended to put the IP of the Darknet publicly visible on our DNS.
The CLCERT brings a darknet proposal would be similar to the following architecture (see Diseño e implementación de una Darknet para monitoreo de la red en Chile – CLCERT – Spanish):
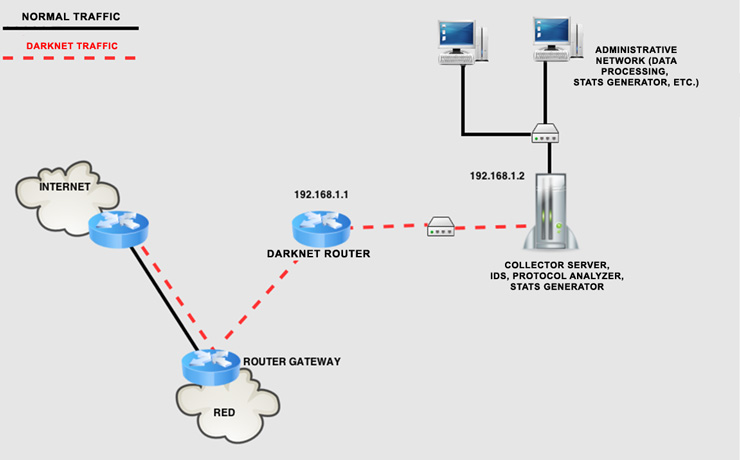
- Darknet Router : configured to forward all content that enters the Darknet. It will forward incoming traffic to the server collector of the Darknet. The router must be configured to accept only inbound traffic (traffic input) directed to Darknet, but not the inverse (output traffic). It must alert when it detects outgoing traffic from the Darknet (in this case, we have a ‘black hole’-type Darknet) since all traffic in the Darknet, as mentioned, is not legitimate. The router also must be configured for SNMP to provide traffic statistics —using tools such as MRTG— because new malware can be easily detected solely on the traffic statistics of the interface darknet.
- Collector Server: This server will be connected to the Darknet and will analyze the traffic received. It would be interesting to install an IDS, a protocol analyzer, log analysis tools, and you can even think about implementing some type of honeypot, depending the installation of these tools on the type of analysis and processing that you want to perform.
- Administrative Network: Network especially secured since it will continuously receive malicious traffic. It will also process the data received from the collector server, and generate statistics and reports on detected traffic.
In short, and since all traffic on the Darknet is potentially suspicious, it can be very useful to detect malicious traffic or device configuration anomalies in our organization.
If you are interested to pursue the subject, there are several projects related to darknets (also known as network telescopes; see Darknet y telescopios de red – Spanish) at a big scale whose main objectives are the monitoring of network traffic activity and detection of new trends in Internet:

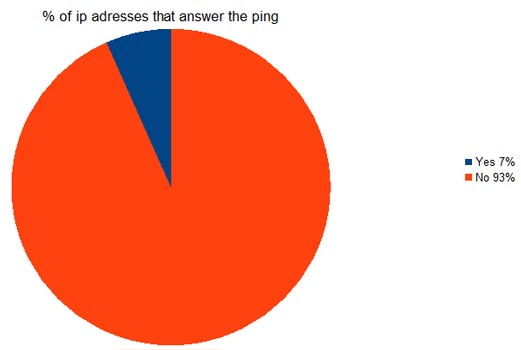
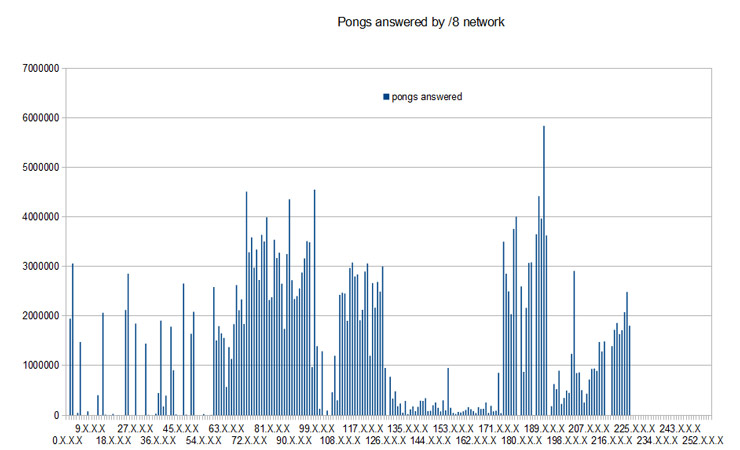
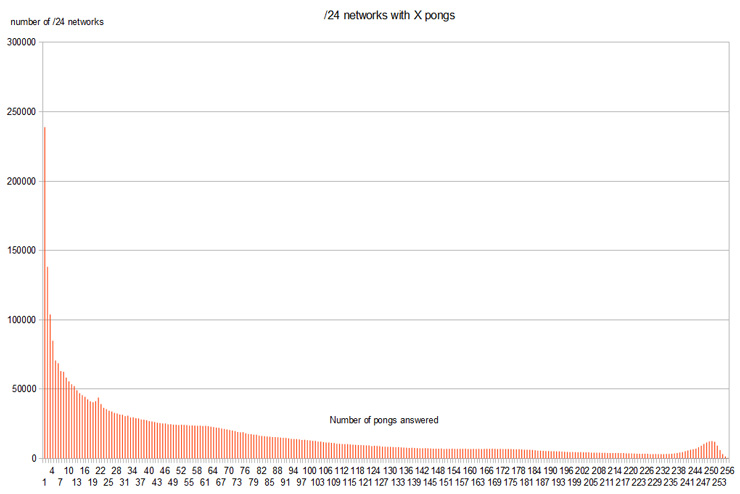
 A month ago took place in Madrid a new edition of the seminar “Recent developments in Payment Systems“. A seminar organized by “Athena Interactive”, where were discussed some of the most important aspects of payment systems currently in operation.
A month ago took place in Madrid a new edition of the seminar “Recent developments in Payment Systems“. A seminar organized by “Athena Interactive”, where were discussed some of the most important aspects of payment systems currently in operation.